Cracking Hashes with HashCat
Hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 300 highly-optimized hashing algorithms. hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and macOS, and has facilities to help enable distributed password cracking.

Here we will be looking into how to crack passwords from below mentioned Generic Hash types, via HashCat:
1. MD5 Hashes
2. Salted MD5 Hashes
3. MD5Crypt Digests
4. a) HMAC-SHA1 key
4. b) SHA-1 Digests
5. SHA-2 Digests
6. SHA-3 Digests
7. NTLM Hashes
8. CRC32 Hashes
HashCat supports the following attack modes:
1. Straight *
2. Combination
3. Brute-force
4. Hybrid dict + mask
5. Hybrid mask + dict
* accept Rules
Use the below command to check out all the available options:hashcat -h
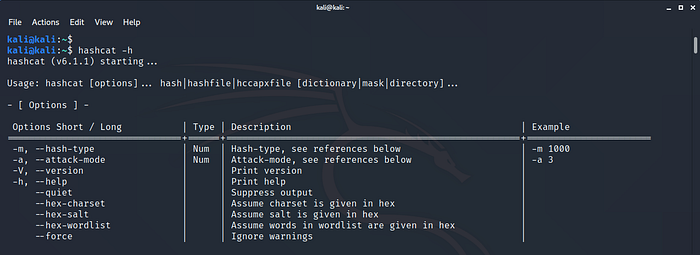
In this module, we will be trying dictionary-based & brute-force attacks.
1. MD5 Hashes
Make sure the input hashes are in hashcat compliant format as shown in the example.
Example: 8743b52063cd84097a65d1633f5c74f5 >hash.txt
Use Command:hashcat -m 0 -a 0 hash.txt passwordlist.txt
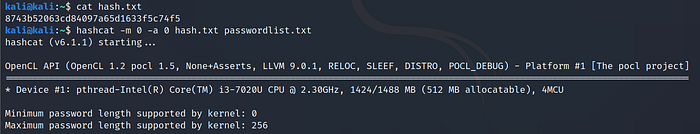
where,
-m 0: MD5 hash mode
-a 0: Dictionary attack mode
hash.txt: txt file containing hash in a compliant format
passwordlist.txt: dictionary file containing passwords in plain text
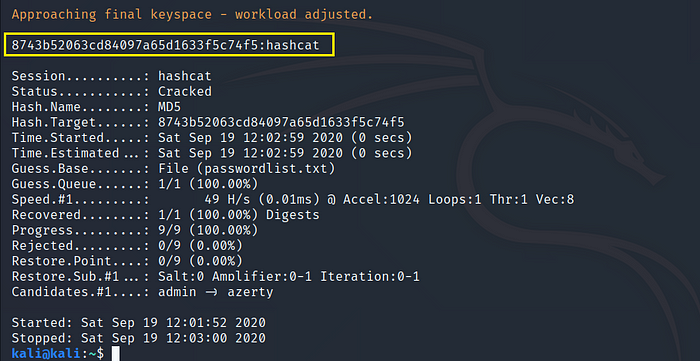
Cracked Hash: 8743b52063cd84097a65d1633f5c74f5 = hashcat
2. Salted MD5 Hashes
Make sure the input hashes are in hashcat compliant format as shown in the example.
Example: md5($pass.$salt) : 01dfae6e5d4d90d9892622325959afbe:7050461 >hash.txt
Use Command:hashcat -m10 -a0 hash.txt passwordlist.txt
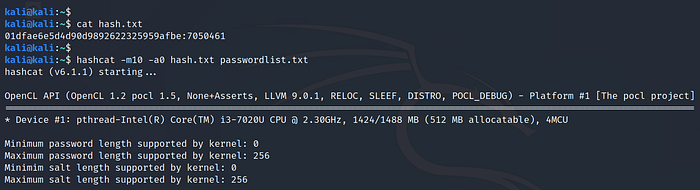
where,
-m 10: Salted MD5 hash mode
-a 0 : Dictionary attack mode
hash.txt : txt file containing hash in compliant format
passwordlist.txt : dictionary file containing passwords in plain text
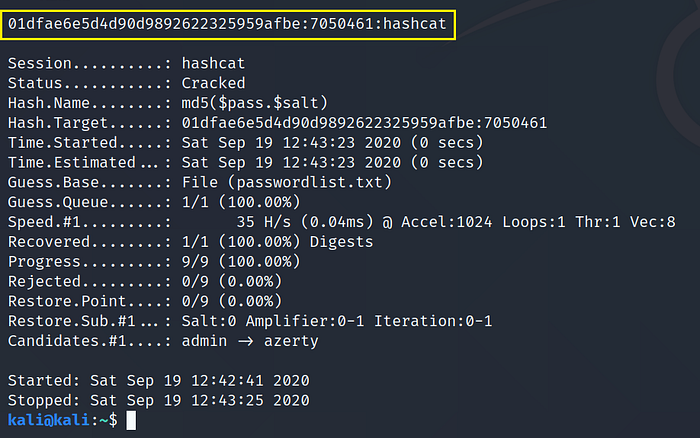
Cracked Hash: 01dfae6e5d4d90d9892622325959afbe:7050461 = hashcat
3. MD5Crypt Digests
Make sure the input hashes are in hashcat compliant format as shown in the example.
