Finding the hidden function led to a $300 IDOR

Hello folks 👋
Today I’m about to tell you guys a story about finding the beautiful BAC on a program so fasten your seatbelt and sit tight.
The story behind the attack is that the attacker can read the comments of the circle that the manager has removed him from. Quite interesting nah ?!
So let’s get into the attack scenario :
- In the first step, we create two accounts, a manager and an attacker
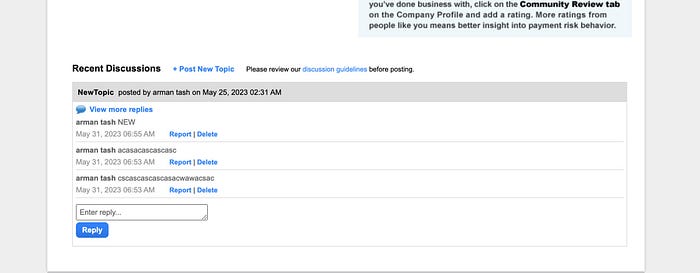
- Then we login to our manager account and make some comments. It doesn’t matter what the comment is about; we keep doing it until we see the option to view more replies.
- This is the key moment → We can do it if we see the view more replies option because this is a hidden function that won’t be called unless the comments have reached a certain level.
- After we have done that we can now invite our dear attacker to the program and make sure that the attacker account can send and receive comments in the program.
- As for the attacker, we keep commenting with the attacker account until we reach the magical view more replies option in the attacker account too.
- After inviting the attacker and commenting on his account, if we
capture the request in the burp we see the following request going to
the server and we send it to the repeater too. - After we invited the attacker and made a comment noe from the manager account we knocked the attacker out of the account and made sure that he had no access to the account and the commenting circle
- Now we head back to the repeater where we captured our request and
hold it there and if we make that request again we can see that we are
able to send and see comments again but we are kicked out of the
account. bingo !!
POST /xxxx/xxxxx/circleHome HTTP/1.1
Host: start.redacted.tld
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 65
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close
circleHome&userAction=viewAllReplies&topicId=xxxx&circleId=xxxxThe security issue of this vulnerability is that members of the circle
might have some private messages that they don’t want anyone to see and by this issue, the attacker can the their comments.
After reporting the bug now we can relax!

