Facebook Text Injection Vulnerability: A Creative Approach | Bug Bounty

Hi Guys,
In this write-up, we’ll walk through the steps we took to identify the vulnerability of a simple text injection and how we escalated it, and the significance of turning a low-severity issue into something more serious security issues. Our success in getting this reported and rewarded shows how out-of-scope issues, when viewed through the right lens, can present significant risks.
Introduction
In the world of bug bounty hunting, not every vulnerability you stumble upon is immediately considered “in scope.” However, with creativity and a deeper understanding of how systems interact, even seemingly benign issues can be escalated into impactful security threats. This write-up highlights one such case where we identified a text injection vulnerability — typically classified as out-of-scope in Facebook’s bug bounty program — that, with some innovative thinking, we escalated it into a valid security exploit.
Overview:
Our journey began with a simple discovery: a text injection vulnerability on an Instagram authorization endpoint. On its own, this might not have seemed dangerous or noteworthy. However, by leveraging OAuth authentication flows and Open Redirection, we managed to create a chain of events that turned an out-of-scope issue into a legitimate security concern.
This creative escalation ultimately demonstrated a potential phishing attack scenario that tricked users into believing their Instagram accounts couldn’t be logged into — after they had successfully authenticated.
The Discovery: A Simple Text Injection
During a routine test of Instagram’s OAuth process with a third-party application, we were unexpectedly redirected to the following error page:
https://www.instagram.com/oauth/authorize/third_party/error/?message=Insufficient%20Developer%20Role%3A%20Insufficient%20developer%20role
At first glance, this was a typical error page indicating insufficient permissions for the third-party app. However, we noticed something peculiar — the message parameter was reflected back on the page unmodified . This led us to realize that any user-supplied text could be injected into the page via the URL parameter.
At this point, we had a basic content spoofing issue on our hands. While content injection is typically considered out of scope in Meta’s bug bounty program, we saw potential to escalate it.

Recognizing this behavior as a text injection vulnerability, we wondered if we could exploit it further.
Here’s where the creativity came into play: The Instagram Authentication flow will automatically send the user to the previously defined next parameter—our crafted URL, which contains the malicious message reflecting back on the legitimate Instagram domain.

Since the error message was on OAuth endpoint, we crafted a new URL with a more convincing and dangerous message related to authentication error as malicious message.
By leveraging a message that seems like a typical login error, I combined the social engineering tactic with technical exploitation to increase the likelihood that users would follow the malicious instructions.
https://www.instagram.com/oauth/authorize/third_party/error/?message=We%20are%20unable%20to%20log%20in%20your%20account.%20Please%20contact%20support@attacker.comThis new message was reflected on the error page as:

By sending the crafted link via Facebook Messenger, When an unauthenticated Instagram user clicks this link in Facebook Messenger, they are redirected to the Instagram login page, as the platform requires the user to authenticate.
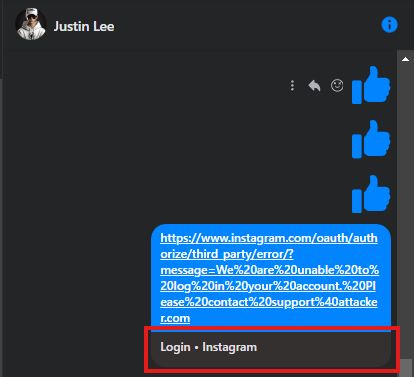
Once they successfully logged in, they were shown the malicious message saying “We are unable to log in your account. Please contact support@attacker.com”., effectively tricking them into believing there was an issue with their account.
The combination of the legitimate login flow followed by the crafted malicious message created a convincing illusion.
Enhancing the Impact: Targeting Mobile Users
One of the primary challenges with phishing attacks is convincing users that the spoofed content is legitimate.
We realized that mobile users were especially vulnerable in this situation, When accessing the malicious link on their mobile devices, the full URL might not be visible, and they would only see the domain “instagram.com”.

Since mobile users don’t see the full URL and have just logged in through a legitimate Instagram interface, they are likely to trust the message and follow the attacker’s instructions.
This helps conceal the fact that the user is being redirected to a malicious endpoint and creates a convincing phishing scenario, tricking users into thinking their login attempt failed and that they need to contact the malicious support email.
Proof Of Concept:
This successful escalation turned what could have been an overlooked issue into a rewarded submission — proving that with a bit of creativity, even low-severity bugs can become impactful security risks.
Why This Demonstrates Significant Risk?
Even though content injection vulnerabilities are often considered out of scope, this report highlights a real phishing risk because:
1. Legitimate Login Flow: By leveraging the legitimate Instagram login page, we added trust to the attack, making it more believable.
2. Post-Login Manipulation: Showing the phishing message after the user successfully logs in creates confusion and makes the user more likely to believe that there’s an issue with their account.
3. Targeting Mobile Users: The attack is particularly dangerous for mobile users who cannot see the full URL and are less likely to detect the manipulation.
The Problem
after the weeks i notice that they fixed the next= parameter redirection on a login they fixed the instagram that even you defined the url, it will now automatically redirected to home page instead of malicious crafted endpoint but they didn’t fix the text injection vulnerability so i ask for update.

after a weeks again, they close my report as informative and im surprised about the decision after they triaged and make initial fixed they come up with this assesment?
This is because the issue was limited to text injection and no further security/privacy impact could be achieved.
the fact i cleary provide the impact with a video, this “philip” seems not aware of that impact the fact he said “the issue was limited to text injection”

i reopened the report and asking to provide reasoning behind decision why they made initial fixed and close it to informative and this what they only said:

its totally unfair honestly, i can only accept this if my report are not fixed at all or still can reproduce, but they made intial fixed and they triaged it, i wonder if this only a mistake or what, but based on they last response and the timeline. They did not proritize my report due to “volume of reports”
to all of you wondering what they patched they remove this feature:

Timeline:
- Oct 13, 2024 (Initial report)
- Oct 14, 2024 (Facebook Initial Evaluation)
- Oct ??, 2024 (Initial fixed)
- Dec 07, 2024 (Facebook Triaged)
- Dec 21, 2024 (Close as informative)
- Dec 21, 2024 (reopen & ask for the assesment they made and if they still can reproduce the bug describe)
- Jan 06, 2025 (bullsh*t)
Thanks for reading my write ups, I hope you enjoy reading and learn you something on this article and and YES this write ups is just to destroy philip & spencer just kidding, its not new to bug bounty and we can do anything about it just move on.
