Member-only story
GraphQL Vulnerabilities: A Complete Guide to Security Testing and Advanced Exploitation Techniques

Disclaimer: This document is for educational purposes only. Exploiting systems without authorization is illegal and punishable by law.
Stay ethical. Stay legal. Secure responsibly.
Thanks, Everyone for reading. Enjoy Happy Ethical Hacking!
Support me if you like my work!
FREE-LINK:
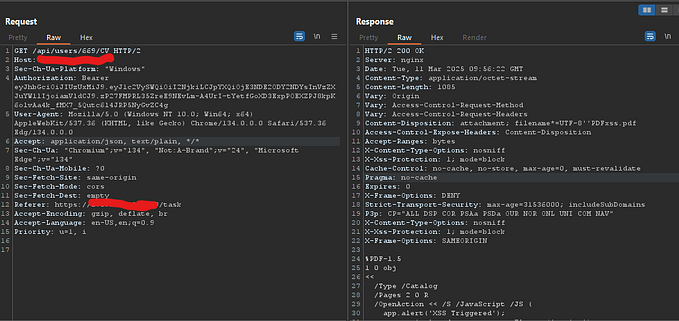
GraphQL has revolutionized how APIs are designed and consumed, offering flexibility, efficiency, and powerful querying capabilities. However, with great power comes great responsibility. GraphQL’s unique architecture introduces a range of security vulnerabilities that, if left unaddressed, can lead to severe consequences such as data breaches, denial of service, and unauthorized access.
In this blog, we’ll dive deep into the world of GraphQL vulnerabilities, exploring how to test for them, advanced techniques for exploitation, and best practices to secure your GraphQL APIs.