Modern Binary
Exploitation Writeups 0x01
This is the 1st writeup of Tools and Basic Reverse Engineering by RPISEC, a subpart of the Modern Binary Exploitation Course.
Link of lectures:- http://security.cs.rpi.edu/courses/binexp-spring2015/
All the lecture materials and other necessary files are available on the above link to check it out.
_________________________________________________ Next WriteUp ➡️
crackme0x00a
Information gathering using the file command
$file crackme0x00a
- The file is 32-bit, LSB executable (least-significant byte).
- It means the file is a little-endian.

Information gathering using the rabin2 tool.
$rabin2 -I crackme0x00a

Cracking the file using strings
$strings crackme00x0a


Cracking the file using xxd

$xxd crackme0x00a

Cracking the file using rabin2



Cracking the file using ltracre
$ltrace ./crackme0x00a
ltrace basically intercepts and print the system calls executed by the program.

Cracking the file using strace :(
strace ./crackme0x00a
strace is used for tracing syscalls. It won’t ever trace a string compare like strncmp as that doesn’t require any syscalls.
Cracking the file using radare2
$radare2 crackme0x00a
[0x08048430]> aaa
[0x08048430]> pdf @ main- aa:-analyze all.
- aaa:- analyze all with more info.
- pdf:- print disassemble function.


radare2 give the view of the code.
- There is *s2 char type pointer which is pointing some strings i.e our input(password). *s1 is “g00dJ0B!”,in the next step both getting compared using strcmp.

Cracking the file using gdb-peda
gdb-peda is like an addon for gdb, you can install it from GitHub.
$gdb crackme0x00a
>gdb-peda$ disassemble mainThe disassemble main will show the main function of the binary.
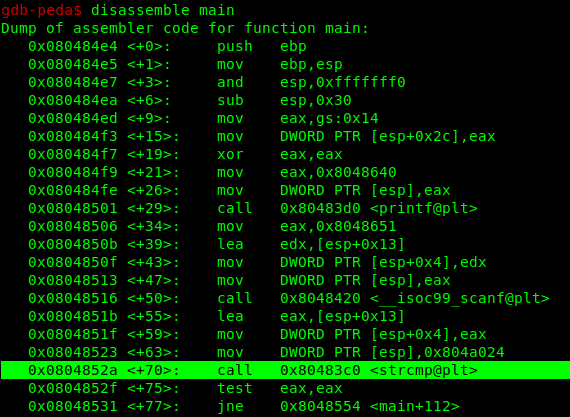
There is an strcmp instruction on <+70>, so lets set the breakpoint at the location and run the program.
gdb-peda$ break *0x0804852a
gdb-peda$ runEnter the password to test the program, in this case, I enter incognito as a password.
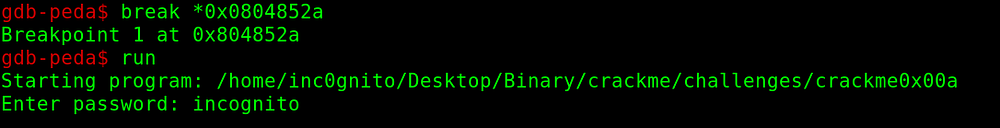

“incognito” is compared with the “g00dj0B!”, gdb-peda also shows some guess arguments.