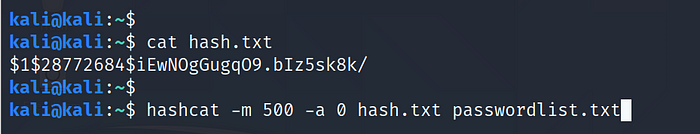
Example: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) $1$28772684$iEwNOgGugqO9.bIz5sk8k/ >hash.txt
Use Command:hashcat -m 500 -a 0 hash.txt passwordlist.txt
where,
-m 500: MD5Crypt Digests hash mode
-a 0: Dictionary attack mode
hash.txt: txt file containing hash in a compliant format
passwordlist.txt: dictionary file containing passwords in plain text
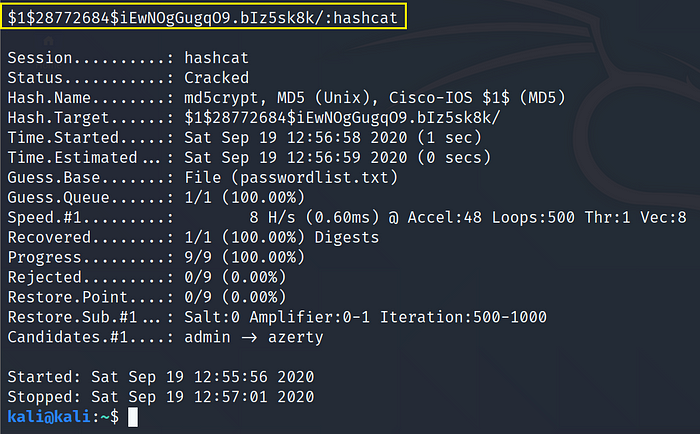
Cracked Hash: $1$28772684$iEwNOgGugqO9.bIz5sk8k/ = hashcat
4. a) HMAC-SHA1 key
Make sure the input hashes are in hashcat compliant format as shown in the example.
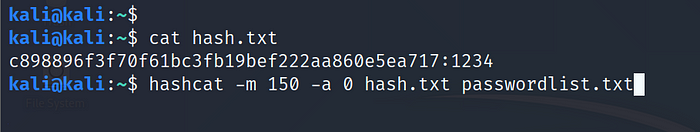
Example: HMAC-SHA1 (key = $pass) c898896f3f70f61bc3fb19bef222aa860e5ea717:1234 >hash.txt
Use Command:hashcat -m150 -a 0 hash.txt passwordlist.txt
where,
-m 150: HMAC-SHA1 key hash mode
-a 0: Dictionary attack mode
hash.txt: txt file containing hash in a compliant format
passwordlist.txt: dictionary file containing passwords in plain text
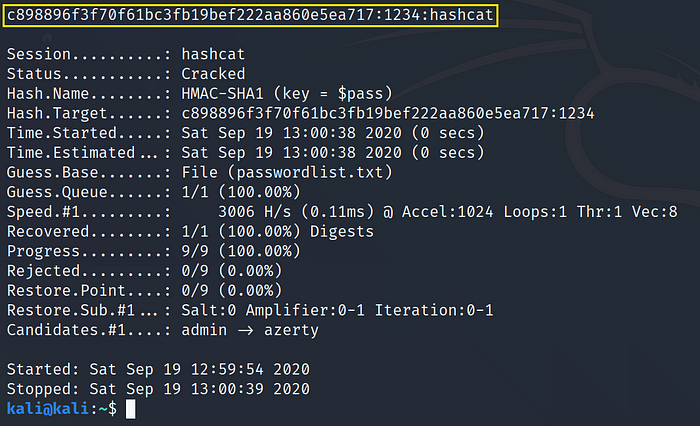
Cracked Hash: c898896f3f70f61bc3fb19bef222aa860e5ea717:1234 = hashcat
b) SHA-1 Digests
Make sure the input hashes are in hashcat compliant format as shown in the example.
