Modern Binary
Exploitation Writeups-0x04
This is the 4th writeup of Tools and Basic Reverse Engineering by RPISEC, a subpart of Modern Binary Exploitation Course.
Link of lectures:- http://security.cs.rpi.edu/courses/binexp-spring2015/
All the lecture materials and other necessary files are available on the above link to check it out.
⬅️ Previous writeup__________________________________ Next WriteUp
crackme0x02
$ ./crackme0x02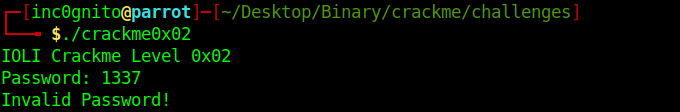
Information gathering using the rabin2 tool.
rabin2 -I crackme0x02

Cracking using radare2
radare2 crackme0x02
[0x08048330]> aaa
[0x08048330]> pdf @ main- aa:- analyze all.
- aaa:- analyze all with more info.
- pdf:- print disassemble function.

[0x08048330]> drdr:- prints the data register with values.

It shows the eax with ‘0’ which is not right it must contain some value. radare2 analysis the binary in the static mode so we have to use radare2 debug mode so that we can set the breakpoint in between the program and find out more.
Cracking using radare2 debug mode
$radare2 -d crackme0x02
- aa:- analyze all.
- aaa:- analyze all with more info.
- pdf:- print disassemble function.


At address ‘0x0804844e’ there is cmp instruction so lets set the breakpoint there.

- db flag:- place a breakpoint at a flag, where the flag can be either an address or a function name.
- dc :- run the program.
cmp eax, dword [local_ch], Now let’s try to find out the value of $eax register and local_0xc.
Finding the value of eax.
[0x0804844e]> ? eax
There is one more way to get the value of eax register.
[0x0804844e]> dr eax
[0x0804844e]> ? 0x00000539- dr flag:- prints the data register value.

Finding the value of local_ch.
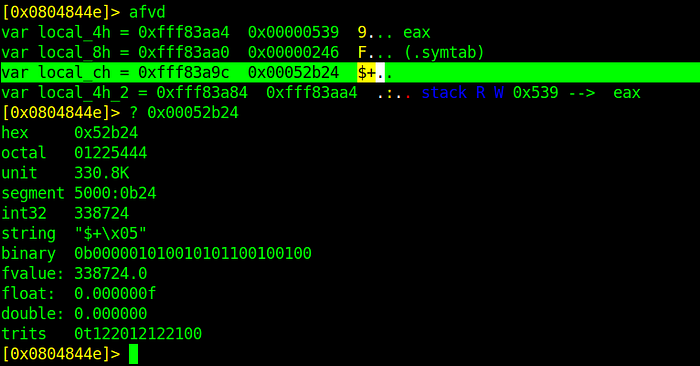
[0x0804844e]> afvd local_ch
[0x0804844e]> pxr $w @ebp-0xc
[0x0804844e]> ? 0x00052b24- afvd:- afvd name output r2 command for displaying the value of args/locals in the debugger.

Another way of finding the value of local_ch.
[0x0804844e]> afvd
[0x0804844e]> ? 0x00052b24- afvd:- afvd name output r2 command for displaying the value of args/locals in the debugger.

Cracking using gdb
$gdb crackme0x02
gdb-peda$ disassemble main
gdb-peda$ break *0x0804844e

cmp eax,DWORD PTR [ebp-0xc]
- eax:- eax register contains 0x539, 0x shows that it’s in hex.
- DWORD:- It refers to the double word, doubleword is 32 bit or 4 bytes(8 bit =1 byte).
- PTR:- Abbreviation of Pointer.
- ebp-0xc:- 0xc(12 in decimal) is subtracted from ebp(Base pointer).
So in this instruction eax is compared to the word(number) which is stored in the address ebp-0xc.
Let’s find out what is stored in eax and ebp-0xc.
From the above image, eax show the value 0x539
p/d 0x539- p:- print command (abbreviated p).
- d:- Print as an integer in signed decimal.

1337 is stored in the $eax, which we give as an input.
gdb-peda$ x/x $ebp-0xc
0xffffd1ec: 0x00052b24
gdb-peda$ p/d 0x00052b24
$9 = 338724x command is used to eXamine.
- /x:- prints address $ebp and the contents at that address in hex.
p command is used to Print.
- /d:-print contents as a decimal.

$./crackme0x02
Converting ‘0x00052b24’ using python
python -c "print 0x00052b24"
Converting ‘0x00052b24’ using rax2
rax2 0x00052b24











