From Responder to NT Authority\SYSTEM
Hi there, my name is Meridian Miftari. I'm 21 years old (Security Researcher) from Kosovo.
On this article I will talk or describe an offensive method of attacks in networks by using Responder & SMB Impacket ToolsThis attack that I will describe in fact it is known as man in the middle attack(MITM), this attack confronts with the idea why it's dangerous to give to others the password of the wireless.
This network pen testing was performed in an authorized environment of a Private Telecom Company, that for matter of confidentiality im not allowed to mention the name of the client!

Here I will describe a short brief explanation of the features that this tool has, and those which we will use them.
Responder its an Offensive Security Tool that Red Teams use it, as we mentioned that its more a man in the middle attack, it has to do with intercepting the communication between 2 or more systems in a network.
Some features of the Tool

In the launching process, this is how the tool looks, I’ve executed in the wlan0 interface, and down we can see the built-in servers that this tool has
- Smb
- HTTP
- MySQL
- Kerberos etc.
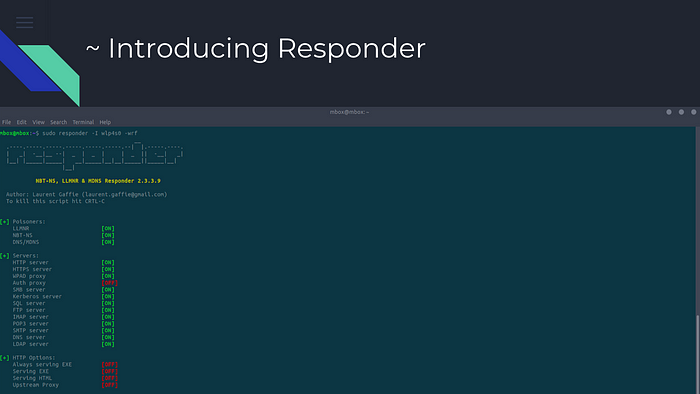
So after the execution of this tool, we see it sends requests in every computer inside that network, and in the end we see that the target has responded to us with his username along with the NTLMv2 Hash

