Angler Exploitation Kit Infection 2 — Malware Traffic Analysis

In this article, I use Network Miner, Wireshark, and Brim to analyze a PCAP file that captured network traffic belonging to an Angler exploitation kit infection. The PCAP file belongs to a blue team-focused challenge on the CyberDefenders website, titled “Malware Traffic Analysis 4” and was created by Brad Duncan.
Disclaimer
I like to add a brief disclaimer before a writeup to encourage people to attempt the challenge before reading this article since there will obviously be spoilers in this writeup. I believe you will enjoy the challenge more if you attempt it yourself first and then come back to this writeup if you get stuck or need a hint. So without any further delay, let's get started!
Challenge Questions
1. What is the victim IP address?
2. What is the victim’s hostname?
In NetworkMiner under the hosts tab, I can see two private internal networks, both of which contain a windows machine.


In Wireshark, I can navigate to “Statistics > Endpoints > IPv4 Tab” and order the IP’s based on the number of packets. I can see that there is a lot of traffic for Turkey-Tom’s Windows machine.

Based on the information above, we can assume that Turkey-Tom’s Windows machine is the infected host, but the deeper investigation is required to confirm this.
3. What is the exploit kit name?
In Wireshark, we can navigate to “Statistics > Conversations > TCP Tab” and order the conversations based on the number of packets. I can see that the top conversation was between Turkey-Tom’s Windows machine and the IP highlighted below.
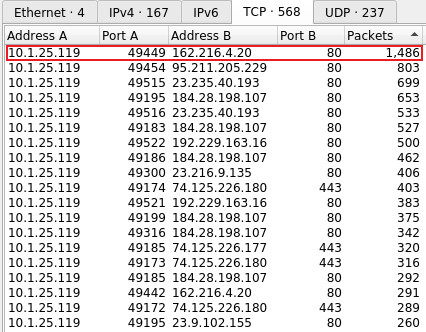
In NetworkMiner, I can see the details for the IP address.

I can see that the conversation took place over port 80, so I decided to look at what HTTP objects related to the IP addressee's FQDN could be exported from Wireshark.

If we export these HTTP objects and upload them to VirusTotal, we can see that two are marked as malicious.


In VirusTotal, we can see that some of the security vendors have identified the malicious files as being related to Angler EK. In AlienVault, we can also see that the IP address of the web server from where these malicious files were retrieved is an network IoC for Angler EK. Finally, in Brim we can see the Bedep payload, a malware downloader that is exclusive to Angler.
According to MalwareBytes:
Trojan.Bedep opens a backdoor on infected systems and can download additional malware to the system.
This Trojan is usually dropped on the affected systems by exploit kits.
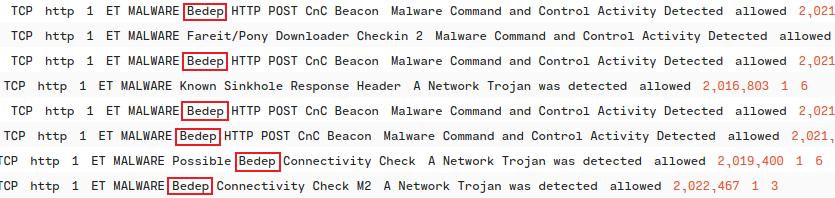
4. What is the IP address that served the exploit?
As we have already seen earlier above, the IP address that served the exploit can be found in NetworkMiner.

5. What is the HTTP header that is used to indicate the flash version?
In Wireshark, we can view the HTTP GET request used to download the malicious flash file and see the header that is used to indicate the flash version.

6. What is the malicious URL that redirects to the server serving the exploit?
In Wireshark, we can view the HTTP stream of the malicious HTML file that contains embedded JS code. Here, we can see the malicious URL that redirects to the server serving the exploit.

7. What is The CAPEC ID corresponding to the technique used to redirect the victim to the exploit server? More info at capec.mitre.org
To identify what technique was used to redirect the victim to the exploit server, we need to retrace the timeline of events for the infection using Wireshark. Looking at the image above for question 6, we can see the website the victim visited from in order to reach the server serving the exploit. In Wireshark, we can view the HTTP stream for the malicious redirect URL.

We can see that an iFrame overlay attack is used to redirect the victim to the exploit landing page. We can perform a quick search on Google to find the corresponding CAPEC ID for this attack (i.e. CAPEC-222: iFrame Overlay).
8. What is the FQDN of the compromised website?
9. The compromised website contains a malicious js that redirect the user to another website. What is the variable name passed to the “document.write” function?
Still retracing our steps in Wireshark, we can see in the image above for question 7 the website that the victim visited from based on the referrer request header value. Looking at the HTTP objects for this website, I can see a JS code object.

In Wireshark, we can view the HTTP stream for this website and the JavaScript Code. Reviewing the code, we can see the malicious URL that redirects to the server serving the exploit and the variable name passed to the “document.write” function.

10. What is the Compilation Timestamp of the malware found on the machine? Format: YYYY-MM-DD hh:mm:ss
After spending sometime trying to solve this question, I was not able to find the solution.
Closing Remarks
I found this challenge was great for practicing with NetworkMiner, Brim and Wireshark. I also really enjoyed working through this PCAP challenge file and understanding how the Angler exploitation kit infected the Windows VM. Thank you for reading till the end and keep hacking 😄!

