TryHackMe CTF Collection Vol. 1
A beginner-friendly CTF walkthrough (Part 1)

🏠 TryHackMe CTF Collection Vol. 1 (Official Website)
👉 TryHackMe CTF Collection Vol. 2 (My Write-up)
· First things first…
· Task 2: What does the base said?
· Task 3: Meta meta
· Task 4: Mon, are we going to be okay?
· Task 5: Erm……Magick
· Task 6: Qrrrr
· Task 7: Reverse it or read it?
· Task 8: Another decoding stuff
· Task 9: Left or right?
· Task 10: Make a comment
· Task 11: Can you fix it?
· Task 12: Read it
· Task 13: Spin my head
· Task 14: An exclusive
· Task 15: Binary walk
· Task 16: Darkness
· Task 17: A sounding QR
· Task 18: Dig up the past
· Task 19: Uncrackable!
· Task 20: Small bases
· Task 21: Read the packet
· Conclusion
TryHackMe is an exceptional online platform designed to provide individuals with hands-on cybersecurity learning experiences.
It offers an immersive environment where users can explore various topics, master essential tools, and enhance their practical skills.
One of the remarkable features of TryHackMe is the CTF Collection Vol 1, which serves as an excellent starting point for aspiring CTF enthusiasts. The CTF Collection Vol 1 consists of a curated set of easy challenges that cover some basic skills needed by any beginner CTF player.
Some of the topics covered include base number conversion, image steganography, decoding various encoding schemes, substitution ciphers, OSINT, and many more.
This first collection consists of 20 tasks and offers a progressive learning path, starting from extremely easy beginner-friendly challenges and gradually increasing in difficulty, allowing the players to sharpen their CTF skills at their own pace.
This collection (Vol. 1) as well as the follow-up CTF Collection (Vol. 2) were created by DesKel.
The main objective of this room is to test your CTF skills. Stay calm and Capture The Flag :)
— DesKel
With its intuitive interface, comprehensive resources, and vibrant community, TryHackMe’s CTF Collection Vol 1 serves as an invaluable resource for those seeking to gain practical experience and confidence in beginning their CTF journey without the pressure of a timed CTF competition.
First things first…
Pre-requisites:
- Your OS: A Linux (virtual) machine packed with your favorite hacking tools. I recommend Kali or Parrot OS as your go-to CTF platform.
- Good Music: CTFs are fun and meant to be enjoyed and not stressed about. Head to Spotify and fire up your favorite hacking music playlist!
- Caffeine Up: You need coffee when you code, hack, or play a CTF. Get some coffee and Caffeine Up!
If you are a free TryHackMe user, you only get 1 hour/day access to a Web-based Kali “AttackBox”.
If you are a paid subscriber you get unlimited access to the AttackBox which you can use for the CTF room in this article.
Task 2: What does the base said?
Challenge
Can you decode the following?
VEhNe2p1NTdfZDNjMGQzXzdoM19iNDUzfQ==
Solution
This looks like a Base64 encoded message. To identify this, you typically look for a string of characters consisting of a combination of uppercase and lowercase letters, numbers, the “+” or “/” and usually ends with or is passed with “=” character.
Let’s decode this by using ‘echo’ to pipe the string to the utility ‘base64’ with the parameter to decode (--decode or -d).
$ echo "VEhNe2p1NTdfZDNjMGQzXzdoM19iNDUzfQ==" | base64 -d
THM{ju57_d3c0d3_7h3_b453}Task 3: Meta meta
Challenge
Meta! meta! meta! meta……………………………..
I’m hungry, I need the flag.
Download Task Files: Findme.jpg
Solution
Download the task file “Findme.jpg”.
To access the metadata of images, the best tool to start your analysis with is usually ExifTool. You may need to install it first if you don’t have it on your system.
$ sudo apt update
$ sudo apt install exiftoolBelow is the screenshot of using ExifTool to extract the metadata and the flag for this challenge.
