Member-only story
🔥 Advanced Bug Bounty $$$$: API Key and Token Leaks — Tools, Techniques, and Exploitation

Disclaimer: This document is for educational purposes only. Exploiting systems without authorization is illegal and punishable by law.
Stay ethical. Stay legal. Secure responsibly.
Thanks, Everyone for reading. Enjoy Happy Ethical Hacking!
Support me if you like my work!
✅ 📌 Introduction
API keys, access tokens, and secrets are the crown jewels of bug bounty hunting. When leaked, they can lead to unauthorized access, data breaches, and full system compromise. As a bug bounty hunter, discovering and exploiting these leaks can result in high-severity reports and significant bounties.
In this blog, I’ll cover 8 powerful tools used by professional bug bounty hunters to:
- Detect, validate, and exploit leaked API keys and tokens
- Automate key spraying against multiple services
- Perform large-scale enumeration and verification
I’ll provide clear installation steps, usage examples, and pro tips to help you maximize your efficiency during bug bounties.
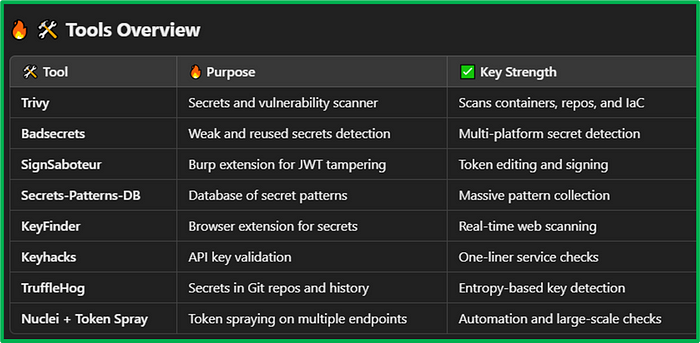
🔥 1. Trivy — Secrets and Vulnerability Scanner
Trivy by Aquasecurity is a versatile scanner used for detecting API keys, tokens, and secrets in file systems, containers, and repositories. It also scans for vulnerabilities and misconfigurations, making it a must-have for bug hunters.
✅ Key Features:
- Secrets Detection: Finds leaked tokens, API keys, and credentials.
- Container and Repo Scanning: Scans Docker images, GitHub repos, and file systems.
- Misconfiguration Alerts: Identifies weak configurations in cloud infrastructure.
🛠️ Installation:
# Install Trivy on Ubuntu
sudo apt install trivy
