LetsDefend — PCAP Analysis — Challenge — [Write-Up]
A step-by-step guide to completing the challenge
PCAP Analysis
We have captured this traffic from P13’s computer. Can you help him?
Before we even get started, observe the description of challenges for any hints, what can you gather from this one?
P13 — This is inferred as the name of the user, something we can pivot on or use to start the investigation
Connect to the lab environment in your browser and open the challenge file in Wireshark — just open the location of the file and double click it.
Questions
1. In network communication, what are the IP addresses of the sender and receiver?
Using the hint of the description we want to look into the user P13. So the question is going to be referring to traffic between P13 and something else. We can use my favourite Wireshark search filter with the username:
frame contains P13
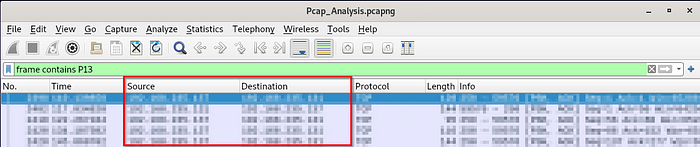
You should find the answer with this search, pay attention to the flag format: SenderIPAddress,ReceiverIPAddress
What we know:
- P13 is the username
- P13's source address
2. P13 uploaded a file to the web server. What is the IP address of the server?
Based off what we know, we can prepare a filter that should narrow down this scope. We can right-click on the SOURCE tab and apply this IP address as our next filter.
This still doesn’t give us an answer, but again we can use the question to give us a hint on what to look for .
“… uploaded a file”
I don’t blame you if you don’t know this, but this indicates to me that for a file upload to occur to a web server, the connection method is going to be a POST request rather a GET request. If I’ve lost you, I encourage you to read into HTTP Methods before we move on.
We can add this search for a POST request into our filter by using boolean which we will use andor && alongside my favourite filter frame contains
ip.src == [REDACTED] and frame contains POST
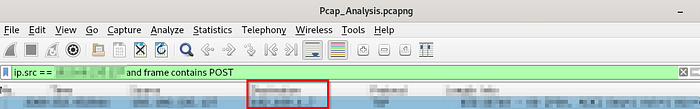
What we know:
- P13 is the username
- P13’s source address
- The IP of the webserver
3. What is the name of the file that was sent through the network?
Luckily we can stay right where we are for this one, have a look into the TCP stream of this traffic via right-clicking the line and following the TCP stream.
You should be presented with this now.
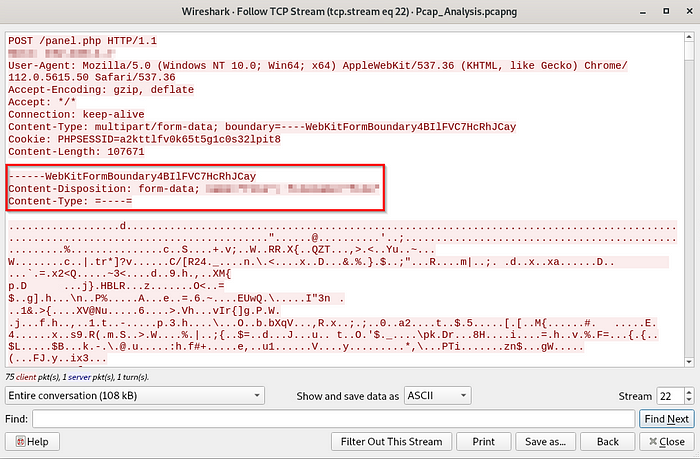
You will find the answer within this HTTP Header.
What we know:
- P13 is the username
- P13’s source address
- The IP of the webserver
- The name of the file that was uploaded
4. What is the name of the web server where the file was uploaded?
Keep the TCP stream open and scroll down to see the server response, it should look like this.

You will find the answer within this page.
What we know:
- P13 is the username
- P13’s source address
- The IP of the webserver
- The name of the file that was uploaded
- The name of the server that the file was uploaded to
5. What directory was the file uploaded to?
Using the exact same information in the TCP stream from the previous question will lead us to the answer for this question.

What we know:
- P13 is the username
- P13’s source address
- The IP of the webserver
- The name of the file that was uploaded
- The name of the server that the file was uploaded to
- The directory the file was uploaded to
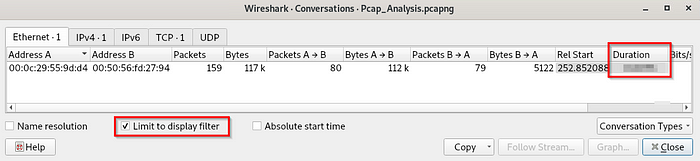
6. How long did it take the sender to send the encrypted file?
This is where we can get lost in the menus of Wireshark, this is where as a cyber professional you resort to a good ol google search for something like:
“wireshark finding duration of packets”

Lets do just that — remember the question is asking specifically for the duration of the packets for the file sending, by default Wireshark will show us EVERYTHING, so be sure to tick the box at the bottom that says “Limit to display filter” and it should look something like this:
ROOM COMPLETED
If you found this helpful, or if you found alternate methods to doing this challenge let me know in the comments below — theres more than one way to skin a cat






![[Blue Team Labs Online Write-up] Nonyx](https://miro.medium.com/v2/resize:fit:679/0*aYYHSGAcieHtzlhT.png)
