A tale of VoIP Security Testing

Most of the Corporates do not focus on their internal security. They think that they are secure because their internal assets are accessible by internally. But Red Team Members know very well that How can attacker exploit internal infrastructures.
Voice over Internet Protocol (VoIP) has seen rapid implementation over the past few years. Most of the organisations which have implemented VoIP are either unaware or ignore the security issues with VoIP and its implementation. Like every other network, a VoIP network is also susceptible to abuse.
You can read more about VoIP here & SIP here.
Possible attacks against VoIP:
- Denial of Service (DoS) attacks
- Registration Manipulation and Hijacking
- Authentication attacks
- Caller ID spoofing
- Man-in-the-middle attacks
- VLAN Hopping
- Passive and Active Eavesdropping
- Spamming over Internet Telephony (SPIT)
- VoIP phishing (Vishing)

A Company gave me IP phones IP Range. Let say 192.168.71.1/24
First, I checked which clients were up (75 hosts were up) and I started NMAP on them.
I started enumeration with Viproy Framework, SIPVICIOUS. I found Clients’ IPs & SIP Server’s IP.
I gathered the information for exploitation such as firmware version, running services, etc.
I found some vulnerabilities so now I am going to talk about them.
- Admin Password Reset
This Vulnerability is due to the version of Grandstream GXP 1625 (i.e., Version — 1.0.4.128). It has a security issue which helps the attacker to reset admin’s password. After that attacker can gain the access in dashboard.
CVE References : CVE-2018–17564
Impact:
- Attacker can change the configuration.
- Attacker can make himself as an another user. Suppose, Attacker changes his phone extension to CTO’s Phone Extension and vice versa.
- Attacker can make a call on the behalf of other user.




2. Privilege Escalation
Privilege escalation is the act of exploiting a bug, design flaw or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user.
CVE References: CVE-2018–17565
Impact:
- Attacker can run the malicious/arbitrary command as a Root user.
- Attacker can change the configurations.

3. Denial of Service
DoS attacks can result in damage such as preventing outgoing and incoming calls. Always consult with your client performing Denial-of-Service attacks as they are destructive in nature.

4. Caller ID Spoofing
Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source. Spoofing can apply to emails, phone calls, and websites, or can be more technical, such as a computer spoofing an IP address, Address Resolution Protocol (ARP), or Domain Name System (DNS) server.
Note: Voicemail spoofing is possible due to unencrypted communications allowing us to manipulate the parameters in the INVITE request to impersonate anyone we like.
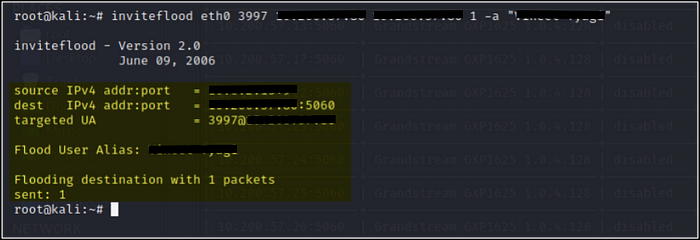

Other Attacks were intercept Voice Call & Registration Manipulation and Hijacking.
Note: You can do intercept voice call using wireshark after ARP Spoofing.
Conclusion
Number of security threats exist related to VoIP. Using enumeration, crucial information regarding VoIP network, user Ids/extensions, phone types etc can be obtained.With use of specific tools, it is possible to attack authentication, hijack VoIP calls, eavesdrop, and call manipulation, VoIP spamming, VoIP phishing and IP-PBX server compromise.
Resources
https://media.blackhat.com/us-13/Arsenal/us-13-Ozavci-Vipray-VoIP-Pen-Test-Kit-Slides.pdf
https://sourceforge.net/projects/vgiphopper/files/
https://github.com/alyssaong1/VolPBot
Hope, You enjoyed it.
If you like it then clap and share it. You can find me on Twitter.









