How I earned $500 from Google - Flaw in Authentication
Hello Everyone!
This is my first writeup.
Today I will share the write-up of my first accepted bug in Google, Which is in “Google Cloud Partner Advantage Portal” where I was able to modify personal details for victim account via Broken Authentication.
What does “broken authentication” mean?
If the login functionality of your application can be subverted or bypassed in some way, this is referred to as broken authentication. This is such a common issue that broken authentication is an entry in the Open Web Application Security Project (OWASP) top ten web application vulnerabilities list.
Let’s start...
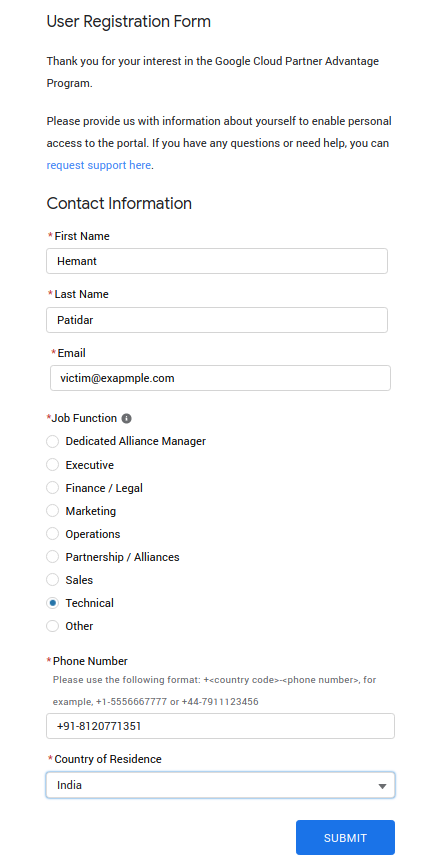
Let's get straight to the bug. When I was trying to do signup using the User Registration Form I notice that when someone does the registration process, the system does not verify the registered email. Also when we do that the user will get a verification email to verify and if the victim clicks to verify then the new detail will be updated into the victim account.
Summary: Insufficient Security Configurability | Flaw in Authentication
Steps-To-Reproduce:
- Go to the https://www.partneradvantage.goog/ and click on Register as a new partner portal user.
- Now fill all the details. (i.e. Victim email, which is already registered and the rest of the detail which you want to update in the victim’s account.) and click to submit.
3. Now the victim will receive an email to verify and if he clicks to verify then the above-entered details will get change in the victim account.

4. Boom! You have changed the details in someone else account.
Attack scenario:
The system does not verify the registered email when entered by someone else. Consider the impact of the business if data can be modified and control of the account assumed, other than that the impact of this is that attacker can fill in the data first before the original account owner enters the system.
Timeline:
Jul 20, 2020 - Bug Reported to Google
Jul 21, 2020 - Status changes to Won’t Fix (Not Reproducible) | Explained how to reproduce the bug and Impact
Aug 3, 2020 - Accepted (reopened) ❤
Aug 10, 2020 - Bounty Awarded $500

So, this was my first bounty from Google. I have reported other minor issues and got Hall Of Fame.

Thanks for reading :)
Happy Hacking ;)
You can see many writeups coming up…
LinkedIn: linkedin.com/in/HemantSolo
Website:- hemantpatidar.me
Twitter:- twitter.com/HemantSolo
Instagram:- instagram.com/hemant_solo
