REvil — Incident Response with Redline

Recently, I’ve been doing some more study around incident response. To get some more practice, I decided to attempt the free TryHackMe room titled “REvil Corp”, created by heavenraiza and RussianPanda. This article presents my approach for solving this room using Redline and I have also provided a link to TryHackMe at the end for anyone interested in attempting this room.
Disclaimer
I like to add a brief disclaimer before a writeup to encourage people to attempt the room before reading this article, since there will obviously be spoilers in this writeup. I believe you will enjoy the CTF more if you attempt it yourself first and then come back to this writeup if you get stuck or need a hint. So without any further delay, lets get started!
Redline
Redline is a free endpoint security tool from FireEye that can be used to search for Indicators of Compromise (IoC) through memory and file analysis. Supplied with a set of IOCs, the redline portable agent is automatically configured to gather the data required to perform IOC analysis and an IOC hit result review. You can find out more about the Redline tool below and you can also find it’s user guide here.
Challenge Scenario
One of the employees at Lockman Group gave an IT department the call; the user is frustrated and mentioned that all of his files are renamed to a weird file extension that he has never seen before. After looking at the user’s workstation, the IT guy already knew what was going on and transferred the case to the Incident Response team for further investigation.
You are the incident responder. Let’s see if you can solve this challenge using the infamous Redline tool. Happy Hunting, my friend!
Investigating the Compromised Endpoint
1. What is the compromised employee’s full name?
After loading the Mandiant Analysis File called AnalysisSession1, I navigated to “Analysis Data > Users” to identify the different users present on the compromised host. Here I can see the employees full name:

2. What is the operating system of the compromised host?
To find the operating system of the compromised host, we can navigate to “Analysis Data > System Information” and look at the Operating System Information:

3. What is the name of the malicious executable that the user opened?
Based on the room’s title and challenge description, it appears that the compromised host has been infected by REvil Ransomware. Doing some research online, I found this article by Secureworks:
Reading through the article, I learnt that as part of the ransomwares delivery, the threat actors leveraged a strategic web compromise (SWC) to deliver REvil by compromising the Italian WinRAR website and replacing the WinRAR installation executable with an instance of the malware. The SWC resulted in the infection of unsuspecting WinRAR customers’ systems.
In Redline, I navigated to “Analysis Data > Filesystem” and found the WinRAR malicious executable that the user opened:
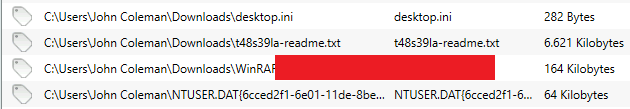
4. What is the full URL that the user visited to download the malicious binary? (include the binary as well)
In Redline, I navigated to “Analysis Data > File Download History” and found the source URL used to download the malicious binary:

5. What is the MD5 hash of the binary?
To find the MD5 hash of the malicious WinRAR binary, we can navigate to “Analysis Data > Filesystem” in Redline and double click on the WinRAR entry to get more details, such as it’s file hashes:

6. What is the size of the binary in kilobytes?
To find the file size of the malicious WinRAR binary, we can navigate to “Analysis Data > Filesystem” in Redline and double click on the WinRAR entry to get more details, such as it’s file size:

7. What is the extension to which the user’s files got renamed?
According to the SecureWorks article above, REvil checks the Software\recfg registry key for the presence of the rnd_ext value. This value contains the random extension generated at runtime that is appended to encrypted files. If this registry value does not exist, the malware generates a random string of lowercase letters (a-z) and numbers (0–9) ranging from five to ten characters in length (inclusive) and preceded by a period (e.g., .9781xsd4).
In Redline, I navigated to “Analysis Data > Filesystem” and saw a random looking file extension similar to the description and example above:

8. What is the number of files that got renamed and changed to that extension?
To determine the number of files that got renamed and changed to the extension identified in question 7, I navigated to “Analysis Data > Timeline” and filtered for the extension in the Summary column:

9. What is the full path to the wallpaper that got changed by an attacker, including the image name?
Referring to SecureWorks, if the encryption process is successful, REvil changes the desktop background to make the victim aware of the compromise. REvil saves the image to the host’s %Temp% directory using a random filename consisting of lowercase letters and numbers between 3 and 13 characters in length appended with the “.bmp” extension (e.g., C:\Users\<user>\AppData\Local\Temp\cd2sxy.bmp).
In Redline, I navigated to “Analysis Data > Timeline” and then filtered for any files with a .bmp extension. I found a file that matched the description provided by SecureWorks:

10. The attacker left a note for the user on the Desktop; provide the name of the note with the extension.
In Redline, I navigated to “Analysis Data > File System” and found the note left by the attacker on the users Desktop:

11. The attacker created a folder “Links for United States” under C:\Users\John Coleman\Favorites\ and left a file there. Provide the name of the file.
In Redline, I navigated to “Analysis Data > File System” and found the file left by the attacker under “C:\Users\John Coleman\Favorites\”:

12. There is a hidden file that was created on the user’s Desktop that has 0 bytes. Provide the name of the hidden file.
In Redline, I navigated to “Analysis Data > File System” and searched for a file with 0 bytes:

13. The user downloaded a decryptor hoping to decrypt all the files, but he failed. Provide the MD5 hash of the decryptor file.
In Redline, I navigated to “Analysis Data > File System” and saw a file called “d.e.c.r.yp.tor.exe”. I double clicked on this entry and saw the MD5 hash:

14. In the ransomware note, the attacker provided a URL that is accessible through the normal browser in order to decrypt one of the encrypted files for free. The user attempted to visit it. Provide the full URL path.
Reading through the SecureWorks article, The ransom note instructs the victim to use a unique URL to decrypt their files. The website offers a trial decryption to prove that the victim can decrypt the files, as seen in the image below:
Looking at the image, I can see the word “Decryptor” is used as part of the unique URL. In Redline, I navigated to “Analysis Data > Browse URL History” and filtered for the keyword “Decryptor”:

15. What are some three names associated with the malware which infected this host? (enter the names in alphabetical order)
I already know that the host was compromised by REvil ransomware. To find the two other names for the ransomware family, I used the MITRE ATT&CK website and referred to the associated software for the REvil ransomware family.
Closing Remarks
I really enjoyed working through this room and getting the opportunity to learn more about incident response using the Redline tool from FireEye and the REvil Ransomware. Thank you for reading till the end and keep hacking 😄!

