Malware Analysis [#1]- NanoCore Rat

In this series of write-ups/articles of Malware analysis I will pick up a random sample from Malware Bazaar https://bazaar.abuse.ch/ , and I will Analyze it without knowing what it is, (BlackBox) approach.
let’s begin…
Our sample of today: md5(5846c3588fbcf6a5078b7a2413da0345).
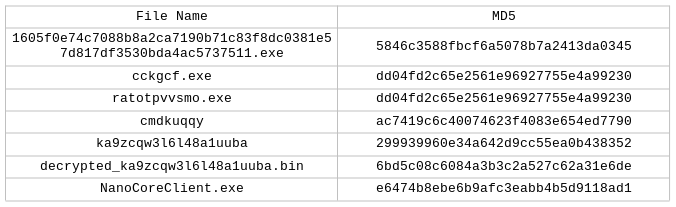
Malware Composition:
The Sample consists of the following components:

Static Analysis of 1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511.exe:
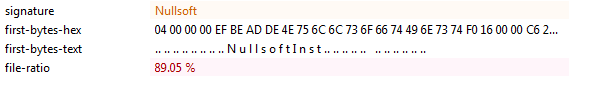
Uploading the sample to PEStudio we see that it is 32-bit executable with high entropy and using NSIS (Nullsoft Scriptable Install System) -which is a professional open source system to create windows installers- to drop/rewrite a new file/executable also it has a very old compiling date which is probably fake, I faced a sample of ghost malware not while ago is using the same technique for installing the malware component:


When decompressing NSIS package we get 4files one executable two might be a shell codes or encrypted files lastly we have the NSIS script:
Dynamic Analysis of 1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511.exe:
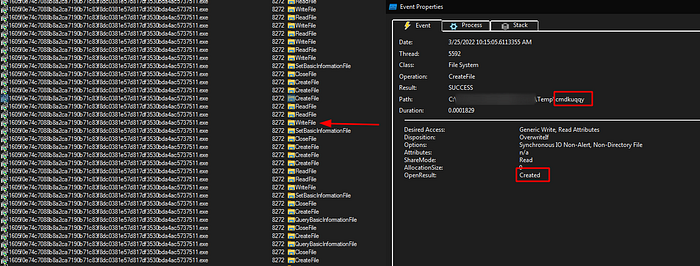
Running this sample we found that it is creating three files in the %TEMP% folder and then write to each file, also creating a folder in the %TEMP% folder with random name each time and keep it empty :
- ccgkcf.exe.
- ka9zcqw3l6l48a1uuba.
- cmdkuqqy.
- ns*****.tmp . (the last five letters keep changing each time it is executed)

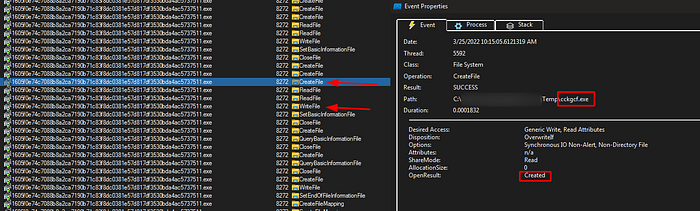
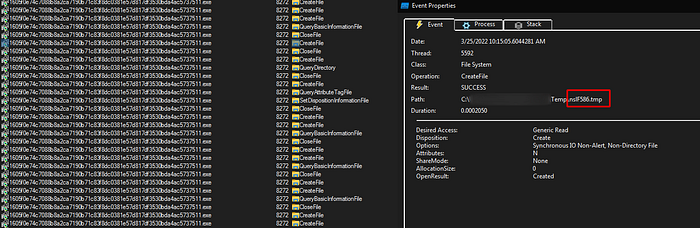
Under the debugger we can see that it is creating a new process with command line to start “ccgkcf.exe” and with file “cmdkuqqy” as an argument then exit the process:
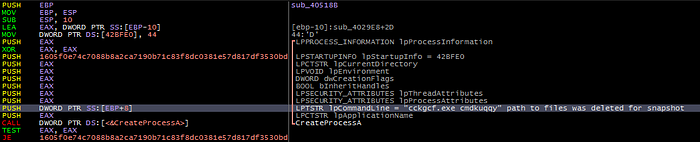
Static Analysis of ccgkcf.exe:

