CyberDefenders Qradar101 Write-up
This write-up is based on Cyberdefenders Qradar101 challenge from Ali Alwashali.
You can check on https://cyberdefenders.org/blueteam-ctf-challenges/39
First of all, let’s start looking for offenses.
We can see 26 offenses between Oct 17 and Nov 8 of 2020.

Despite this, the logs are between 10/11/2020 10:00 PM and 10/11/2020 3:00 PM

How many log sources available?
We can find this information going to Admin > Log Sources.

What is the IDS software used to monitor the network?
We can see in figure 3 the IDS is one of the log sources.
What is the domain name used in the network?
We can find this information looking for payload events related to hosts as an example: Success Audit: A Kerberos service ticket was granted.

Multiple IPs were communicating with the malicious server. One of them ends with “20”. Provide the full IP.
We can display log Activity by Source IP to see what IPs generated more communication.
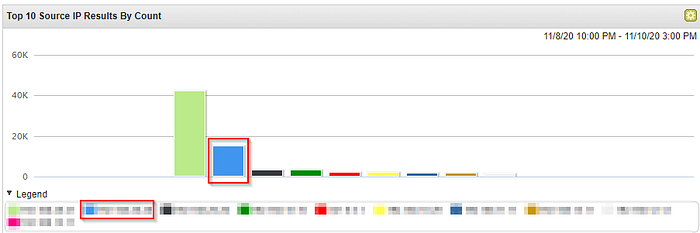
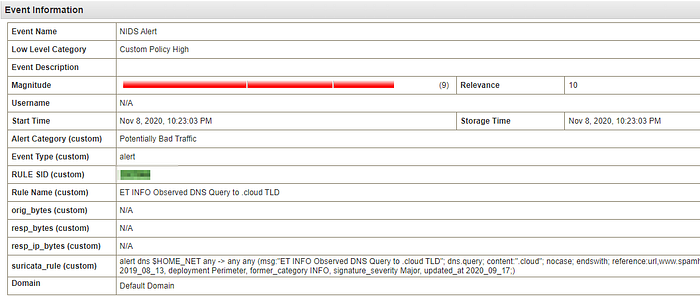
What is the SID of the most frequent alert rule in the dataset?
We can look for sid: in the payload with regular expression.

We will find 110 logs from SO-Suricata where 72
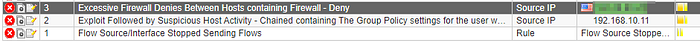
What is the attacker’s IP address?
In closed offenses, we can see a suspicious public IP.
The attacker was searching for data belonging to one of the company’s projects, can you find the name of the project?
We can search for project with regular expression.
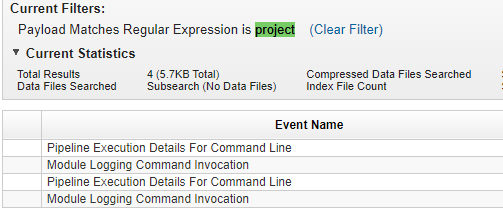
We will find 4 events, then we will read the payload.
What is the IP address of the first infected machine?
We can order the events by increasing time. We can see a suspicious event.
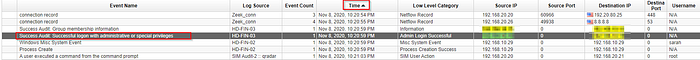
What is the username of the infected employee using 192.168.10.15?
Adding a filter where Source IP is 192.168.10.15 we can find the first username that logged in.
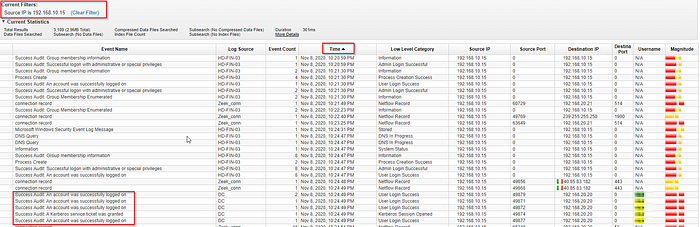
Hackers do not like logging, what logging was the attacker checking to see if enabled?
Let’s look for the first events that the attacker generated. We can observe a tool widely used in attacks.

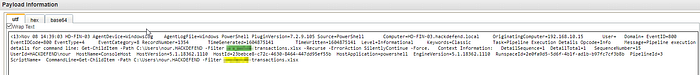
We can also see that the attacker is using PowerShell to find project48.
Name of the second system the attacker targeted to cover up the employee?
We can search for deleted files.

