Bypass the Firewall with SSH Tunnelling
a guide to make an SSH tunnel for accessing blocked port over port 22

Do you work for a company?
You have a problem with their firewall?
Or are you a hacker who making the netcat listener in your local computer?
This article fit for you. Because today I will explain you how making an ssh tunnel for accessing blocked port over port 22.
Port 22 by default use to ssh connection, and almost every company have allowed this port in their firewall.
Dummy Scenario
In this scenario, I wanna make a firewall rule to block facebook.com in my Windows Machine. This is an prove of concept that we will bypass the firewall with ssh tunnel.
My firewall settings
Firstly, collect the Facebook’s IP with nslookup command.

Then I am creating a new outbound rule in the firewall for specific blocking the facebook.com


My Working Laptop (Windows) — Before SSH Tunnel
Because the firewall block access to facebook.com, so when I try to connect with browser, and this is my browser respond:

Bypass Firewall
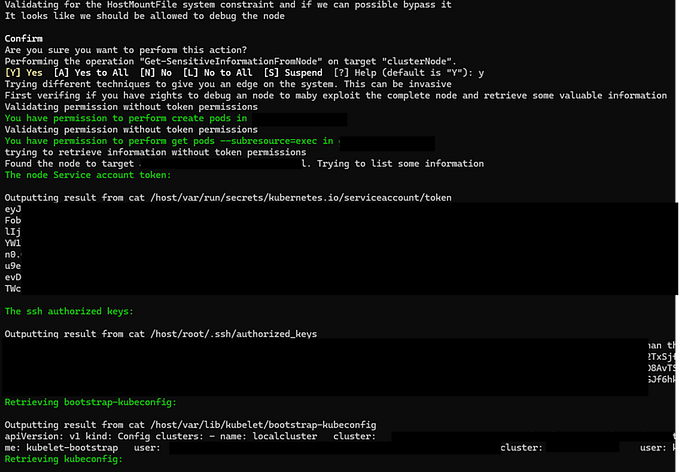
At the beginning, I am setting the sshd_config on the Ubuntu Server.
My Server (Ubuntu Server)
Make sure that in the file /etc/ssh/sshd_config have this configuration:
AllowTcpForwarding yes
GatewayPorts yes
After that restart the sshd service, for making sure that the config applied.
sudo service sshd restartMy Working Laptop (Windows) — After SSH Tunnel
Step number 1 on the windows machine, create an ssh tunnel:
ssh -N -D user@ip-server
Note:
-N → without login in to the server
-D →dynamic tunneling
8181 → is the port binding in the localhost to any port in the 192.168.0.113
The next step is setting your proxy like this,

And congratulation, your proxy server with ssh tunneling works and you bypass the firewall.
Demo

Conclusion
Firewall is not a one of the security tools for make sure your company is secure. Make a combination with some security tools and make the attacker in trouble.
Thanks for reading.