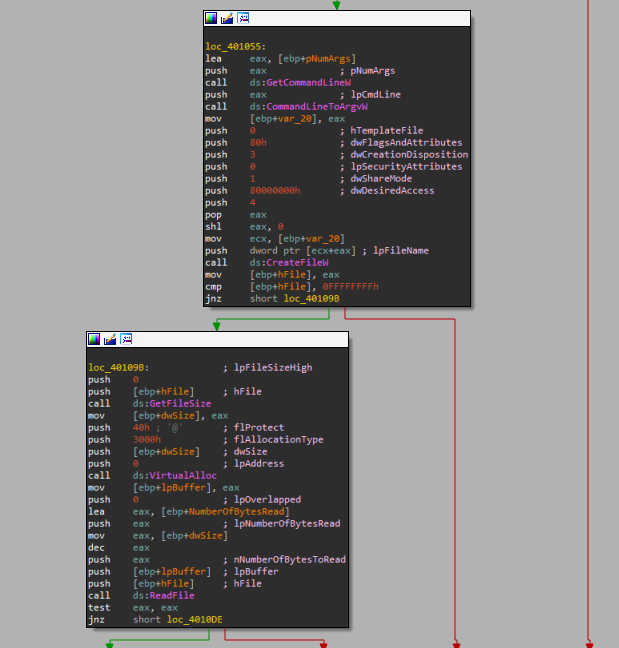
It is a 32-bit executable with new compiling and debugging date, uploading it to IDA we see that it is getting command line argument and try to open a file with “CreateFileW” and if the function fails it will exit, if it succeed it will get file size, allocate memory for that file and read it then proceed to decrypt the data that was read from the file and then jump to it which mean that it is a shell-code:
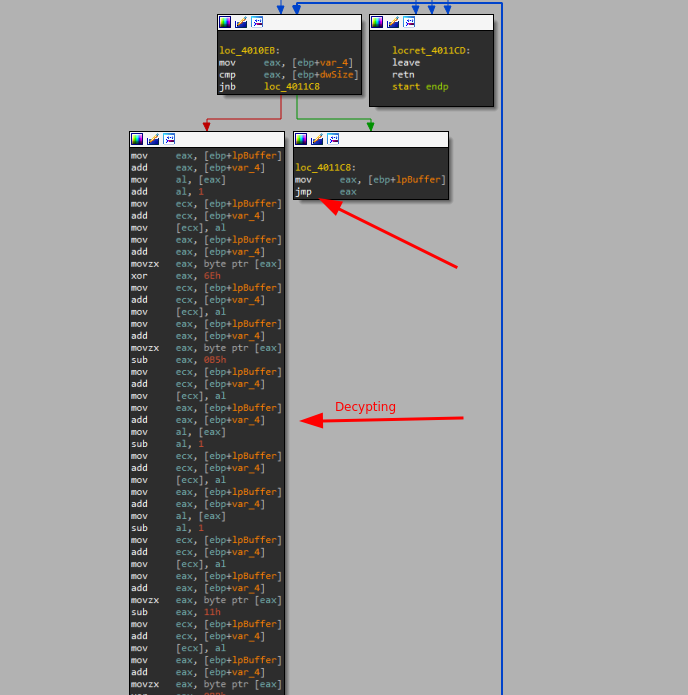
Dynamic Analysis of ccgkcf.exe:
As mentioned before when running this instance without any argument the process will exit and no action will be taken, but when adding the “cmdkuqqy” as an argument as we saw the installer did when creating a new process, the sample continue it’s work by opening the “cmdkuqqy” file get it’s size read it and decrypt it and at last handle the execution to the shell-code :




