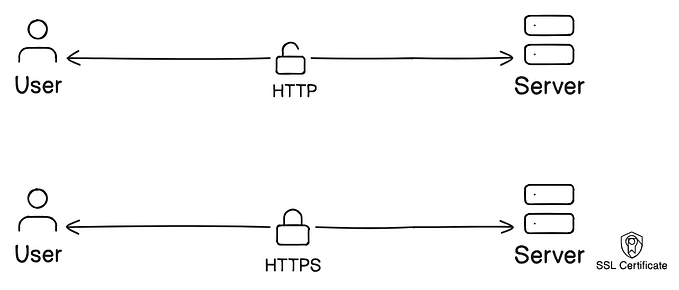
Open-redirection leads to a bounty
Hey guys Pratik this side. In this writeup, I’m going to share some of my open-redirection hunts and what resources I use to find open-redirection as well as how do I make its severity higher. So let’s hop into it.
What is an Open-redirection Vulnerability?
According to netsparker.com, “An Open Redirection is when a web application or server uses an unvalidated user-submitted link to redirect the user to a given website or page. Even though it seems like a harmless action to let a user decide on which page he wants to be redirected, such techniques if exploited can have a serious impact on the application security, especially when combined with other vulnerabilities and tricks”.
Open-redirections are the low hanging fruits. If you hunt for it
Some resources
https://twitter.com/jae_hak99/status/1279303602532528128
https://twitter.com/search?q=openredirection&src=typed_query
https://twitter.com/search?q=open%20redirection&src=typed_query&f=live
Some dorks
/{payload}
?next=
?url=
?target=
?rurl=
?dest=
?destination=
?redir=
redirect_uri=
?redirect_url=
?redirect=
/redirect/
cgi-bin/redirect.cgi?{}
/out/
/out?
?view=
/login?to=
?image_url=
?go=
?return=
?returnTo=
?return_to=
?checkout_url=
Common Parameters
dest, redirect, uri, path, continue, url, window, to, out, view, dir, show, navigation, Open, url, file, val, validate, domain, callback, return, page, feed, host, port, next, data, reference, site, html
What happens in open-redirection (Short Story)
Basically when the ?url=redirects-to-home but you insert your malicious place then the web page redirects to there.
Private Bug Bounty Story
I found 8+ open redirections on bugcrowd public and private programs but most of them haven’t patched yet so I don’t have the permission to share the the info for those bug but 2 bugs that are patched.
First case
Redacted.com using /// and then payload then webpage is redirect to payload.com
Like this
redacted.com///pratikdabhi.com — -> pratikdabhi.com

Second Case
Redacted.com/google/?dest_path=, here in place of path={}, I use javascript:alert() and changed its severity from P4 to P3
Like this
redacted.com/google/?dest_path=javascript:alert() — -> javascript popup
Url Based xss payloads
https://github.com/R0X4R/D4rkXSS
Open-redirection leads to SSRF (PortSwigger)
In the preceding SSRF example, suppose the user-submitted URL is strictly validated to prevent malicious exploitation of the SSRF behavior. However, the application whose URLs are allowed contains an open redirection vulnerability. Provided the API used to make the back-end HTTP request supports redirections, you can construct a URL that satisfies the filter and results in a redirected request to the desired back-end target.
For example, suppose the application contains an open redirection vulnerability in which the following URL:
/product/nextProduct?currentProductId=6&path=http://evil-user.net
returns a redirection to:
You can leverage the open redirection vulnerability to bypass the URL filter, and exploit the SSRF vulnerability as follows:
POST /product/stock HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 118
stockApi=http://weliketoshop.net/product/nextProduct?currentProductId=6&path=http://192.168.0.68/admin
This SSRF exploit works because the application first validates that the supplied stockAPI URL is on an allowed domain, which it is. The application then requests the supplied URL, which triggers the open redirection. It follows the redirection and makes a request to the internal URL of the attacker’s choosing.
*Solve the lab to get hands-on practice.
→ Lab solve
In the lab, we get 2 vulnerable params that are stockApi and path, where path has open-redirection and stockapi has ssrf vulnerability. First, we have to do some param spidering using burpsuite.

By clicking on check stock we get the stockapi param

After we get the param just send that request to the repeater.

To get path param we need to click on next product link.

Then we get our ?path= param send this request to repeater
Now copy the whole path /product/nextProduct?currentProductId=1&path=
Paste it on stockApi param. Like this stockApi=/product/nextProduct?path={here paste your given ssrf ip} for me its stockApi=/product/nextProduct?path=http://192.168.0.12:8080/admin
Then click on go wait sometime then you get the response scroll down and you get the path which you use to delete user Carlos.

Then just paste the path in stockApi (stockApi=/product/nextProduct?path=http://192.168.0.12:8080/admin/delete?user=carlos) param and click go and BOOM! Lab solved.
Impact of Open-redirection (AC PortSwigger)
The user may be redirected to an untrusted page that contains malware which may then compromise the user’s machine. This will expose the user to the extensive risk and the user’s interaction with the web server may also be compromised if the malware conducts keylogging or other attacks that steal credentials, personally identifiable information (PII), or other important data.
The user may be subjected to phishing attacks by being redirected to an untrusted page. The phishing attack may point to an attacker-controlled web page that appears to be a trusted web site. The phishers may then steal the user’s credentials and then use these credentials to access the legitimate web site.
hanks everyone for reading:)
Happy Hacking ;)
Support me if you like my work! Buy me a coffee and Follow me on twitter.
Website:- https://www.pratikdabhi.com/
Instagram:- https://www.instagram.com/i.m.pratikdabhi
Twitter:- https://twitter.com/impratikdabhi
Youtube:- https://www.youtube.com/impratikdabhi