Member-only story
💸Get $5000: GitHub Dorks & Leaks 🚀
🔥Free Article Link
GitHub is a goldmine for both security researchers and malicious actors. While it serves as a critical platform for developers, it often hosts exposed credentials, API keys, and sensitive corporate data. In this guide, we’ll dive into GitHub Dorking — how attackers find leaks, how I personally landed a $5000 bounty, and how to protect your repositories from accidental exposure. Let’s secure the code and earn some rewards! 💪✨

🔎 What Is GitHub Dorking?
GitHub Dorking involves using advanced GitHub search operators to pinpoint sensitive data in public repositories. Because developers can accidentally push private API keys, passwords, SSH credentials, or database connection strings to their repos, GitHub becomes a prime hunting ground for attackers.
With just a few smart search queries, threat actors and security researchers can dig through billions of lines of code to spot leaked credentials in seconds. It’s surprisingly powerful — and equally dangerous. ⚠️🔐
💻 How Attackers (and Researchers) Use GitHub Dorks
1. Master the GitHub Search Operators
GitHub’s search bar is more powerful than most realize. These operators help narrow down your targets:
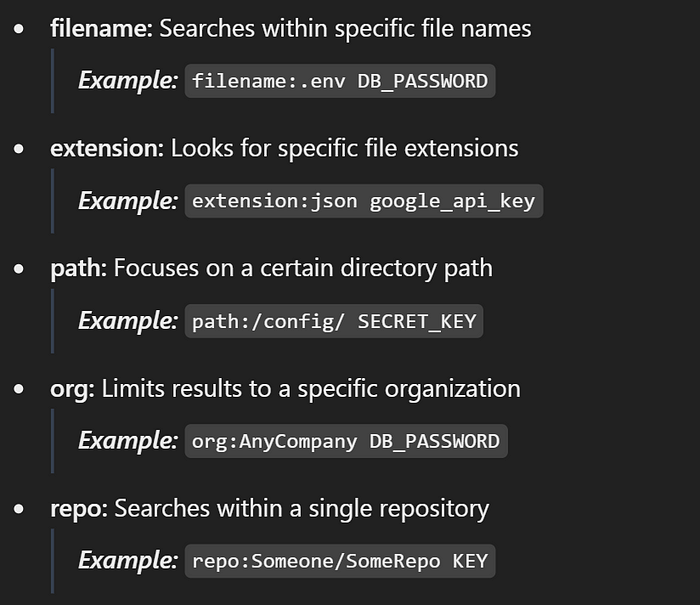
Armed with these operators, both ethical hackers and cybercriminals can quickly unearth valuable data. ⚒️✨

