Social Engineering: The Art of Psychological Exploitation (Part-2)
How do different website phishing attack works
Last time we discussed different social engineering attacks. Website Phishing is the most compulsory or common component in social engineering. The link to that Phishing page is attached or sent via different social engineering approaches. So designing and presenting it in such a way is essential to hook potential victims. Below is a list of various web phishing tactics that are yet effective.

- Homograph Attack
- Address Bar Spoofing
- Fake Pop-up Login
- Browser-in-the-browser Attack
- Typosquatting
- SSL/TLS Spoofing
- Search Engine Poisoning
- QR Code Phishing
- Malicious Redirects
- Full-Screen Mode Phishing
- Fake Mobile Apps
- Utilizing One-click attacks
- SVG Phishing
- Subdomain TakeOver
- Browser Autofill Exploitation
- Rogue Extension
- Fake CAPTCHA
- Browser Fingerprinting
- Man-in-the-middle Attack
- Man-in-the-Browser Attack
Address Bar Spoofing
Address bar spoofing is a technique used by attackers to manipulate the browser’s address bar to display a URL that appears legitimate, while the user is actually on a malicious or deceptive website. This attack exploits vulnerabilities in browsers, JavaScript, or other web technologies to make users believe they are interacting with a trusted site.
The goal of address bar spoofing is to deceive users into entering sensitive information (e.g., login credentials, credit card details) on a phishing site or performing actions they wouldn’t otherwise take. There are again various methods to achieve address bar spoofing.
Homograph Attack
A homograph attack is a type of phishing or spoofing attack that exploits the similarity between characters in different scripts or alphabets to create domain names that visually resemble legitimate ones. The goal is to deceive users into believing they are visiting a trusted website when, in reality, they are interacting with a malicious site.
For example: A legitimate domain: https://www.google.com
A spoofed domain: https://www.gооgle.com (using Cyrillic “o” instead of Latin “o”).
The spoofed domain appears identical to the legitimate one but resolves to a different IP address controlled by the attacker.
URL padding
URL padding is a malicious technique used by cybercriminals to disguise fraudulent URLs, particularly targeting mobile users. Attackers insert extra characters, hyphens, or deceptive subdomains into a URL to make it appear legitimate.
https://www.google.com%20%20%20%20%20@malicious-site.com
Tabnabbing
Tabnabbing is a type of phishing attack that takes advantage of users who have multiple browser tabs open. The attack works by manipulating an inactive browser tab to change its appearance, often disguising it as a legitimate website (such as a login page for a bank, email service, or social media platform). When the user returns to the tab, they may be tricked into entering sensitive information, such as usernames and passwords, thinking they are interacting with a trusted site. If developers fail to use rel=”noopener noreferrer” in their external links, tabnabbing takes place.
Favicon Spoofing
Favicon spoofing is a type of phishing attack where an attacker manipulates the favicon (the small icon displayed in the browser tab next to the page title) to deceive users into believing they are on a legitimate website.
Subdomain Spoofing
Subdomain spoofing refers to the tactic where attackers craft a URL that appears to include a trusted domain as a subdomain, misleading users about the site’s true identity. google.com.phishing-site.com can be an example. This technique is particularly effective on mobile browsers, as their address bars are too small to display the full URL.
If you want to study more about address bar spoofing, then you can read Rafay Baloch’s blog or book.
Fake Pop-up Login
A fake pop-up login is a common phishing technique where attackers display a fraudulent login window that mimics a legitimate service (e.g., email providers, banks, or social media platforms). The goal is to trick users into entering their credentials, which are then captured by the attacker. These fake login pop-ups often appear as part of a larger phishing campaign and can be highly convincing due to their resemblance to real login interfaces. Here is an article which describes the attack very well.
Browser-in-the-browser Attack
It is similar to a fake pop-up login like the above. A Browser-in-the-Browser (BiTB) attack is an advanced phishing technique that exploits the trust users place in browser interfaces. In this attack, a malicious actor creates a fake browser window within the actual browser, mimicking legitimate login pages or websites. This makes it extremely difficult for users to distinguish between the fake and real browser windows, as the attacker can replicate all visual elements of a legitimate website, including URL bars, security indicators (e.g., HTTPS padlocks), and favicons.
Typosquatting
Typosquatting (also known as URL hijacking or domain squatting) is a cyberattack tactic where attackers register domain names that are intentionally misspelled or slightly altered versions of legitimate, popular website URLs. The goal is to exploit common typing errors users make when entering web addresses, redirecting them to fraudulent or malicious sites. Such as-
- goggle.com (extra ‘g’ instead of o)
- face-book.com (hyphen in the middle)
- amaz0n.com (‘0’ instead of ‘o’)
- twiter.com (a ‘t’ before ‘e’ is missing)
- apple.net (using alternative TLD, .net instead of .com)
- www-tesla.com (hyphen after “www” instead of dot)
SSL/TLS Spoofing
SSL/TLS Spoofing refers to a type of attack where an attacker attempts to forge or impersonate a valid SSL/TLS certificate to deceive users into thinking they are communicating securely with a trusted website. It exploits weaknesses in the SSL/TLS protocol or certificate validation mechanisms, allowing the attacker to establish a secure (but fake) connection between the user and a malicious server. Services like Let’s Encrypt allow attackers to easily obtain valid SSL certificates for phishing domains (e.g., paypa1-security.com). Users see a padlock icon and assume the site is safe. 58% of the Phishing websites now uses HTTPS according to ‘The SSL Store’.
