Member-only story
Decoding Advanced XSS Payload Chaining Tactics
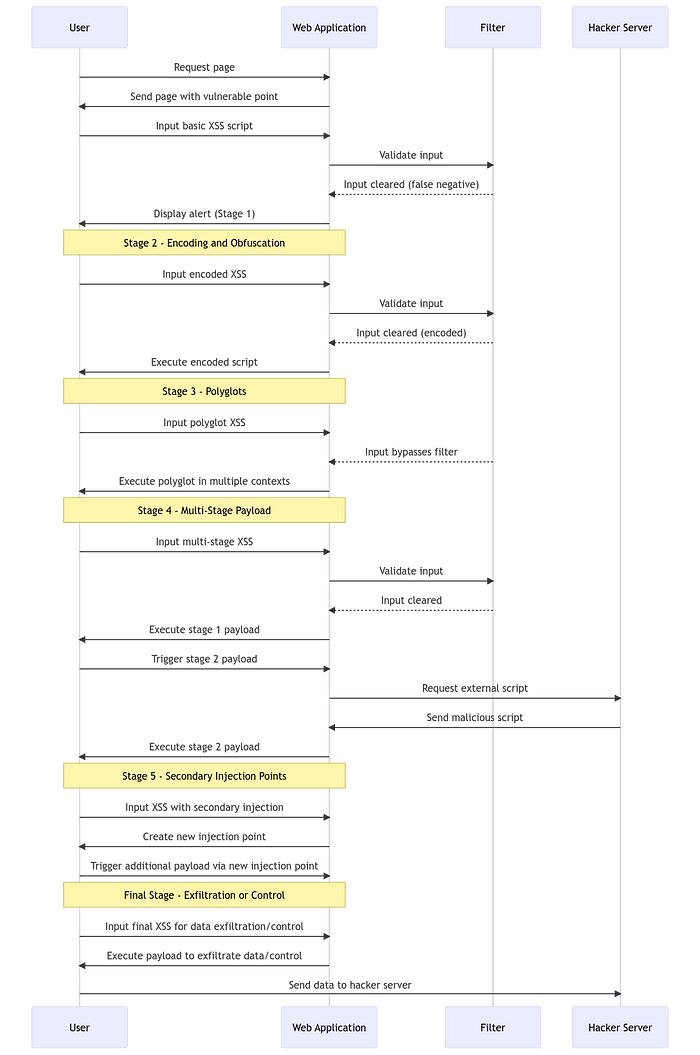
The digital landscape is an ever-evolving battlefield, with cybersecurity experts and malicious hackers continually adapting to each other’s strategies. In this high-stakes game, advanced Cross-Site Scripting (XSS) payload chaining stands out as a particularly sophisticated technique, demonstrating the complexity and potential severity of web application attacks. Let’s unravel the threads of a more complex XSS payload chain to understand the intricacies of such attacks.

Stage 1: Setting the Stage with Basic XSS
The journey into complex XSS chaining begins with a simple step — the foundation. It’s a straightforward script injection:
<script>alert('XSS');</script>Such a payload may be easily caught by modern security filters, but it serves as a crucial building block for more complex chains.
Stage 2: Encoding and Obfuscation
The next step is encoding and obfuscation, turning the simple into the indecipherable. Attackers often use multiple encoding layers or obscure characters to disguise the payload, ensuring it passes through basic filters undetected.
%3Cscript%3Ealert(%27XSS%27)%3B%3C%2Fscript%3ENow the payload is URL-encoded. Simple yet effective, but we’re building towards something far more convoluted.
Stage 3: Bypassing Advanced Filters with Polyglots
Enter the polyglot: a payload designed to execute in multiple contexts. These strings are chameleons, changing their function based on where they’re placed, often combining HTML, JavaScript, and CSS into a single, compacted attack vector.
jaVasCript:/*-/*`/*\\\\`/*'/*"/**/(/* */oNcliCk=alert())//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/--!> <sVg/<sVg/oNloAd=alert()//>\\\\x3ePolyglots can be particularly dangerous because of their versatility and the difficulty in detecting and mitigating them using traditional filtering methods.
Stage 4: Combining Techniques for a Multi-Stage Payload

