Bypassing rate limit abusing misconfiguration rules

Hello Friends,
This time I’ll share with you how I was able to bypass rate limit implemented on all forms in a private program so let’s get started :)
A little bit about Rate Limit:
A rate limiting algorithm is used to check if the user session (or IP-address) has to be limited based on the information in the session cache.
In case a client made too many requests within a given timeframe, HTTP-Servers can respond with status code429: Too Many Requests.

Discovery Phase:
In the discovery process I noticed that all application functions were protected by rate limit, so I started thinking about how to ignore this algorithm implemented by the company, because once ignored, I could perform brute force attacks on multiple application functions, such as:
- Create multiple users through brute force
- Bruteforce attacks on Sign In page
- 2FA bypass (unfortunately the application did not implement 2FA methods)
First attempt:
Trigger rate limit algorithm purposefully and then change my IP. When performing such test, I was able to send 4 more requests, after that, I was blocked again.
Did you notice anything?
With this test, I got a sense that rate limit rule was being implemented by IP. I was able to identify that every 4 Requests the IP was blocked. We can now assume that the application is constantly checking how many requests we make through our remote IP.
Interesting…
I immediately thought of a second possibility: A common error in implementing a rate-limit rule is that sometimes the rule is created to block brute force attacks from remote Ips with the exception of IP 127.0.0.1 (localhost)
Second attempt:
Add to HTTP Request Header X-Remote-IP: 127.0.0.1
And … Rate Limit Bypass successfully completed!
Attack Scenarios:
This opened up several possibilities such as: Perform brute force on login page (which was protected with rate limit)
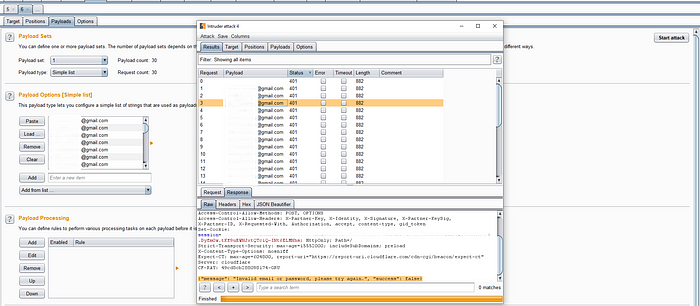
Perform password change spam:


If the application had two-factor authentication, we could also perform this attack on users password, but unfortunately there was no such mechanism enabled :(
Tips:
There’s a Burp Suite extension that automatically inserts the bypass headers into all your HTTP requests, you can find it here
It’s a way for you to perform burp intruder attacks without having to manually insert headers in every request you make. The attack would look like this:

Finally, I would like to thank the whole bug bounty community, it’s always a great pleasure to learn with all of you :)
Hope you liked it!
Find me here.

