Member-only story
Cache Control: An Easy P4 Vulnerability
Introduction
Hello, fellow hackers! Today, I’ll walk you through how to identify a simple yet impactful P4 vulnerability — improper cache control. This is a widely overlooked issue that can lead to user data leakage, unauthorized access, and even session hijacking in certain cases. Let’s dive in!
What is Cache Control?
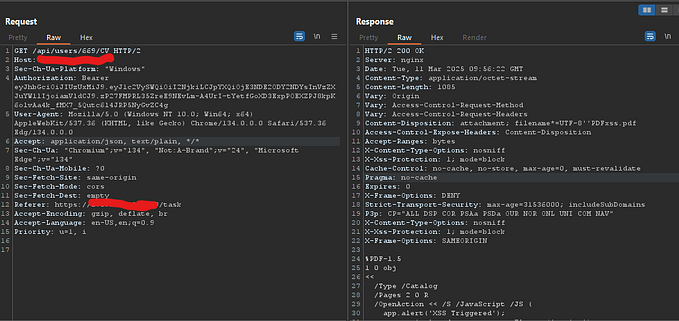
Web applications use cache control headers to manage how browsers and proxies store and serve content. A properly configured cache control mechanism prevents sensitive pages from being stored in a way that could be accessed by unauthorized users. When misconfigured, it can allow sensitive information to be cached and retrieved by unintended parties.
Example Target: apps.target.com/accounts
Let’s assume the application we are testing is apps.target.com/accounts, which handles user accounts and contains sensitive data.
How to Identify the Vulnerability
Step 1: Checking Cache Headers
The first step is to analyze the cache control headers returned by the server. You can use browser developer tools or cURL to inspect them:
Using cURL:
curl -I https://apps.target.com/accounts