Cheat Sheet for Path Traversal Payloads
Alright, fellow bug hunters! Today, we’re diving into the intriguing world of Path Traversal Vulnerability. Path Traversal is a sneaky vulnerability that lets hackers navigate through directories they shouldn’t access. But fear not, I’ve got your back! I’ve compiled some awesome resources to help you grasp the concept and understand it (and exploit it) like a pro.
Don’t forget to save this post (or check out the corresponding GitHub repo) for future reference. Oh, and be sure to hit that follow button to stay in the loop with my latest learnings and findings!
If you’re already familiar with how the web works and have some Linux filesystem know-how, you’re in for a treat!

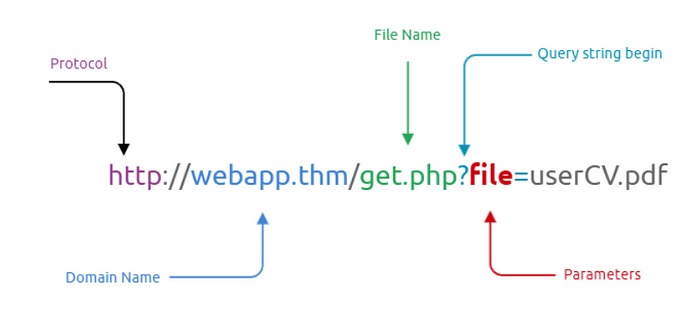
Alright, so what is mean by path traversing? Imagine a website URL, and it’s made up of various elements (check out the figure below). We won’t dive too deep into it, assuming you all got the basics of “how the web works.” 😉 No worries; we’ll keep it simple for everyone!
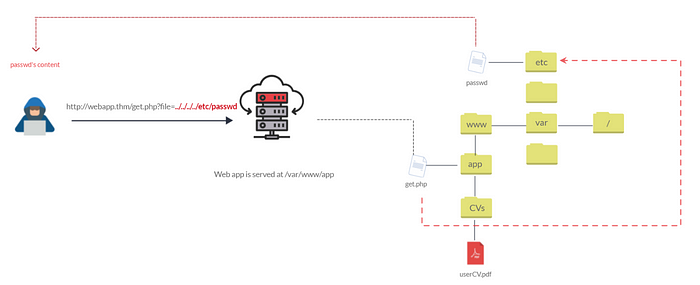
You’re trying to fetch your CV, userCV.pdf, from a webserver. So, you shoot a HTTP request to the server asking for the same. Now, here’s where things get sneaky. Instead of just asking for your CV, a clever hacker can sneakily mess with the request and try to access other files or directories on the server. It’s like taking a shortcut up the path and peeking into places you shouldn’t.
A path traversal vulnerability is also called directory traversal or zip slip vulnerability (or dot-dot-slash attack).
Here’s the deal: Imagine the user’s input gets passed to a function without being checked or sanitized. The hacker takes advantage of this and tries to play around with the webserver. They can thus access the operating system resources, like local files on the server.
To test for the sneaky vulnerability we talked about, we can tinker with the URL parameter and see how the web app reacts. We move up the directory using double dots and a slash (../). Now, when we find an entry point (like this one: http://webapp.thm/get.php?file=userCV.pdf), we can try something wild, like: http://webapp.thm/get.php?file=../../../../etc/passwd. Guess what? The web app sends back the file’s content in the response!
I will provide few resources to learn about this vulnerability if you are not familiar!
Directory Traversal — PortSwigger
What is Directory Traversal ? — Intigriti
TryHackMe room — File Inclusion
You can further learn more about LFI and RFI from this Medium post by a fellow writer, which I found to be really useful :)
Some web apps might have put up a little defense by handling input validation and sanitization — but don’t be fooled, it’s not always foolproof! That means the direct payload like “../../../../etc/passwd” won’t always do the trick. So, the plan is to keep testing, of course! Load up the web app with tons of payloads until you find the perfect match! It’s like unlocking a secret code — you just gotta try until you hit it off with the right one!
Path Traversal Cheat Sheet
Just to make all our lives easier, I have compiled a list of payloads from several sources . Check out my GitHub repo — PathTraversal-Cheat-Sheet. It’s packed with different payloads from various sources, ready to be used in your Burp Suite Intruder! Whether you’re dealing with Linux or Windows, I’ve got you covered! Just load up the payloads and fire away until you hit it off.
Remember, we’re hacking ethically here! No messing with real stuff without permission!
To summarize, path traversal is a dangerous web vulnerability if not handled properly. By taking appropriate measures for user input validation and sanitization, we can keep the hackers at bay.
Alright, play safe, always test with permission, and keep exploring those vulnerabilities! Go ahead and make the web safer, one payload at a time! Happy hacking :D
You can buy me a coffee here https://www.buymeacoffee.com/suprajabask

