Member-only story
File Inclusion — TryHackMe Simple Write-up | 2023
TryHackMe’s File Inclusion — This room introduces file inclusion vulnerabilities, including Local File Inclusion (LFI), Remote File Inclusion (RFI), and directory traversal | Karthikeyan Nagaraj
Make Sure to Connect with TryHackMe’s VPN to Attack box to access the Machine
Task 2
Deploy the Machine
Task 3 — Path Traversal
- Also known as Directory traversal, a web security vulnerability allows an attacker to read operating system resources, such as local files on the server running an application.
- The attacker exploits this vulnerability by manipulating and abusing the web application’s URL to locate and access files or directories stored outside the application’s root directory.
- Path traversal vulnerabilities occur when the user’s input is passed to a function such as
file_get_contentsin PHP.
1. What function causes path traversal vulnerabilities in PHP?
Ans: file_get_contentsTask 4 — Local File Inclusion — LFI
- Give Lab #1 a try to read /etc/passwd. What would the request URI be?
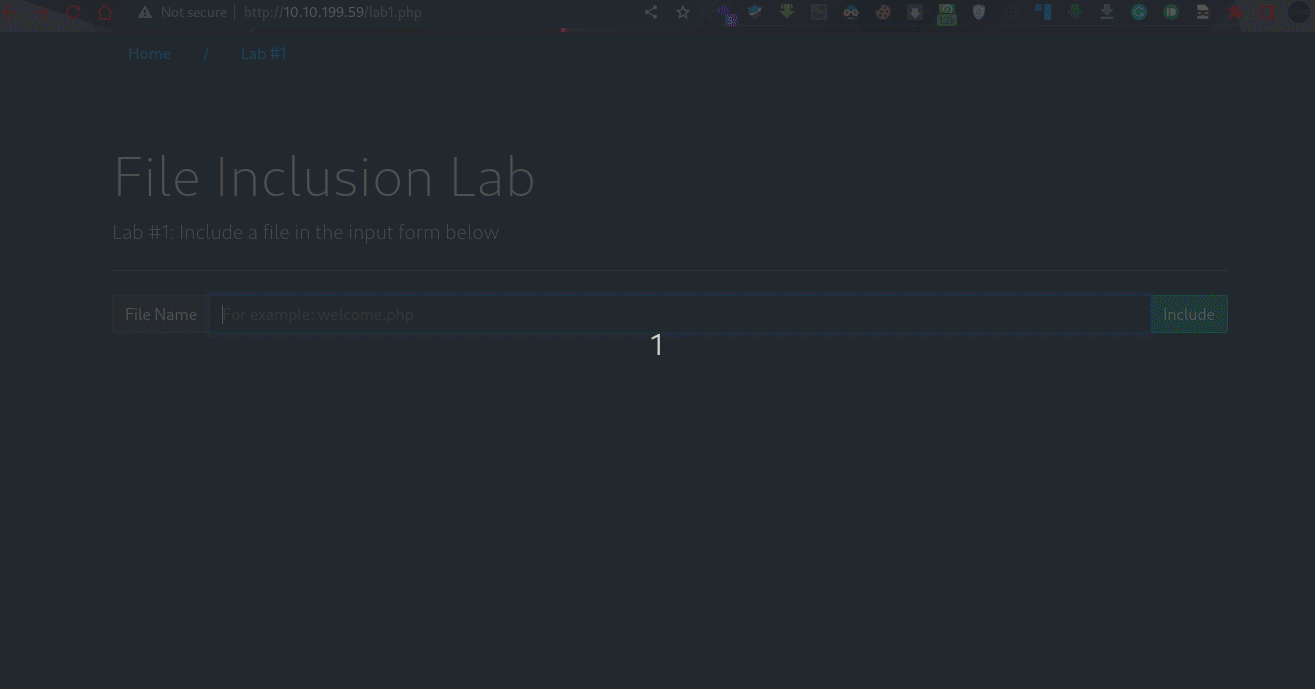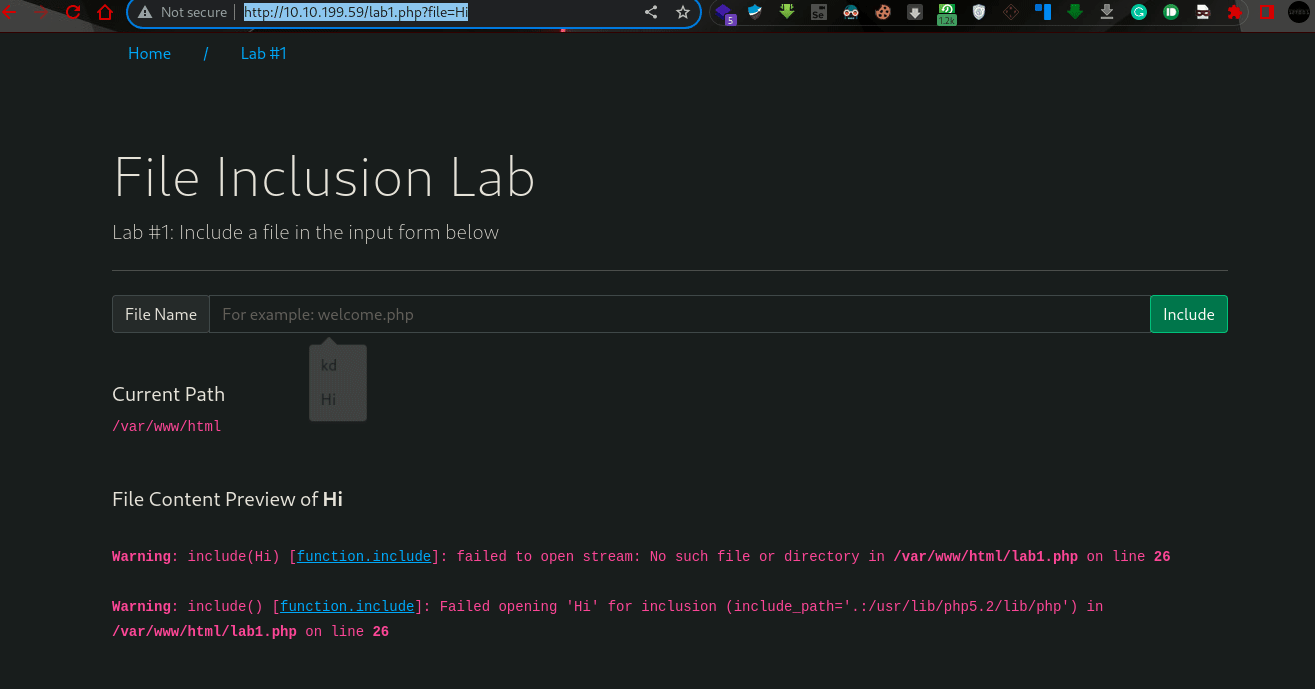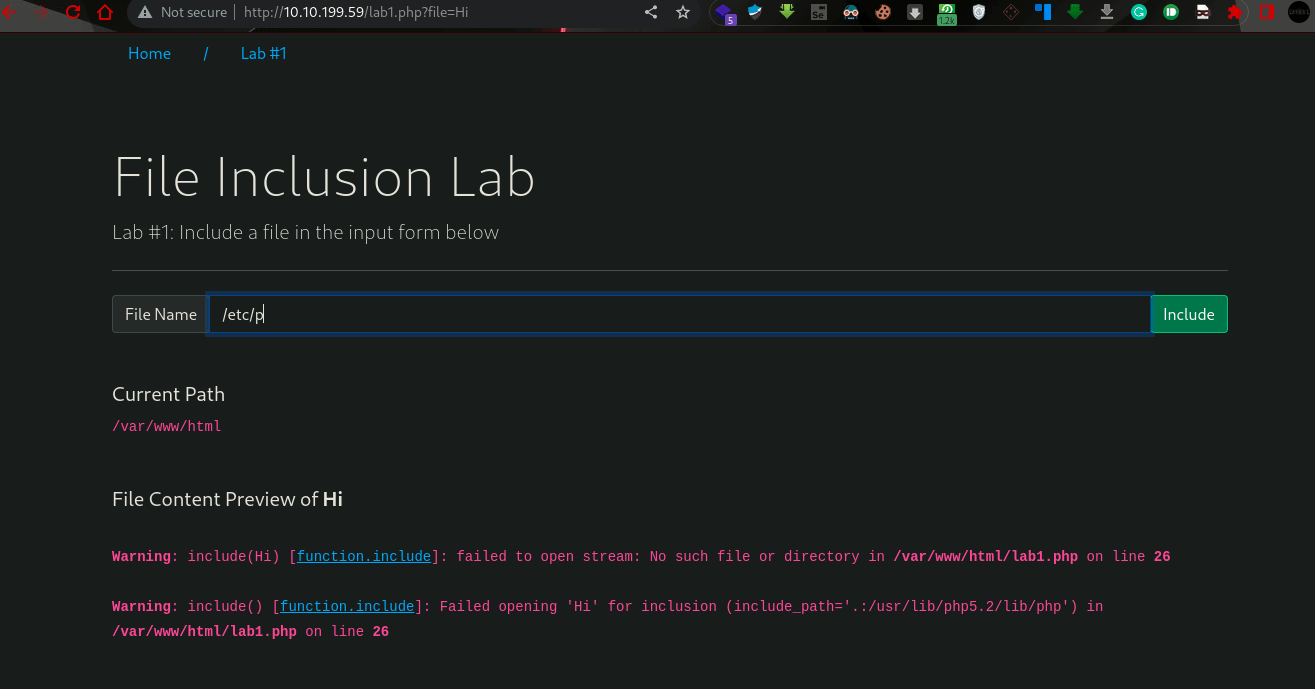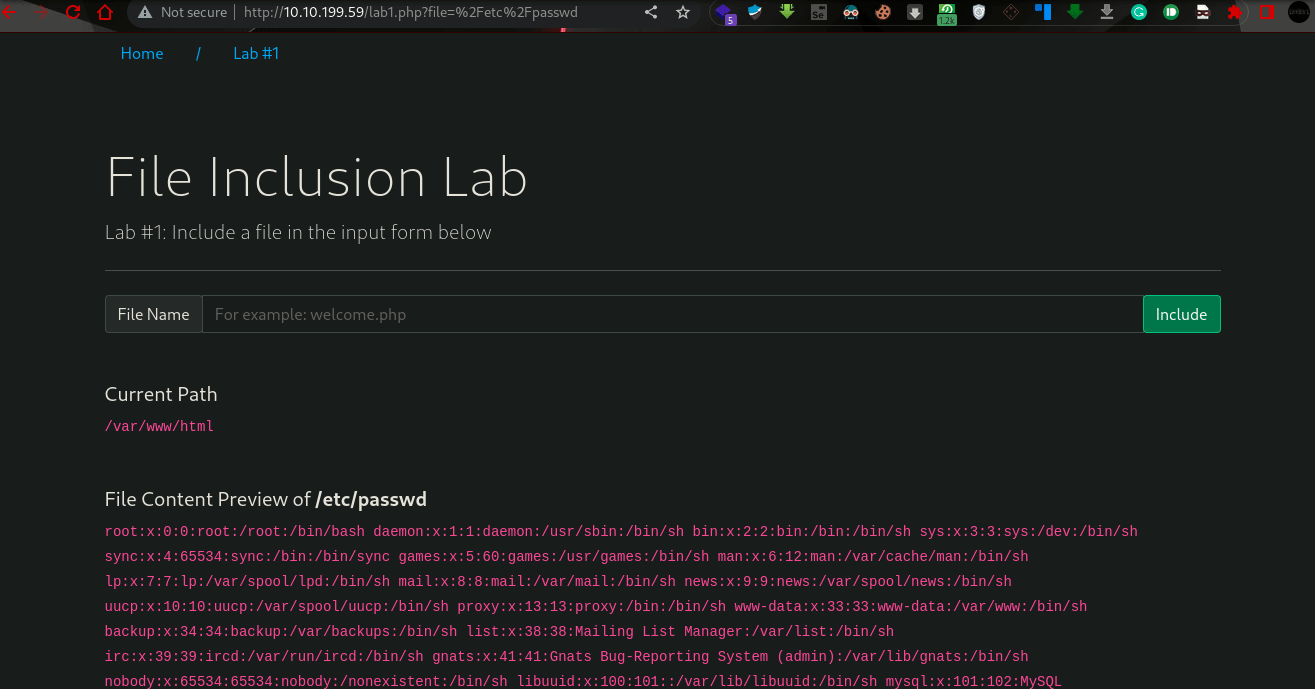
Ans: /lab1.php?file=/etc/passwd2. In Lab #2, what is the directory specified in the include function?

Ans: includesTask 5— Local File Inclusion — LFI #2
- Give Lab #3 a try to read /etc/passwd. What is the request look like?
If we put our payload into the text field “File Name” the path gets encoded, so we have to inject the payload into the search bar as below