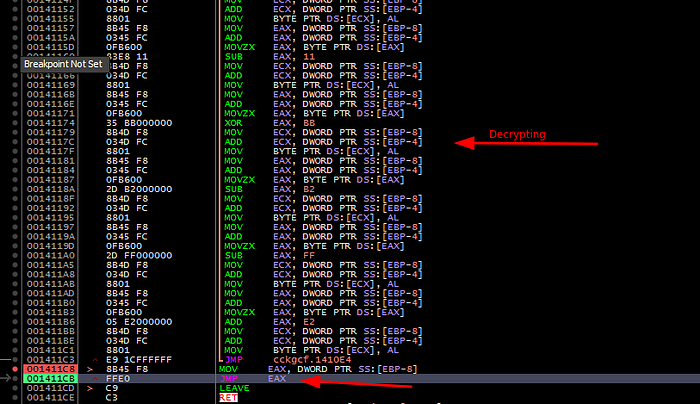
The shell-code start by loading libraries and importing modules then it pushes the below names letter by letter to memory:
- ka9zcqw3l6l48a1uuba.
- ratotpvvsmo.exe.
- gswccl.
- hhtktvn.
after that it opens “ka9zcqw3l6l48a1uuba” file from the %TEMP% folder to get handle of it then get the file size, allocate memory, read file and decrypt the data read from the file, so I dumped it to a file to be analyzed later:
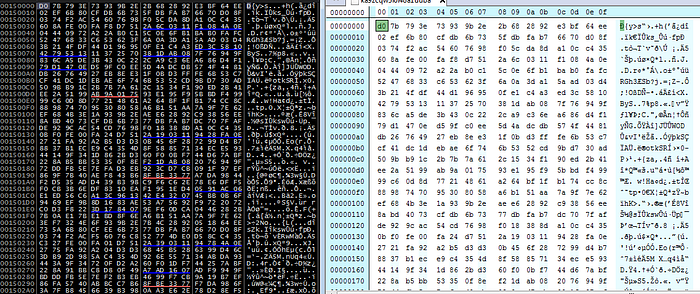

After that it creates a folder with name “gswccl” in “C:\<USER>\AppData\Roaming” and creates a file named “ratotpvvsmo.exe” in it and use this file as persistence technique by changing the auto run value in the registry “HKCU\SOFTWARE\Micorsoft\Windows\CurrentVersion\Run” with name “hhtktvn” :
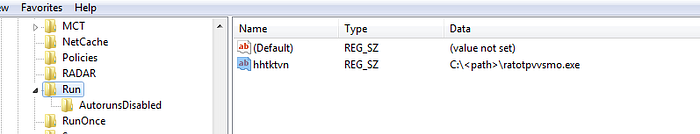
and by fast look at that “ratotpvvsmo.exe” we see that it is a copy of “ccgkcf.exe” executable:

Proceeding with the analysis we see that it create a new process with it’s name and inject the code the was decrypted from the “ka9zcqw3l6l48a1uuba” file to it and exit the process

What also worth to mention that it uses “Havens gate” technique which refer to far return, to switch to the 64bit mode, also It can be used as an anti reverse engineering technique for protecting the malware.
Static Analysis of ka9zcqw3l6l48a1uuba.decrypted:
Uploading this instance to PEStudio we see it is 32-bit executable with high entropy and a new compiling and debugging date also has an executable resource. From IDA we found that this instance will load executable file from resources and exit process.
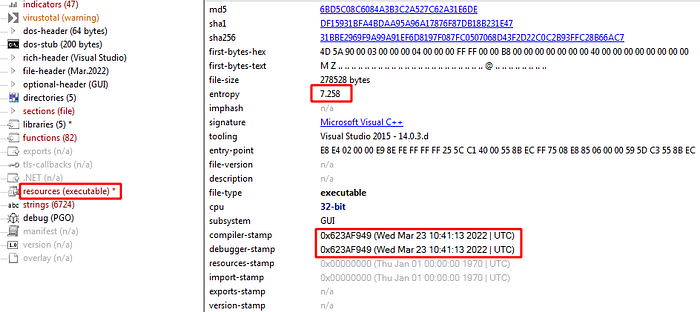
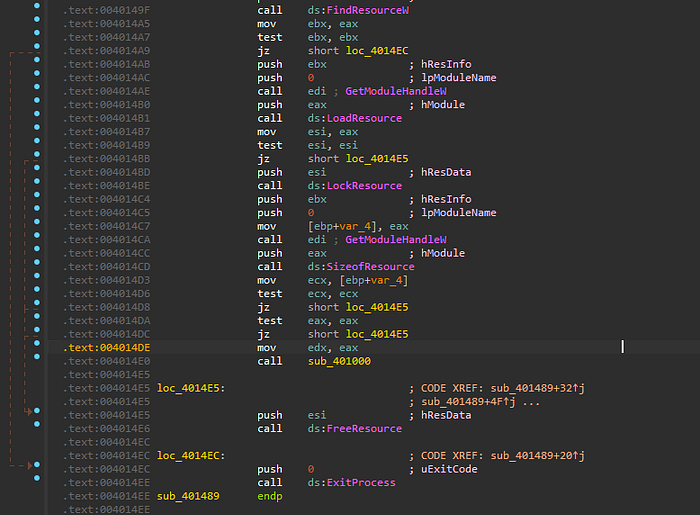
I used “ResourceHacker” to drop the resource file after checking it in x64dbg
Static Analysis of resource file (NanoCore Rat):
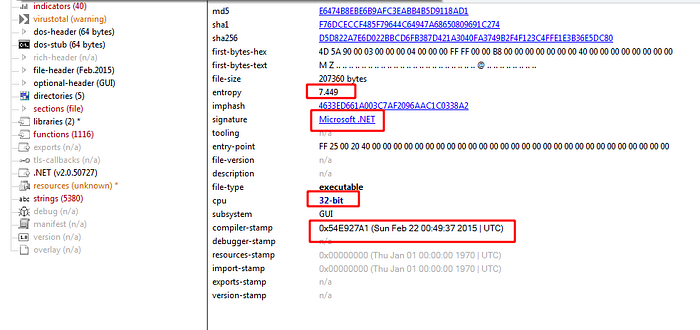
Uploading the resource file it appear that it is .NET executable file, and when looking at the imports or strings of this executable there is a big hashed imports list also the important thing is I found a NanoCore ascii string and when uploading the file to dnSpy we can see that it is heavily obfuscated:
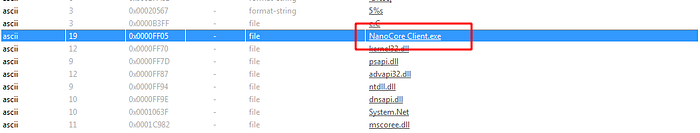