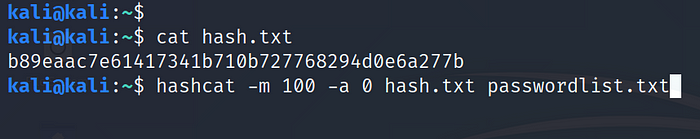
Example: b89eaac7e61417341b710b727768294d0e6a277b >hash.txt
Use Command:hashcat -m100 -a 0 hash.txt passwordlist.txt
where,
-m 100: SHA1 digest hash mode
-a 0: Dictionary attack mode
hash.txt: txt file containing hash in a compliant format
passwordlist.txt: dictionary file containing passwords in plain text
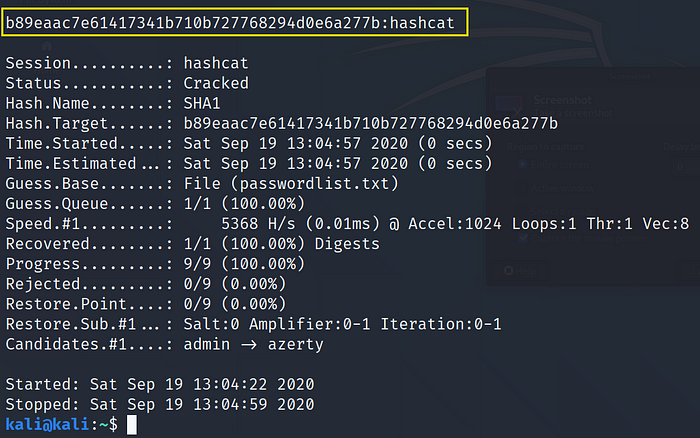
Cracked Hash: b89eaac7e61417341b710b727768294d0e6a277b = hashcat
5. SHA2–384 Hash
Make sure the input hashes are in hashcat compliant format as shown in the example.
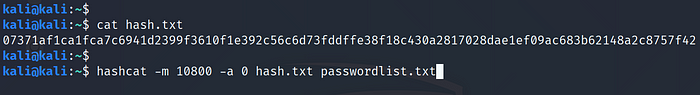
Example: SHA2-384 07371af1ca1fca7c6941d2399f3610f1e392c56c6d73fddffe38f18c430a2817028dae1ef09ac683b62148a2c8757f42 >hash.txt
Use Command:hashcat -m 10800 -a 0 hash.txt passwordlist.txt
where,
-m 10800: SHA-2 Digests hash mode
-a 0 : Dictionary attack mode
hash.txt : txt file containing hash in compliant format
passwordlist.txt : dictionary file containing passwords in plain text
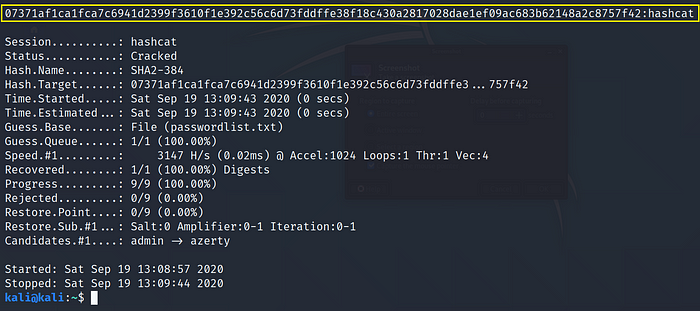
Cracked Hash: 07371af1ca1fca7c6941d2399f3610f1e392c56c6d73fddffe38f18c430a2817028dae1ef09ac683b62148a2c8757f42 = hashcat
6. SHA3–512 Hash
Make sure the input hashes are in hashcat compliant format as shown in the example.