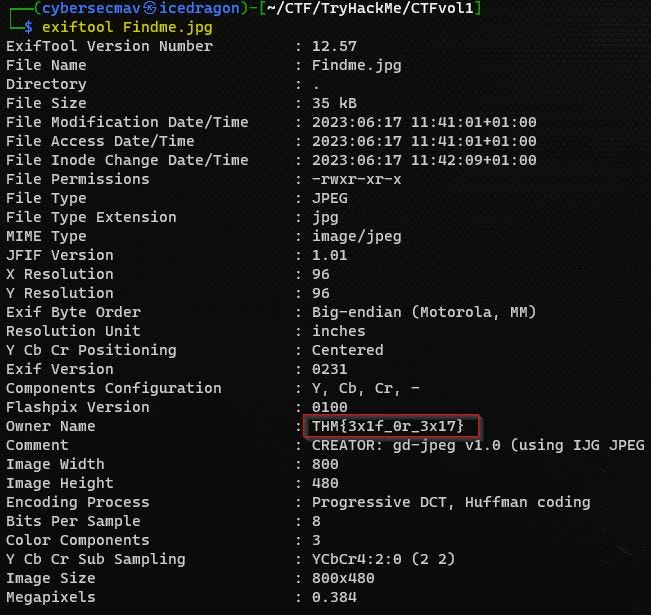
Task 4: Mon, are we going to be okay?
Challenge
Something is hiding. That’s all you need to know.
It is sad. Feed me the flag.
Download Task Files: Extinction.jpg
Solution
Let’s begin by downloading the task file Extinction.jpg.
We begin our usual analysis by first running the ExitTool again (see Task 3), but this revealed nothing hidden in the metadata of the image.
Next is another popular steganography (or stego for short) tool called steghide. If this is not installed by default in your Kali machine, you can install it by following the instructions below:
$ sudo apt update
$ sudo apt install steghideLet’s analyze it for any hidden text with the “info” option:
$ steghide info Extinction.jpg
"Extinction.jpg":
format: jpeg
capacity: 1.3 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "Final_message.txt":
size: 79.0 Byte
encrypted: rijndael-128, cbc
compressed: yesBingo! There seems to be a hidden text file called “Final_message.txt”.
Now we extract the data with the command below. Note that you were not provided with a passphrase so you can hit “Enter” and leave it blank.
$ steghide extract -sf Extinction.jpg
Enter passphrase:
wrote extracted data to "Final_message.txt".
$ cat Final_message.txt
It going to be over soon. Sleep my child.
THM{500n3r_0r_l473r_17_15_0ur_7urn}Task 5: Erm……Magick
Challenge
Huh, where is the flag?
Did you find the flag?
Solution
This one was a bit tricky at first. No downloadable files, nothing to analyze.
For this one, we have to use the hint provided:
“Highlight the text or check the html.”
Either by highlighting the text or inspecting the source code of the page, you will be able to uncover the text.
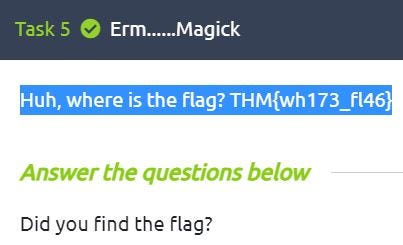
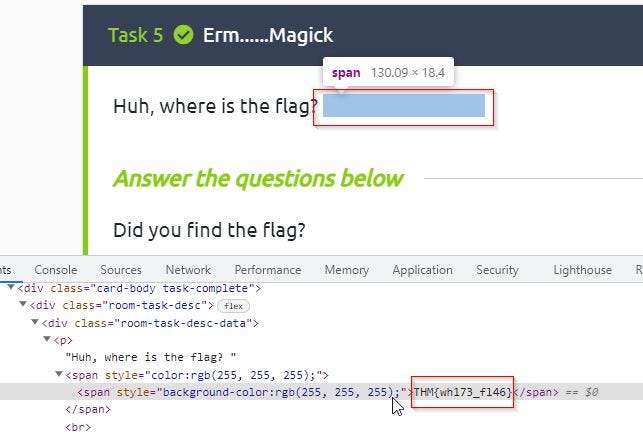
Task 6: Qrrrr
Challenge
Such technology is quite reliable.
More flag, please!
Download Task Files: QR.png
Solution
We begin with downloading the task file QR.png which contains a QR code.
Using your phone or tablet’s camera or QR reader app, point your camera at the image of the QR code once you have opened it up with any image viewer. Getting the flag is easy for this one. See my screenshot from my Android phone.