After we captured NTLMv2 Hash and decrypt it with the help of John the Ripper, that is a very well-known password cracker, the decryption process it depends on the complexity of the password that the system has.
After the cracking process is finished, we can see the decrypted password in the picture!
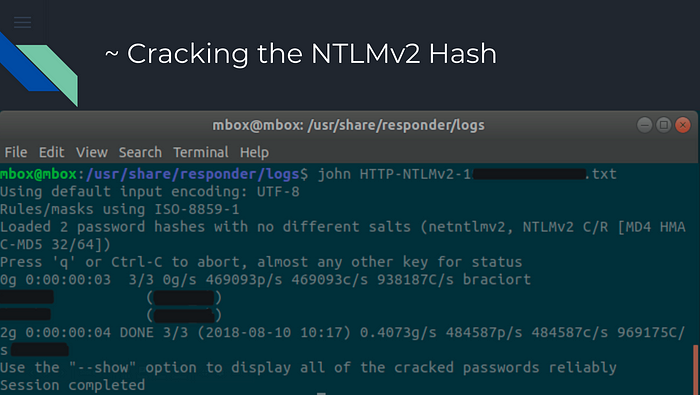
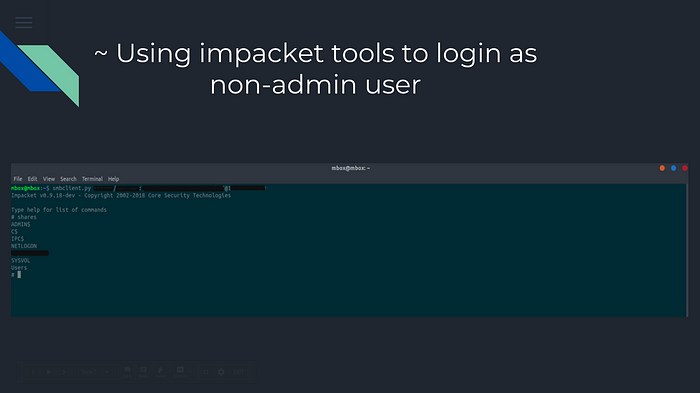
After the cracking process, we will use Impacket packages.
Impacket is a collection of Python classes for working especially with network protocols, and one of them is smbclient.pyWe will use the username & password we got from John the Ripper Cracker to login to the disk shares of the system, as seen in the picture.
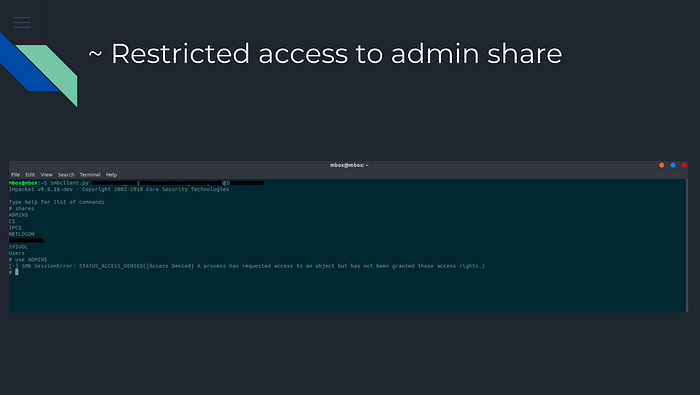
We try to access the Administrator Shares of the system, however an error appears : Access Denied.
It means we have restricted access to them.!
Further we will 2 other scripts, that are part of Impacket Packages that we mentioned earlier.
Rpcclient.py & GetUserspns.pyRpcclient.py : This script its default installed in Kali Linux, we will use to enumerate domains with the Username & Password of the system.
GetUserSPNs.py : This script will try to find and fetch Service Principal Names that are associated with normal user accounts.
(SPN) are unique identifiers of a service instance in, are used by Kerberos authentication to associate a service instance with a service logon account, and they hold a TGT(Ticket Granting Ticket)that is a small, encrypted identification file with a limited validity period.
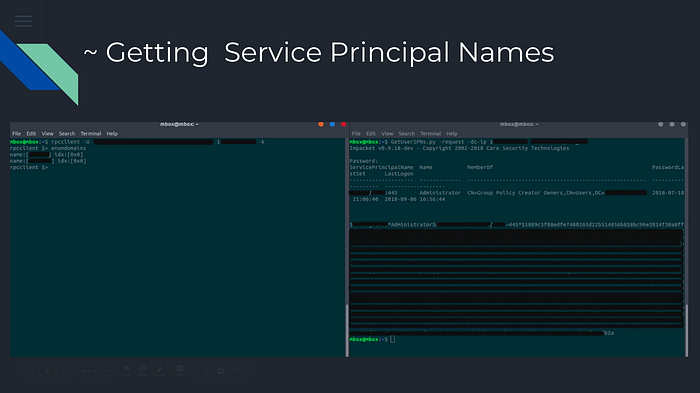
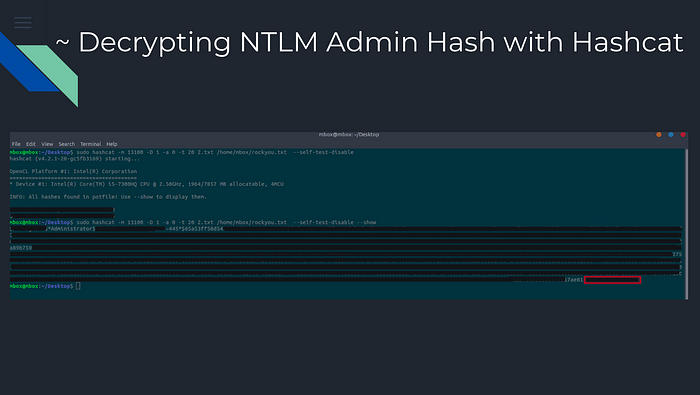
After getting the valid TGT, we decrypt using the help of Hashcat that is also a very well-known password cracker.
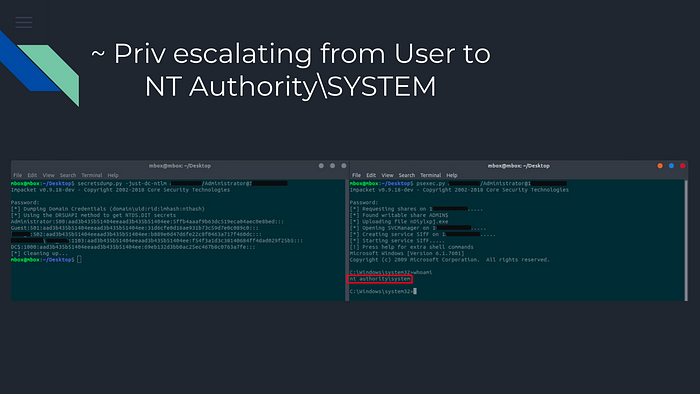
In the end after we get the password of the Administrator, we will login to it, and we escalated our privileges from Simple User to NT Authority\SYSTEM
Prevention Ways by this attack are described in the picture.

//Hope, you have a great time reading this writeup and learned new things
//Thank you very much.
Tools :
