Member-only story
How I uncover an IDOR led to access Private CV
Free Read
Hello everyone! Today, I’m excited to share how I discovered an IDOR vulnerability in one of the private programs. Let’s dive right in.
I began my bug hunting routine by enumerating subdomains using the subzy tool to check for subdomain takeovers. After that, I ran waybackurls to gather URLs and proceeded to use the httpx tool to identify interesting domain titles.
During this process, I came across a domain titled “Target Test Portal.”
I immediately visited the page and noticed a signup option. Without wasting time, I signed up for an account. After confirming my account and logging in.
I noticed something interesting:The server’s response contained my email, username, and JWT token, all encoded with my user ID. Surprisingly, there were no additional protections such as secure cookies.
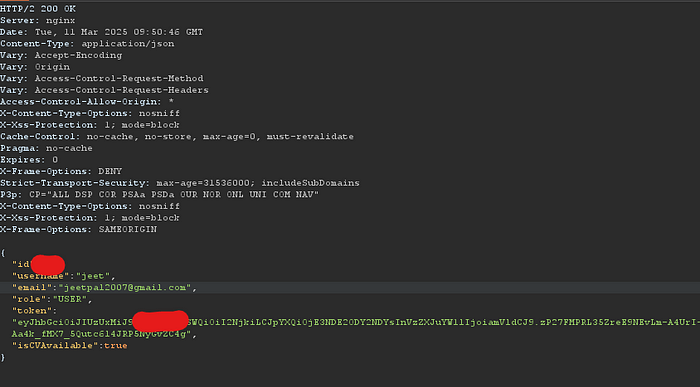
I created a second account to test further. Just like before, this account’s JWT token also followed the pattern of email + userID + username.
Next, I explored my profile section and noticed an option to upload a CV. Initially, I attempted various…

