Member-only story
CVE-2025–24813: Apache Tomcat Path Equivalence Vulnerability $$$$ BOUNTY

Disclaimer: This document is for educational purposes only. Exploiting systems without authorization is illegal and punishable by law.
Stay ethical. Stay legal. Secure responsibly.
Thanks, Everyone for reading. Enjoy Happy Ethical Hacking!
Support me if you like my work! OR You Need exploitation Script!
Overview
Apache Tomcat recently disclosed a critical security vulnerability, CVE-2025–24813, which affects multiple versions of its servlet container. The flaw originates from improper handling of path equivalence checks when processing filenames containing internal dots (e.g., file…txt). Exploitation of this vulnerability may lead to:
- Unauthorized information disclosure
- File manipulation and unauthorized modification
- Remote Code Execution (RCE)
Given the widespread use of Apache Tomcat in enterprise environments, this vulnerability poses a significant risk.
Affected Versions
The following versions of Apache Tomcat are impacted by CVE-2025–24813:
- Apache Tomcat 9: 9.0.0.M1 through 9.0.98
- Apache Tomcat 10.1: 10.1.0-M1 through 10.1.34
- Apache Tomcat 11: 11.0.0-M1 through 11.0.2
Due to incorrect normalization of file paths containing internal dots, attackers can leverage this vulnerability to bypass security controls, access or modify sensitive files, and potentially execute arbitrary code.
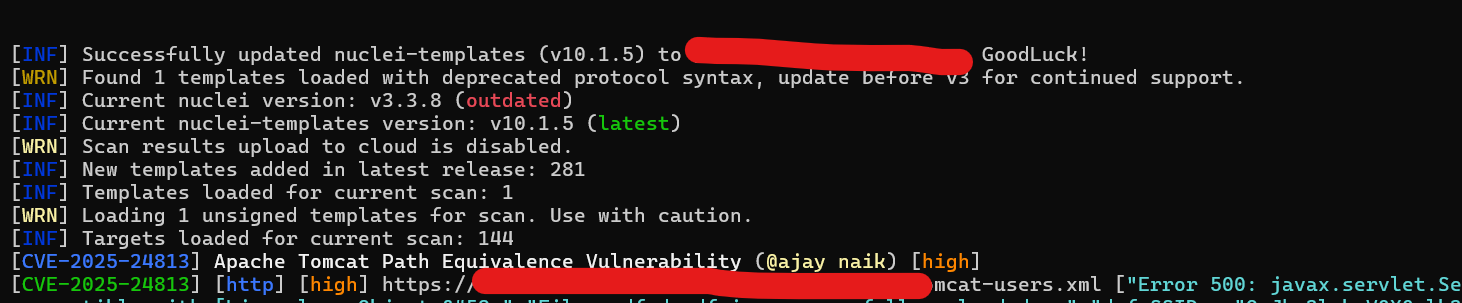
Exploiting the Vulnerability
1. Information Disclosure and File Manipulation
For an attacker to exploit this issue, the following conditions must be met:
- The default servlet is configured with write permissions (i.e., readonly=false).
- Partial PUT requests are enabled (default configuration).

