Extracting Forensic Evidence from Smartwatch : A CID Hackathon Experience

Introduction
In today’s world, digital evidence plays a crucial role in solving crimes, and smartwatches have emerged as unexpected but powerful forensic tools. At the recent CID Hackathon, our team embarked on a mission to extract and analyze smartwatch data beyond conventional health metrics — delving into GPS movements, call logs, payment transactions, and even multimedia evidence. Our goal? To demonstrate how these devices can serve as silent witnesses in criminal investigations.
The Objective
Our primary aim was to transform raw smartwatch data into actionable forensic insights by extracting system logs, communication records, and user activity. This involved:
- Uncovering forensic data relevant to crime investigations, such as GPS trails, call logs, and payment transactions.
- Accessing hidden system files using advanced debugging tools.
- Extracting sensitive multimedia content, including stored images and audio files.
- Reconstructing movement timelines from GPS and sensor logs.
- Hosting and visualizing the extracted data on a secure web server for analysis.
- Exploring real-world crime investigation applications for law enforcement and forensic experts.
Data Extraction & Processing
1. Extracting Critical Crime-Related Data
Our extraction focused on gathering digital evidence that could assist in criminal investigations:
- GPS Movement Logs & Location Data — Tracking suspect movements before, during, and after an incident.
- Call & Messaging Logs — Identifying communication patterns, contacts, and possible accomplices.
- Stored Audio & Images — Recovering recorded conversations and images that may provide crime-related evidence.
- NFC Payment & Transaction History — Extracting smartwatch-based tap-and-pay records for financial investigation.
2. Advanced Extraction Techniques Using SDB (Smart Development Bridge)
Since the smartwatch was running on Tizen OS, we used SDB (Smart Development Bridge) to access deeper system files and extract forensic data efficiently.
- Connecting to the smartwatch:
sdb connect <WATCH_IP_ADDRESS>- Extracting GPS logs and movement data:
sdb pull /home/owner/media/GPS_logs.txt .- Retrieving stored images and audio files:
sdb pull /home/owner/media/DCIM/ extracted_images/- Extracting payment transaction logs from tap-and-pay services:
sdb pull /home/owner/media/NFC_transactions.log .- Fetching call logs and messaging records for communication analysis:
sdb pull /home/owner/logs/call_logs.txt .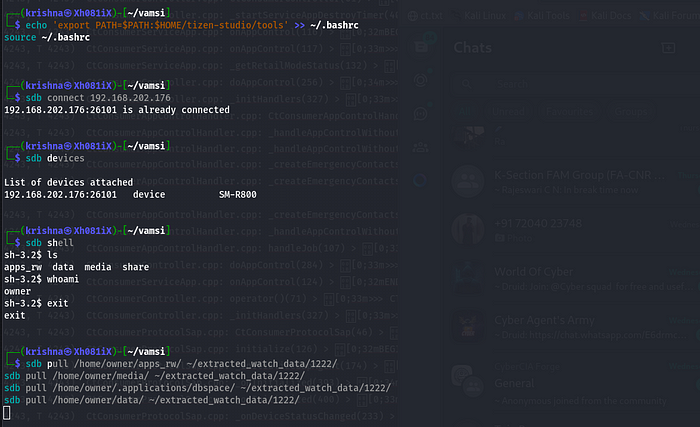
3. Smartwatches as Silent Witnesses in Crime Scene Investigations
Smartwatches capture constant data about user activity, making them invaluable forensic tools in crime cases. Potential investigative applications include:
- GPS Location Tracking: Establishing an alibi or tracking suspect movements.
- Call & Message Records: Identifying crucial connections in a case.
- Heart Rate Analysis: Detecting stress spikes at potential moments of crime involvement.
- Stored Media Evidence: Recovering deleted images or audio related to a case.
- Transaction Records: Tracing financial movements linked to illegal activities.

4. Data Cleaning & Structuring
To make the extracted data meaningful and usable for investigations, we implemented:
- Filtering techniques to eliminate false or irrelevant log entries.
- Imputation methods to reconstruct missing or incomplete data.
- Time-series structuring to align GPS movements and event timestamps.
- Decryption & conversion tools to handle proprietary or encrypted smartwatch data.
5. Hosting on a Secure Web Server
For real-time accessibility and analysis, we:
- Used Flask/Django for backend API services.
- Deployed the system on AWS/GCP for secure data storage.
- Created API endpoints to allow visualization of movement trends and forensic insights.
Data Visualization & Analysis
To make forensic data more interactive and actionable, we built a dashboard using React.js and D3.js, enabling investigators to:
- Track GPS movements on a map-based interface.
- Analyze suspect communication trails via call and messaging logs.
- Detect anomalies in smartwatch logs, such as sudden heart rate spikes.
- Access stored images, transactions, and system logs in a structured manner.
Challenges Faced
Despite the breakthroughs, we encountered several challenges:
- Device Compatibility Issues — Different smartwatch OS versions required unique extraction techniques.
- Data Security & Encryption — Some files had proprietary encryption, requiring advanced decryption methods.
- Access Restrictions & Rooting Difficulties — Certain data required elevated privileges to extract.
- Data Synchronization Errors — Timestamps across logs were inconsistent and required correction.
Key Takeaways
- Smartwatch data is a goldmine for forensic investigations — Extracting system logs, call records, and multimedia files provided a wealth of evidence.
- SDB is a powerful forensic tool for Tizen-based devices — Direct access to internal storage allowed deeper data extraction.
- Data preprocessing is crucial — Cleaning and structuring raw data significantly improved its usability for analysis.
- Real-time hosting & visualization enhance investigation speed — Interactive dashboards provided instant insights into extracted data.
- Smartwatches are emerging as critical digital evidence sources — Their continuous tracking and logging make them invaluable in crime scene investigations.
Conclusion
The CID Hackathon provided a unique opportunity to explore the hidden potential of smartwatch data in crime investigations. By successfully extracting and structuring forensic data from these devices, we showcased how law enforcement agencies could leverage wearable technology as digital witnesses.

🚀 Runner-Up at CID Hackathon! 🚀 Our team’s efforts in developing an IoT forensic evidence extractor were recognized at the CID Hackathon, where we secured the runner-up position. We successfully showcased how smartwatch data can be leveraged for crime investigations, winning a cash prize and recognition from cybersecurity experts.
Let’s keep the conversation going! Connect with me on LinkedIn:
🔗 Vamsi K
If this article resonated with you, show some love — clap, drop a comment, and follow. Your support inspires me to share more! 🔥💭

