Member-only story
SSRF Advanced Methodology✨
Free Article Link
By Abhijeet Kumawat, Jr. Security Consultant, Bug Bounty Hunter
What is SSRF? 🛡️🔥
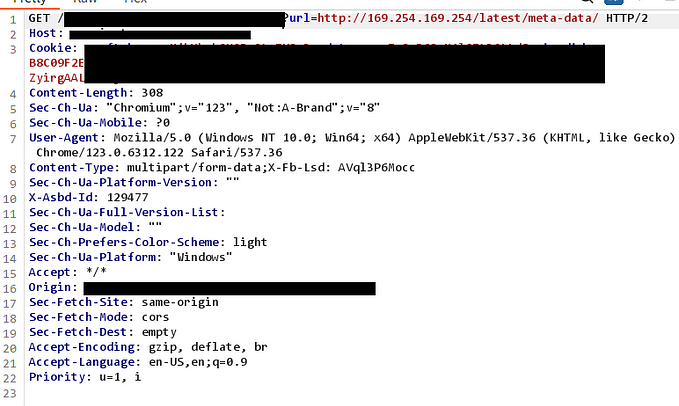
Server-Side Request Forgery (SSRF) allows attackers to manipulate a server into sending malicious requests, often bypassing firewalls to access sensitive data, cloud metadata, internal APIs, or internal networks. 🛠️💻

Why is SSRF Critical? ❓💥
- 🧱 Access internal services and hidden endpoints.
- ☁️ Obtain cloud instance metadata (AWS, GCP).
- 🕵️♂️ Perform internal network scans.
- 🧨 Exploit further by chaining SSRF with RCE.
Detailed SSRF Methodology 📚🔍
1. Subdomain Enumeration 🔍🗺️
- Tools: 🛠️ Subfinder, Amass, Assetfinder, CRT.sh, Chaos.
- Where to Find Bugs: 🐛 Look for internal subdomains like
dev.target.com,staging.target.com, orapi.target.com. Test staging environments as they often have misconfigured SSRF protections. - Commands: 🖥️
subfinder -d target.com -o subdomains.txt amass enum -active -d target.com -o amass_subdomains.txt chaos -d target.com -o chaos_subdomains.txt2. Live Domain Detection 🛠️🌐
- Tools: HTTPX, Httprobe, Naabu.
- Where to Find Bugs: 🔍 Services running on uncommon ports (e.g., 8080, 8443, 8888).
- Commands: 💻
cat subdomains.txt | httpx -threads 150 -silent -status-code -o live_domains.txt naabu -list live_domains.txt -p 80,443,8080,8443,8888 -o open_ports.txt3. URL Enumeration and Filtering 🔗🧵
- Tools: gauplus, Katana, Waybackurls, hakrawler.
- Where to Find Bugs: 📍 URLs with parameters like
?url=,?next=,?redirect=,?link=.