Search Engine Poisoning
Search Engine Poisoning (SEO poisoning) is a cyberattack technique where attackers manipulate search engine results to promote malicious websites, often disguised as legitimate ones, to trick users into visiting phishing pages, downloading malware, or revealing sensitive information. This method exploits users’ trust in high-ranking search results and leverages SEO tactics to hijack visibility. Here is a news article about a real incident of this attack.

QR Code Phishing
QR code phishing, or “quishing,” has emerged as a sophisticated social engineering tactic where attackers use QR codes to redirect victims to malicious sites, steal credentials, or deploy malware. Because QR codes offer a quick, frictionless way to access web content, many users scan them without scrutinizing the underlying URL. Attackers take advantage of this by crafting QR codes that appear innocuous, while the URL they encode is designed to deceive. It is particularly effective from in-app browsers.

Malicious Redirects
Malicious redirects are a common technique used in phishing attacks where attackers manipulate users into being redirected from a legitimate website to a fraudulent or malicious site. These redirects often occur without the user’s knowledge or consent, making them a highly effective method for stealing sensitive information, distributing malware, or conducting other malicious activities. It is typically done by link shortening or exploiting open redirect vulnerability. The payload for open redirect vulnerability looks somewhat like this: https://legitimate.com/redirect?=https://evil.com
Full-Screen Mode Phishing
Full-screen Mode Phishing is a sophisticated phishing technique where attackers use the browser’s full-screen mode (or simulate it) to create a deceptive environment that mimics a legitimate application or operating system interface. This method is designed to trick users into believing they are interacting with a trusted system, such as a login screen, payment gateway, or security prompt, when in reality, they are entering sensitive information into a malicious website or application.
By leveraging the full-screen mode, attackers can hide visual cues that might otherwise alert users to the scam, such as the browser’s address bar, tabs, or other indicators of authenticity. This makes the attack highly convincing and difficult to detect. Although it requires a slight user interaction to enable full-screen.
Fake Mobile Apps
Fake mobile apps designed for phishing are malicious applications that mimic legitimate apps to trick users into providing sensitive information such as login credentials, credit card details, or other personal data. These apps often look identical or very similar to trusted apps, making it difficult for users to distinguish between the real and fake versions. These apps are typically distributed through phishing sites or third-party app stores. Fake mobile apps are often more effective than traditional phishing sites because users do not see the forged domain that is trafficking their credentials. You frequently come across reports in cybersecurity news about fraudulent apps on the Play Store that steal user data.
Utilizing One-click Attacks
One-click attacks like XSS, CSRF, clickjacking, and session fixation can be weaponized for phishing by exploiting user trust and technical vulnerabilities with minimal interaction. For instance, XSS injects malicious scripts into legitimate sites to redirect victims to phishing pages or overlay fake login forms directly on trusted domains, while CSRF silently triggers unauthorized actions (e.g., changing account details) and redirects users to phishing sites to harvest credentials. Clickjacking embeds a target site in an invisible frame, overlaying a deceptive UI to trick users into clicking hidden elements, such as submitting sensitive data to an attacker’s server. Session fixation lures victims into authenticating with a predetermined session ID, allowing attackers to hijack their active sessions post-login. These attacks often combine social engineering (e.g., urgent “account verification” emails) with technical exploits, requiring just a single click to trigger data theft or account compromise.
SVG Phishing
SVG (Scalable Vector Graphics) phishing exploits the inherent scripting capabilities of SVG files to execute malicious code, bypass security controls, and steal sensitive data.
How SVG Phishing Works:
- Embedding Malicious Content: SVG files can contain embedded scripts (like JavaScript) or hyperlinks. Attackers exploit this by embedding malicious code or links that redirect users to phishing sites.
- Evasion of Security Filters: Since SVG files are commonly used for images and icons, many email clients and web security solutions don’t scrutinize them as rigorously as other file types, allowing them to bypass filters.
- High Customizability: SVGs are highly customizable and can be manipulated to look like legitimate buttons, forms, or other interactive elements, making the phishing attempt more convincing.
- Obfuscation: Attackers can obfuscate malicious code within the SVG, making detection by security tools more challenging.
Subdomain TakeOver
Subdomain takeover occurs when attackers hijack unused or misconfigured subdomains. It can be used to host phishing content, leveraging the trust associated with legitimate domains. This technique has become a critical enabler of advanced phishing campaigns. Technically, it doesn’t appear to be phishing since the attacker is exploiting the genuine site itself to deceive its users. If you exploit subdomain takeover through broken link hijacking, it will be a form of reverse social engineering, making it a more sophisticated attack.
Browser Autofill Exploitation
Browser autofill exploitation is a phishing technique where attackers trick users into revealing sensitive information using the browser’s autofill feature. Here’s how it works:
How Browser Autofill Exploitation Works
1. Creating a Deceptive Form: Attackers design a webpage with visible input fields (like name and email) to make it look legitimate.
