Member-only story
EXIF Geolocation Data: The Overlooked Risk in Uploaded Images

Introduction: A Simple Bug with Hidden Risks
Some vulnerabilities don’t require advanced tools or complex techniques to exploit; just attention to detail. One such vulnerability is unstripped EXIF geolocation data in uploaded images.
This happens to be one of my favorite bugs to hunt for. Why? Because it doesn’t require much effort, yet it can expose sensitive data like a user’s exact location, device information, or timestamps. Surprisingly, this type of vulnerability is often overlooked by developers and bug hunters alike, making it a hidden gem in the bug bounty world.
In this article, we’ll explore how unstripped metadata in images can lead to security risks, how to detect it, and why it’s critical to sanitize uploaded files.
What Is EXIF data?
EXIF (Exchangeable Image File Format) data is embedded information(metadata) stored in image files, such as JPG, PNG, and TIFF. This data often includes:
- Geolocation coordinates: GPS latitude and longitude.
- Device details: Camera make, model, and settings.
- Timestamps: When and where the image was captured.
If applications fail to strip this metadata during the upload process, sensitive data could be unintentionally exposed to malicious actors.
A Practical Demonstration: Unstripped Metadata
While testing for vulnerabilities, I encountered an image uploaded to a web application that hadn’t been sanitized properly. Upon analyzing the image using ExifTool, I discovered embedded geolocation metadata, which could expose sensitive information. Here’s the command I used to inspect the metadata:
Next, I inspected the metadata to verify the geolocation data was present:
exiftool index.jpg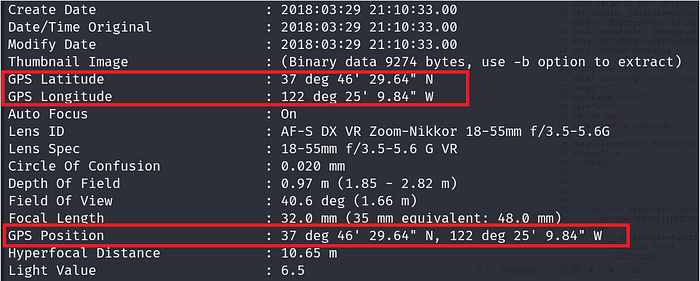
You have probably seen the metadata of an image before, but for those who haven’t, keep in mind that this is just a portion of the…

