Paginator v2- NullCon CTF 2025
Paginator v2 is a web challenge of the NullCon CTF 2025
Link for challenge: http://52.59.124.14:5015/

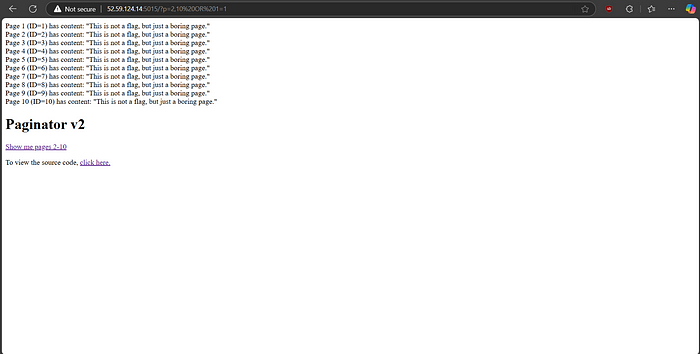
On accessing the link, I got a webpage like the one below:

On clicking “Show me pages 2–10”, it gives records of pages from ID 2 to 10.

Now, I checked the source code of this webpage.

Here, in the first try block, it executes a create table command and 10 insert commands. Unlike Paginator v1, where the flag was encoded as base64 string in the first record of pages table, here the flag is itself not in the pages table. So, basic SQL injection commands won’t work.
Therefore, I came to a conclusion that they might have made a new table related to it. So, I checked up on some union-based injection payloads. I guessed the name of the table to be “flag” and since I had no information on the no. of rows or the row in which the flag was present, I had to use an asterisk(*).
So, the payload became:
2,10 UNION SELECT * FROM flag
BINGO! I got the base64 encoded flag.
Now, I just had to decode it.

FLAG: ENO{SQL1_W1th_0uT_C0mm4_W0rks_SomeHow_AgA1n_And_Ag41n!}References:
1. SQL Injection Using UNION