2. Hidden Fields: The form also contains multiple hidden input fields for sensitive information, such as credit card numbers, passwords, and addresses. These fields are styled to be invisible (using CSS like display:none, opacity:0, or positioning them off-screen).
3. Triggering Autofill: When the user clicks on one of the visible fields and the browser’s autofill is triggered, it populates not only the visible fields but also the hidden ones.
4. Data Exfiltration: The hidden fields capture the autofilled data, which is then sent to the attacker’s server upon form submission.
Rogue Extension
Rogue browser extensions are malicious or deceptive add-ons that appear legitimate but are designed to steal sensitive information, track user activity, or redirect users to phishing sites. These extensions exploit the trust users place in browser add-ons to carry out phishing attacks, often without the user realizing it. Rogue extensions can perform various activities. Such as, keylogging, malicious redirects, cookie stealing, and credential harvesting.
Fake CAPTCHA
Fake CAPTCHA phishing combines traditional CAPTCHA mechanisms with phishing tactics. Attackers design deceptive CAPTCHA challenges to trick users into divulging sensitive information or downloading malware.

How It Works:
- Deceptive Design: A fake CAPTCHA mimics legitimate tests (e.g., distorted text, image grids) but is embedded in a malicious site or phishing page.
- Information Harvesting: After solving the CAPTCHA, users may be prompted to “verify” their identity by entering passwords, credit card details, or signing in via social media.
- Redirection: Completing the CAPTCHA might redirect users to phishing pages impersonating trusted platforms (e.g., Google, Facebook) to steal credentials.
- Malware Distribution: Some fake CAPTCHA phishing schemes are designed to deliver malware to the victim’s device. For example, after completing the fake CAPTCHA, the user may be prompted to download a file that contains malware, or run malicious commands on PC.
Browser Fingerprinting
Browser fingerprinting is a technique used by attackers to collect detailed information about a user’s device and browser configuration. In phishing attacks, it helps cybercriminals create more convincing and targeted schemes. The information from browser fingerprinting serves multiple purposes:
- Tailoring the Phishing Experience: By knowing the victim’s exact browser environment, attackers can customize the look and behavior of their phishing page to closely mimic a legitimate website. This makes the spoofed site far more convincing.
- Bypassing Automated Defenses: Phishers often use fingerprinting to distinguish between real users and security crawlers or bots. They might show malicious content only when a genuine fingerprint is detected — reducing the risk of early detection by automated scanning systems.
- Spoofing for Authentication Bypass: In more advanced scenarios, attackers can collect a user’s fingerprint and then spoof it during a login process. Some recent studies have demonstrated that by replicating the expected fingerprint, an attacker might bypass risk-based authentication measures (like triggering two-factor authentication only when discrepancies are detected).
- Exploiting Security Vulnerability: An outdated browser version may lack essential security mechanisms, such as protection against address bar spoofing and lack of anti-phishing filter, which attackers can exploit.
Man-in-the-middle Attack
A Man-in-the-Middle (MiTM) attack occurs when an attacker intercepts and manipulates communication between a user and a legitimate service to steal sensitive information, such as login credentials. Unlike traditional phishing (which relies on deceptive links or fake emails), MiTM phishing exploits real-time interception, making it harder to detect.
Common Techniques
- Public Wi-Fi : Attackers intercept traffic on unsecured networks.
- DNS Spoofing : Redirect users to fake sites by manipulating DNS.
- SSL Stripping : Force HTTPS connections to use insecure HTTP.
- Malware : Use malicious software to intercept and modify traffic.
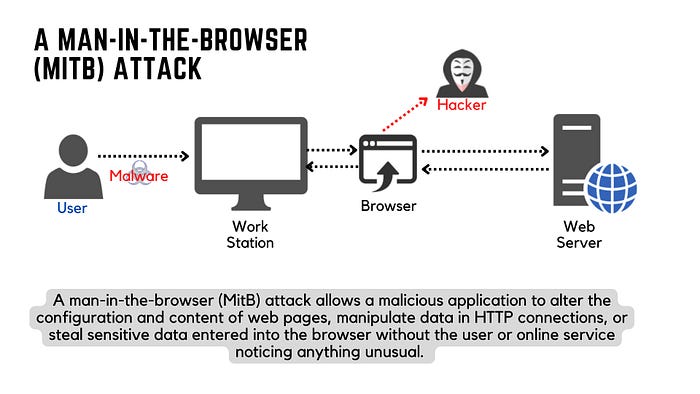
Man-in-the-Browser (MITB) Attack
A Man-in-the-Browser (MITB) attack is a type of cyberattack where an attacker exploits vulnerabilities in a web browser or its components, such as browser extensions or plugins, to intercept, modify, or inject malicious content into web traffic. This attack typically relies on malware, such as a Trojan, that infects the victim’s browser to manipulate data as it passes between the user and the websites they visit.
That’s all for today. The techniques I discussed are written from my personal experience and research. My efforts will be worthwhile if you benefit from them. See you again in the next part.