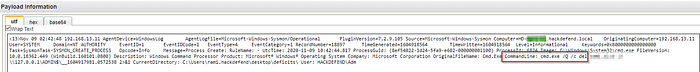
When was the first malicious connection to the domain controller (log start time — hh:mm:ss)?
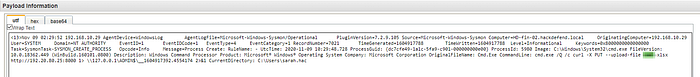
We can look for detected network connections by looking at the payloads, we can see that the first event is for a connection to the attacker’s server 192.20.80.25. And by a process that should not be making this connection.
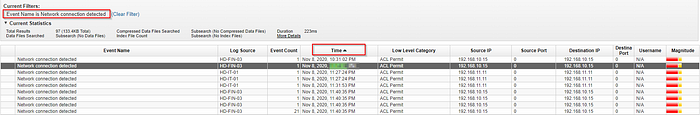
What is the md5 hash of the malicious file?
Filtering by hash, we find 10 events, when we look at the first one from the infected machine 192.168.10.15 we can find the .docx file with malicious hash.
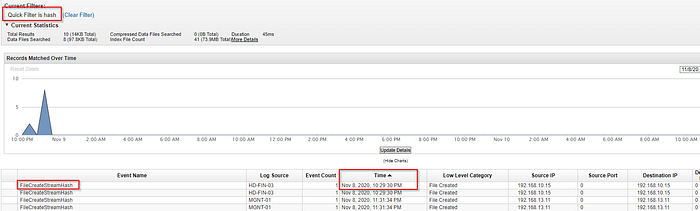
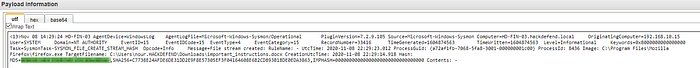
What is the MITRE persistence technique ID used by the attacker?
By looking up persistence techniques in mitre, we can search for logs about which techniques the attacker may have used.
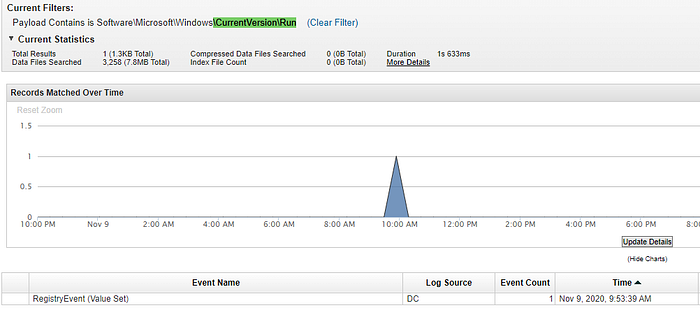

What protocol is used to perform host discovery?
We can discover this information by analyzing the outgoing traffic from the first compromised host.
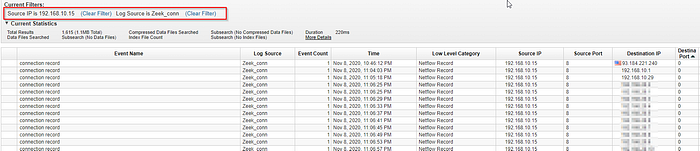
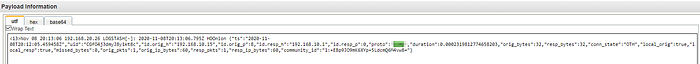
What is the email service used by the company?(one word)
We can look for traffic directed to the standard ports of the IP’s services, in this case, we had no success so let’s look at HTTPS traffic port 443 We checked on https://viewdns.info that most IP’s belong to Microsoft and so we found our answer.
What is the name of the malicious file used for the initial infection?
We found the file with the md5 hash.

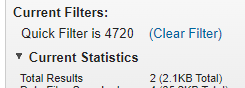
What is the name of the new account added by the attacker?
We can search for Event id 4720 A user account was created.
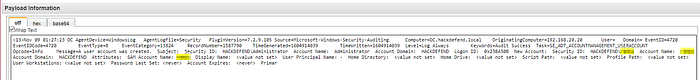
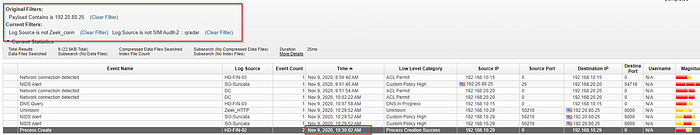
What is the PID of the process that performed injection?
We can look for process creation on the infected host.
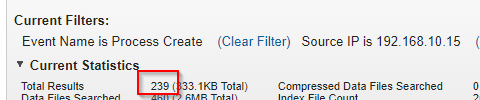

What is the name of the tool used for lateral movement?
I didn’t know about this tool and couldn’t find anything in the logs, I needed to use the tip, so searching on google I found https://github.com/SecureAuthCorp/impacket
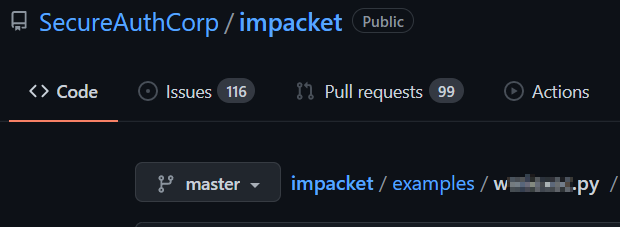
Attacker exfiltrated one file, what is the name of the tool used for exfiltration?
Searching for the events where there was communication with the attacker.
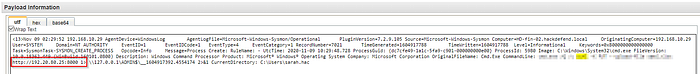
Who is the other legitimate domain admin other than the administrator?
We can see a list of users grouped by username and search for event 4672.

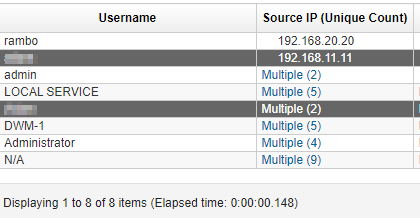
The attacker used the host discovery technique to know how many hosts available in a certain network, what is the network the hacker scanned from the host IP 1 to 30?
We can check if the first compromised machine scanned the network.

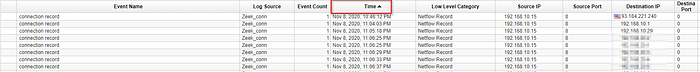
What is the name of the employee who hired the attacker?
While searching for which tool the attacker was performing data exfiltration we noticed a suspicious .xlsx spreadsheet.
I hope this write-up has helped you. Any questions, feel free to contact me on https://www.linkedin.com/in/isaacfn/


