Malware Analysis : HTB Sherlock OpSalwarKameez24–1: Super-Star

Sherlock Scenario
StoreD Technologies’ customer support team operates tirelessly around the clock in 24/7 shifts to meet customer needs. During the Diwali season, employees have been receiving genuine discount coupons as part of the celebrations. However, this also presented an opportunity for a threat actor to distribute fake discount coupons via email to infiltrate the organization’s network. One of the employees received a suspicious email, triggering alerts for enumeration activities following a potential compromise. The malicious activity was traced back to an unusual process. The Incident Response Team has extracted the malicious binaries and forwarded them to the reverse engineering team for further analysis. This is a warning that this Sherlock includes software that is going to interact with your computer and files. This software has been intentionally included for educational purposes and is NOT intended to be executed or used otherwise. Always handle such files in isolated, controlled, and secure environments. One the Sherlock zip has been unzipped, you will find a DANGER.txt file. Please read this to proceed.
First of this challenge you need to download the sample malware from the HTB platform, inside the folder you will get the instructions.

Start the Analysis!
Unzip the file then we get the Electron-Coupon.exe , validate this file to virustotal, you will the the file flag as malicious.



As you can see, the malicious files is related to another files,IP and domain, you can more deep down to analysis each file that correlated to this malware, to get more big picture how the malware was operated in real case.
Next step is to answer all the challenge question.
- What is the process name of malicious NodeJS application?
To answer this question we need to do some analysis to get to know how the malware behavior in the runtime, thanks to this comprehensive analysis from the Joe-sandbox, based on this analysis we can get visibility this malware on runtime.

2. Which option has the attacker enabled in the script to run the malicious Node.js application?
In Electron, the WebPreferences object is used to configure and control how a BrowserWindow or WebView behaves. It allows you to set various properties and behaviors for the web content loaded within a window or web view.

on this task we need focus on this configuration nodeIntegration because this configuration affected integration in the renderer process. Electron determines whether Node.js APIs are available in the renderer process. By default, nodeIntegration is set to false for security reasons, as enabling it allows full access to Node.js APIs like require, fs, and others, which can pose security risks if the web content is not properly sanitized.
3. What protocol and port number is the attacker using to transmit the victim’s keystrokes?
Now we will examined the how this malware steal the data, this malware steal the keystroke data, it means stealing data from what you typing on keyboard.
deep analysis the malware, how the foldering structure and read the source code, you can find keystroke.js file. this file wrapped inside the .asar file (Atom Shell Archive) is a file format used in Electron applications to package application source code, assets, and resources into a single archive.
first we need unpack the .asar file and find the keystroke.js inside the public directory.

as we can see on the keystroke.js the protocol that using by attacker is Websocket and the port is 44500

below we can deep digging from the network perspective.

4. What XOR key is the attacker using to decode the encoded shellcode?
if you inspect the network pcap, there is an interesting information that request from this IP 15.206.13.31. that string is the XOR key!

5. What is the IP address, port number and process name encoded in the attacker payload ?
examined the preload.js there was a suspicious encoded base64 string that possible shellcode that we looking for.

if you trying to decoded and XOR it by the key, you will find the Reverse Shell payload.

6. What are the two commands the attacker executed after gaining the reverse shell?
To get this information we need deep dive analyze the pcap file, if scope the traffic that in out from this IP 15.206.13.31, we will quick spotted the traffic.

7. Which Node.js module and its associated function is the attacker using to execute the shellcode within V8 Virtual Machine contexts?
back to the preload.js we can easly spot that this possible module and function to execute the shellcode within V8 Virtual Machine contexts.

8. Decompile the bytecode file included in the package and identify the Win32 API used to execute the shellcode.
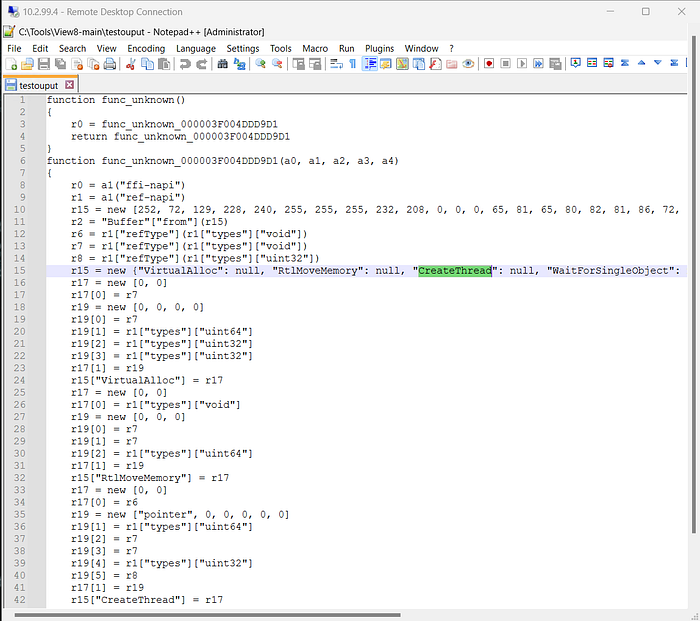
decompile the script.jsc we will get the decompiling code that tell us the windows api that used in this bytecode. in this case we using tools View8 to decompile the bytecode.

analyze the decompiled code, there is a few Win API on the list. on this case “CreateThread” the Win API that execute the shellcode.
9.Submit the fake discount coupon that the attacker intended to present to the victim.
From file that we decompiled before, there is some interesting data that executed by “CreateThread” Win API, which means this is the shellcode. We need further investigation to extract the information from this data. Next step in to do some static analysis to this data, convert it into .bin for more easy to put it into another static analysis tools.
This is the python code to convert the shellcode into a .bin for further analysis.
shellcode = [
252, 72, 129, 228, 240, 255, 255, 255, 232, 208, 0, 0, 0,.....
]
with open("shellcode.bin", "wb") as f:
f.write(bytearray(shellcode))
when we open the shellcode.bin using hexdump, the coupon code will easily spotted.






![Maldev : [Evasion] Shellcode Injection and Fileless Execution](https://miro.medium.com/v2/resize:fit:679/1*NDzRNgdfpnmZ_mHscyI06Q.png)