Task 7: Reverse it or read it?
Challenge
Both work, it’s all up to you.
Found the flag?
Download Task Files: hello.hello
Solution
Download the task file hello.hello which looks like a binary. Let’s verify that first.
$ file hello.hello
hello.hello: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=02900338a56c3c8296f8ef7a8cf5df8699b18696, for GNU/Linux 3.2.0, not strippedIndeed it is a Linux executable file. The challenge description suggests we either try to “reverse engineer” it or read it. Reverse engineering involves using tools such as Ghidra, radare2, Cutter, OllyDBG, x64dbg and GNU’s gdb to analyze the binary.
For this exercise, we will go the easier route to suit a CTF beginner who isn’t familiar with reverse engineering yet. Reading the binary suggests that we could extract the strings within the binary using a tool such as … you guessed it! strings.
Note that we can either pipe the output to a file, to screen or to grep (find) the strings of interest. In this case, we are searching for THM{ and we will ignore the case-sensitivity so it can match either “thm{“ or “THM{“.
$ strings hello.hello | grep -i thm{
THM{345y_f1nd_345y_60}Task 8: Another decoding stuff
Challenge
Can you decode it?
3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L
Oh, Oh, Did you get it?
Solution
This string does not look like Base64 or Base32. We can certainly try and verify that to be sure, using the same process as Task 2.
$ echo "3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L" | base32 -d
base32: invalid input
$ echo "3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L" | base64 -d
ݨ+K-B{}�ˤq)I����(%)(nDo we know of more possible Base encoding schemes?
with a little research (ehm… Googling!) we stumble upon Base58.
$ echo "3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L" | base58 -d
THM{17_h45_l3553r_l3773r5}That seemed like a bit of brute-forcing, didn’t it?
If you are planning on doing more CTFs in the future, the more you automate and cut the number of manual attempts down the quicker and more efficient you will be.
Being a Maverick, this screams for a simple bash script to feed this string through as many encoding schemes as we can to save us time. Bash scripting was chosen to keep it simple.
#!/bin/bash
# Read input string from command prompt
read -p "Enter the encoded string: " encoded_string
# Display the original string
echo
echo "Original String: $encoded_string"
echo
# Decode using base32
decoded_base32=$(echo "$encoded_string" | base32 -d)
if [[ -n "$decoded_base32" ]]; then
echo "Decoded (Base32): $decoded_base32"
fi
echo
# Decode using base58
decoded_base58=$(echo "$encoded_string" | base58 -d)
if [[ -n "$decoded_base58" ]]; then
echo "Decoded (Base58): $decoded_base58"
fi
echo
# Decode using base64
decoded_base64=$(echo "$encoded_string" | base64 -d)
if [[ -n "$decoded_base64" ]]; then
echo "Decoded (Base64): $decoded_base64"
fi
echoSee the output of the shell script base-decoder.sh below:
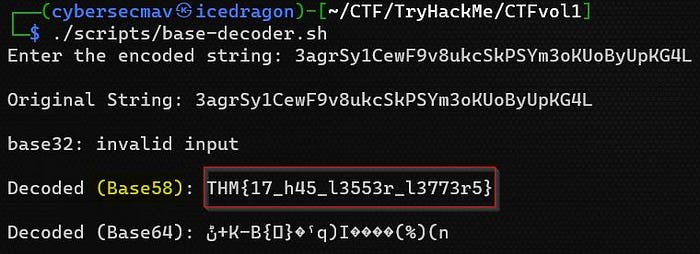
Task 9: Left or right?
Challenge
Left, right, left, right… Rot 13 is too mainstream. Solve this
MAF{atbe_max_vtxltk}
What did you get?
