#BugBounty — How I was able to delete anyone’s account in an Online Car Rental Company
Hi Guys,
One more interesting finding that I recently discovered in a popular online car rental company. Some parameter manipulation combined with CSRF resulted into disabling account of any user. Let’s see how it was done —
So it comes to me as surprise, I was going through “Update Profile” functionality to find some bug and then I saw something fishy in the request. Parameter “method” :)
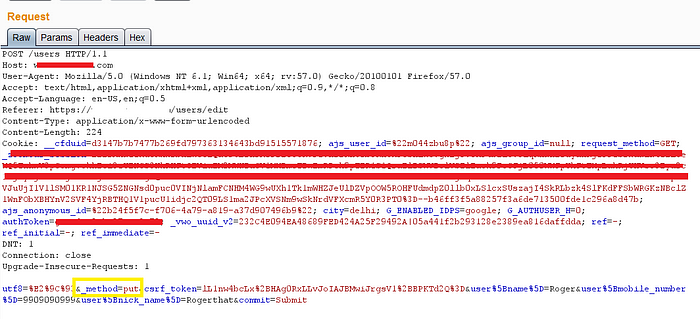
The original value going in the “method” parameter was “put” which suggest creating a new resource or replaces a representation of current resource with the requested data and then I knew what to do next — I just changed that value to method “delete” (HTTP DELETE request method deletes the specified resource) and forwarded it. As expected , account was gone,it was deleted! (and in actual there was no such functionality in the portal which allow user to deactivate his account) .
Now the next challenge was to do the same thing but to other user’s account . I tried , searched, dig into various areas but all was going into vain then I tried the most basic thing- CSRF . If you notice the above request, you will find “csrf_token” going in the post body. Just to check whether the token was getting validated or not , I removed the token value and forwarded the request and I got “200 OK”. Whoaa!
Below is the CSRF exploit-

And on some more analysis, I came across that this was the only form where CSRF token was not getting validated- Most common case of weak CSRF implementation. :)
Report details-
08-Dec-2017 — Bug reported to the concerned company.
29-Dec-2017 — Bug was marked fixed.
01-Jan-2018 — Re-tested and confirmed the fix.
07-Jan-2018 — Awarded by company.
Thanks for reading!
~Logicbomb (https://twitter.com/logicbomb_1)