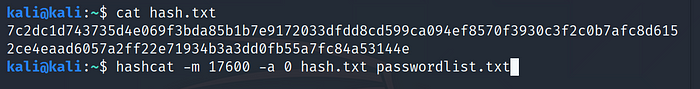
Example: SHA3–512 7c2dc1d743735d4e069f3bda85b1b7e9172033dfdd8cd599ca094ef8570f3930c3f2c0b7afc8d6152ce4eaad6057a2ff22e71934b3a3dd0fb55a7fc84a53144e >hash.txt
Use Command:hashcat -m 17600 -a 0 hash.txt passwordlist.txt
where,
-m 17600: SHA3–512 hash mode
-a 0 : Dictionary attack mode
hash.txt : txt file containing hash in compliant format
passwordlist.txt : dictionary file containing passwords in plain text
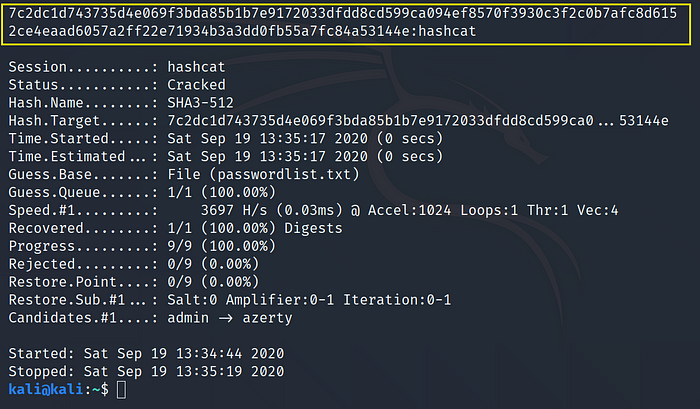
Cracked Hash: 7c2dc1d743735d4e069f3bda85b1b7e9172033dfdd8cd599ca094ef8570f3930c3f2c0b7afc8d6152ce4eaad6057a2ff22e71934b3a3dd0fb55a7fc84a53144e = hashcat
7. NTLM Hashes
Make sure the input hashes are in hashcat compliant format as shown in the example.
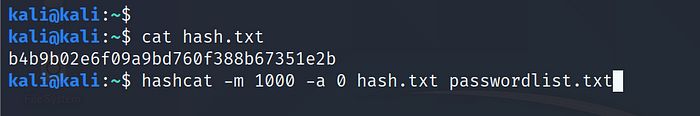
Example: b4b9b02e6f09a9bd760f388b67351e2b >hash.txt
Use Command:hashcat -m 1000 -a 0 hash.txt passwordlist.txt
where,
-m 1000: NTLM Digests hash mode
-a 0: Dictionary attack mode
hash.txt: txt file containing hash in a compliant format
passwordlist.txt: dictionary file containing passwords in plain text
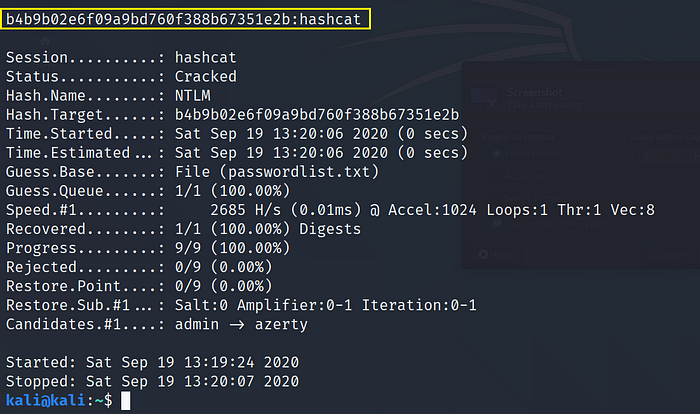
Cracked Hash: b4b9b02e6f09a9bd760f388b67351e2b= hashcat
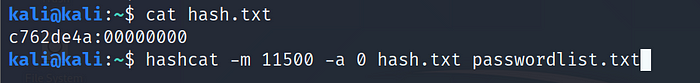
8. CRC32 Hashes
Make sure the input hashes are in hashcat compliant format as shown in the example.
Example: c762de4a:00000000 >hash.txt
Use Command:hashcat -m 11500 -a 0 hash.txt passwordlist.txt
where,
-m 11500: CRC32 hash mode
-a 0: Dictionary attack mode
hash.txt: txt file containing hash in a compliant format
passwordlist.txt: dictionary file containing passwords in plain text
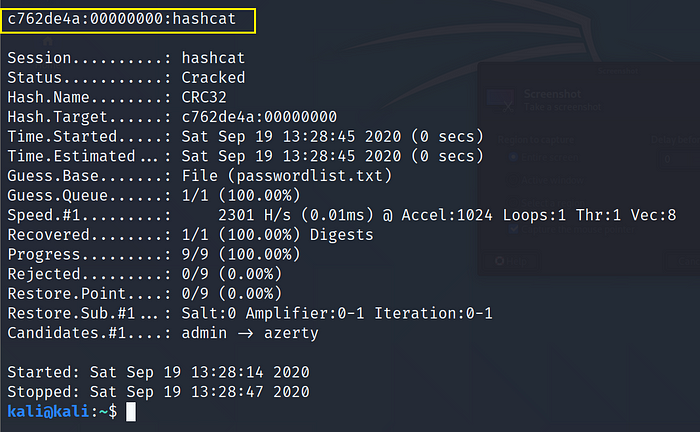
Cracked Hash: c762de4a:00000000 = hashcat
and to be continued…

