Member-only story
Abusing NTLM Relay and Pass-The-Hash for Admin
With the rise of PetitPotam recently, I was inspired to do a bit more research into NTLM Relaying as a whole. So I spent a while reading through different techniques and managed to combine two ideas that I had seen often, Responder/NTLMRelayx and Pass-The-Hash on some of my work engagements to significant effect. These techniques have been known for years, but still see use inside environments that have not implemented strong network security.
For experienced pentesters, this probably isn’t anything groundbreaking or new, but I hadn’t seen a complete attack chain like this post anywhere else, so I figured I might as well write it up.
Note: All the examples below are on a personal test domain, so yes, the passwords are easily crackable for this example.
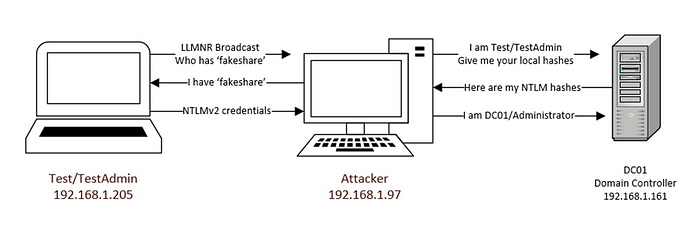
NTLM Relaying
Before diving into the technical details, let’s review NTLM Relaying and outline the conditions necessary for exploitation. Windows New Technology Lan Manager (NTLM) is a suite of security protocols offered by Microsoft to authenticate and authorize users on Windows computers. NTLM is a challenge/response style protocol whereby the result is a Net-NTLMv1 or v2 Hash. This hash is relatively low-resource to crack, but when strong security policies of random, long passwords are followed, it holds up well. However, Net-NTLM hashes can not be used for Pass-The-Hash (PTH) attacks, only the local NTLM hashes on the victim machine itself.
To get around this, we capture the Net-NTLM hashes in a SOCKS server relay and use this authentication to pull the local NTLM hashes from a machine. With these hashes in hand, we can then proceed down the standard PTH attack path. For PTH, I will showcase 3 different methods of using NTLM hashes and explain why one might be helpful over another one, based on real-world engagements, including avoiding anti-virus.
For more technical dive into the different Windows authentication protocols, I recommend reading https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4, an excellent write-up on the differing pieces.
Prerequisites
- Layer 2 access to the Local Area Network
- Impacket installed on Linux (preferably Kali since it comes…

