FUNBOX-7: EASYENUM Walkthrough (Vulnhub)
Description

Boot2root in 6 steps for script-kiddies. Timeframe to root this box: 20 mins to never ever. It’s on you. You can do this in 20 minutes or even less if you get the right user to perform the brute force. Another nice and easy box designed by @0815R2d2. To download visit https://www.vulnhub.com/entry/funbox-easyenum,565/
Port Scanning
As usual start with scanning the network with Nmap for open ports and services.

Web Reconnaissance
Nothing is important here. Then I tried to figure out some hidden directories using gobuster on port 80.

…and here we goo. Many hidden directories are discovered but the one which helps us to gain the reverse connection is mini.php. Visit the mini.php which already has some file and I tried to upload a file named secret to see if uploading is allowed or not and yes we can.
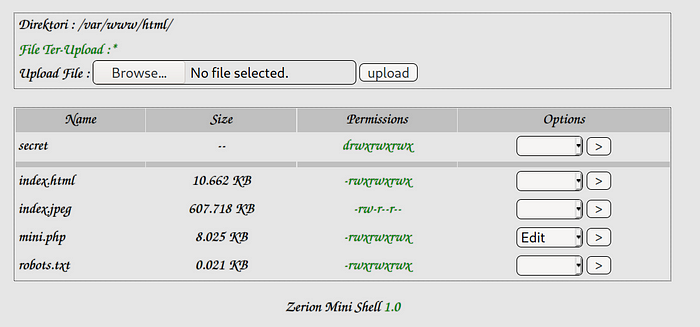
Time to make our hands dirty. Upload a PHP reverse shell file like this

and open another terminal for listening to the reverse connection using Netcat. Click on Go option 3–4 times if not getting the reverse shell.

After getting a low privileged shell I tried the LinPEAS script and found the GCC-8 compiler is installed. Then I installed linux_exploit_suggester to enumerate some Linux version exploit but failed.
Finally, spending a good amount of time I decided to perform a brute force attack using hydra on service SSH on each user. First I tried on user harry but even after spending 10–15 minutes, I got nothing. Then I tried on user goat and after 6–8 minutes, I discovered the key.

Hint- The key is something similar to Funbox-4 user thomas SSH key.
Privilege Escalation
Login through SSH and since we have the key let’s check for the sudo permission this user has.

So, this user has can run MySQL as root. Visit this site https://gtfobins.github.io/gtfobins/mysql/ and you can find the privilege escalation technique through MySQL service.

Finally, navigate to the root directory and we can access the root flag.

For more walkthroughs stay tuned…
Before you go
Visit my Funbox series walkthrough’s:-
and clap 👏 if you like what you read. Feedback is always welcomed.

