Member-only story
Hacking AWS Cognito Misconfiguration to Zero Click Account Takeover
Hi all, hope you are keeping well and staying safe. This blog is about my recent Account Takeover finding.
Inspiration
I was going through Hackivity from Hackerone and read about the amazing Flickr Account Takeover. Thanks to Lauritz for the find and an excellent blog post. If you haven’t read it, it is here. I’ll also provide some references at the end of this post.
Introduction
I was testing a web application related to health care. Some of the functionalities were to schedule appointments with doctors, order medicines, interact with doctors within the website via messaging, etc. It was an authenticated test, credentials were provided.
It is important to note that the email address and other details cannot be changed from the application, we had to send a request to support for any changes.
Upon logging in to the app, I have noticed the login request is sent to Amazon Cognito URL. If you need a thorough understanding of the login, pl go through Laurtiz blog or this blog by Appseco.
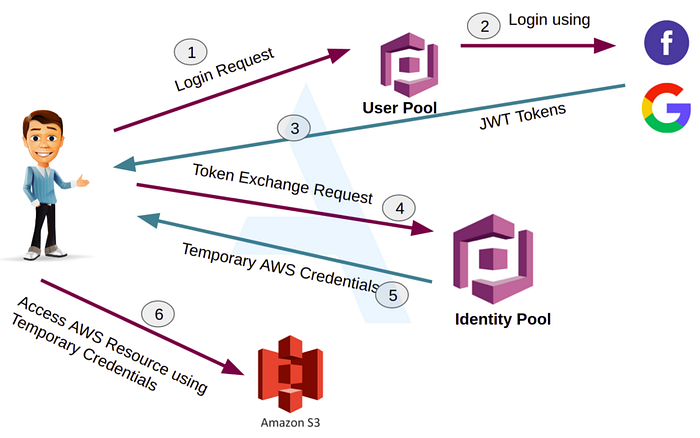
So, the login flow in the app I was testing was as follows.
- Login to the App, a POST request is sent to Amazon Cognito
- If creds are valid, Amazon Cognito provides the tokens.
HTTP/2 200 OK
Date: Thu, 32 Abc 2040 25:51:36 GMT
[...]{
"AuthenticationResult":
{
"AccessToken":"[REDACTED]",
"ExpiresIn":3600,
"IdToken":"[REDACTED]",
"RefreshToken":"[REDACTED]",
"TokenType":"Bearer"
},
"ChallengeParameters":
{
}
}
- Next, the app sends a request to Amazon Cognito to fetch the user details. Specifically, the
X-Amz-Target: AWSCognitoIdentityProviderService.GetUserheader is sent in a post request along with the AccessToken.
POST / HTTP/1.1
Host: cognito-idp.eu-west-1.amazonaws.com
Referer: https://target
Content-Type: application/x-amz-json-1.1
X-Amz-Target: AWSCognitoIdentityProviderService.GetUser
X-Amz-User-Agent: aws-amplify/0.1.x js…
