Modern Binary
Exploitation Writeups-0x02
This is the 2nd writeup of Tools and Basic Reverse Engineering by RPISEC, a subpart of Modern Binary Exploitation Course.
Link of lectures:- http://security.cs.rpi.edu/courses/binexp-spring2015/
All the lecture materials and other necessary files are available on the above link to check it out.
⬅️ Previous writeup__________________________________ Next WriteUp ➡️
crackme0x00b
Information gathering using the file command
$file crackme0x00b
Information gathering using the rabin2 tool.
$rabin2 -I crackme0x00b
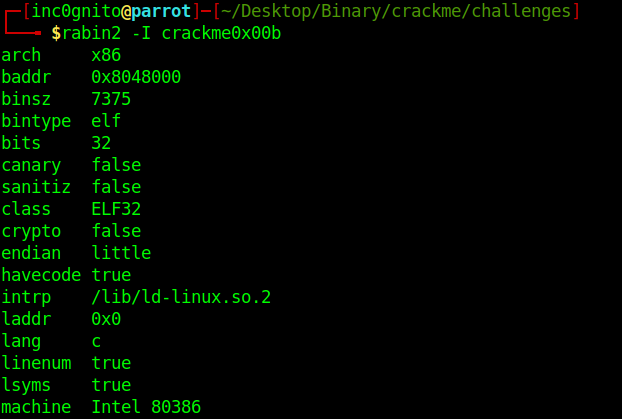
The given crack me is 32 bits and little endian, make a note of this it will help to find out the way to crack.
Cracking the file using strings
$strings -e L crackme0x00b


Cracking the file using xxd
$xxd crackme0x0b


Cracking the file using rabin2
$rabin2 -z crackme0x00b


Cracking the file using radare2
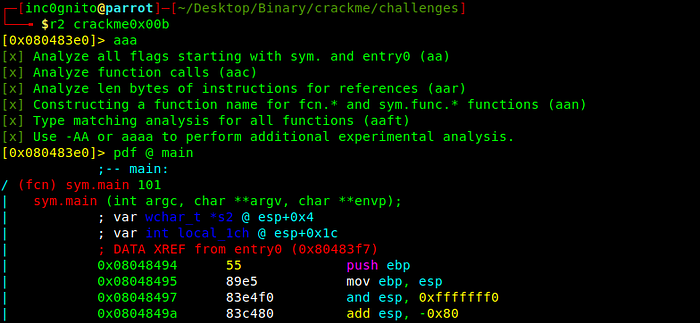
$radare2 crackme0x00a
[0x080483e0]> aaa
[0x080483e0]> pdf @ main- aa:-analyze all.
- aaa:- analyze all with more info.
- pdf:- print disassemble function.
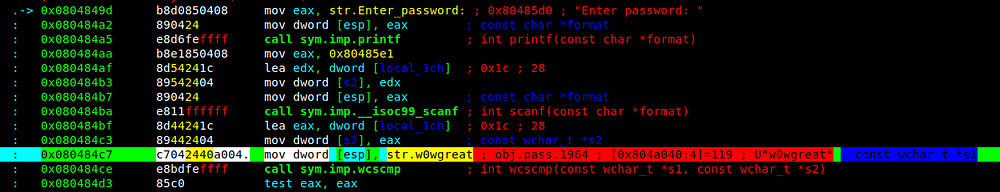
wcscmp() use *s1 and *s2 variable s1 is pointing to w0wgreat and s2 is the input strings.

Cracking the file using gdb-peda
gdb-peda is like an addon for gdb, you can install it from GitHub.
$gdb crackme0x00a
>gdb-peda$ disassemble maindisassemble main will show the main function of the binary.
gdb-peda$ break *0x080484ce
gdb-peda$ run
gdb-peda$ nini or nexti — execute calls as one instruction.

gdb-peda$ telescope $edxThe telescope view shows stack values, and also attempts to dereference pointers which may be pointed to by the stack.

There is one more way to do that above thing
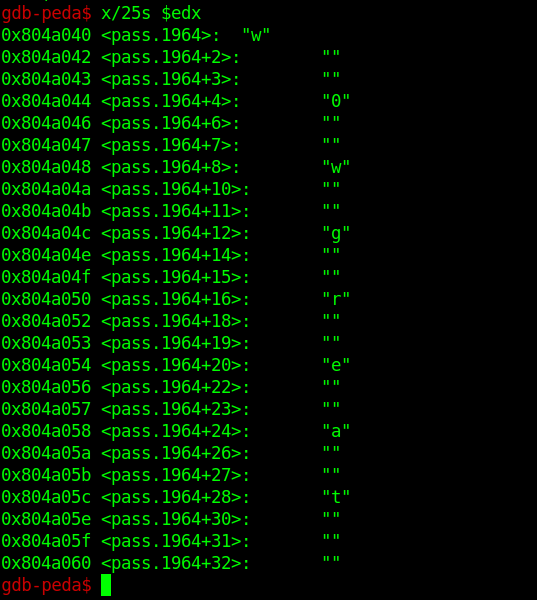
gdb-peda$ x/25s $edxx/ :- show bytes
25:- how many we want to show
s:- as a strings
$edx:- this refers to the register