Dynamic Analysis of resource file (NanoCore Rat):
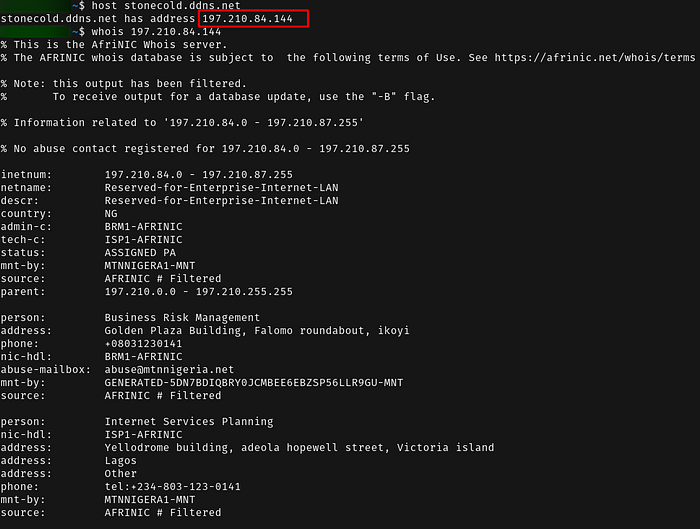
When running the NanoCore it creates a file “run.dat” in “<user>\AppData\Roaming\” folder . It also try to connect to C2 server, below is a snapshot of the DNS request and information about the domain:

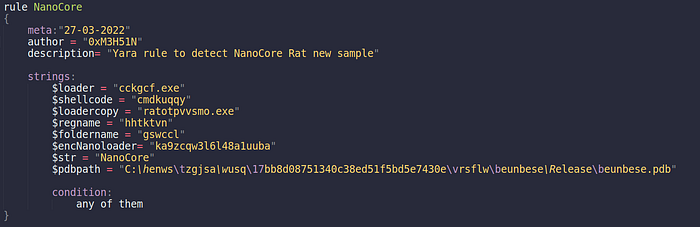
Yara Rule and Signature:
Anti-Reversing techniques:
- IsDebuggerPresent.
- Far return (heaven’s gate).
- Obfuscation.
Links:
- https://bazaar.abuse.ch/sample/1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511/
- https://www.virustotal.com/gui/file/1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511/detection/f-1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511-1648116728
- https://www.flaticon.com/free-icons/trojan"