Solution
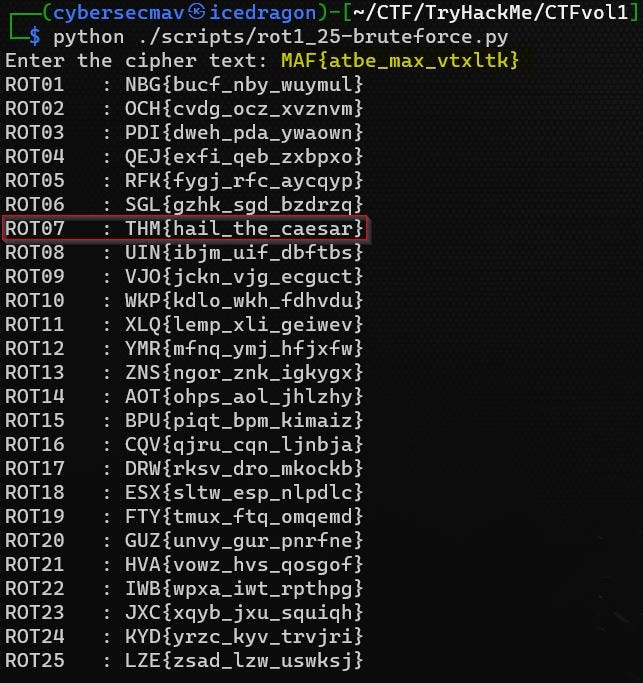
This challenge suggests that the very common ROT13 is not the correct one. ROT13 is a simple letter substitution cipher also known as Caesar Cipher. Most likely the coded string used a variation of ROT-N where N is not 13.
ROT26 is not used for brute forcing ROT cipher because it’s like trying to unlock a door with the same key but turning it twice as much and wondering why it’s not opening.
Method 1:
Use an online decoder such as https://www.dcode.fr/rot-cipher.
Method 2:
If you want to be an efficient CTF player and a Cyber Maverick, you will need to get used to scripting in languages such as Python.
This task can be automated and you will be able to add that script to your bag of tools for future CTFs.
Below is a simple Python script to brute-force ROT1 all the way to ROT25 decryption for a given string. We saved this to rot1_25-bruteforce.py.
# This is a ROT1 to ROT25 brute-force rotation script.
# You enter the cipher text and the script will output all potential outputs in every ROT scheme
def rot_decode(cipher_text):
# Loop over all possible ROT values (1 to 25)
for rot in range(1, 26):
decoded_text = ""
# Loop over each character in the cipher text
for c in cipher_text:
# Check if the character is a letter
if c.isalpha():
# Determine the ASCII offset based on whether the letter is uppercase or lowercase
if c.isupper():
ascii_offset = 65
else:
ascii_offset = 97
# Convert the character to its ASCII code
c_code = ord(c)
# Determine the new ASCII code by applying the ROT value
new_c_code = (c_code - ascii_offset + rot) % 26 + ascii_offset
# Convert the new ASCII code back to a character
new_c = chr(new_c_code)
decoded_text += new_c
else:
# If the character is not a letter, add it to the decoded text as is
decoded_text += c
# Print the decoded text for the current ROT value
print(f"ROT{rot:02d} : {decoded_text}")
# Prompt the user for input
cipher_text = input("Enter the cipher text: ")
rot_decode(cipher_text)Running the script above should contain the flag in one of the rotations.
Task 10: Make a comment
Challenge
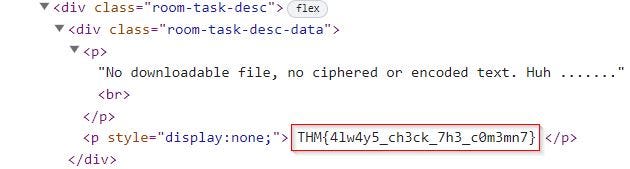
No downloadable file, no ciphered or encoded text. Huh …….
I’m hungry now… I need the flag
Solution
Our initial suspicion was to check the HTML source code. It is a very common CTF challenge, especially the very easy challenges.
As it turns out, we were correct about our assumption. Checking the hint also gets you there quicker if you are stuck.
Task 11: Can you fix it?
Challenge
I accidentally messed up with this PNG file. Can you help me fix it?
Thanks, ^^
What is the content?
Download Task File: spoil.png
Solution
We downloaded the task file spoil.png which seems like a corrupted PNG image.
This challenge is one of the most common ones in beginner CTF challenges. The level of corruption depends on the complexity of the challenge.
When dealing with JPG or PNG images there are a few things to be checked.
If the image is not corrupted you can look straight away for any steganography using tools such as exiftool and steghide for starters.
However, if we are dealing with a corrupted image, one of the first tools to use is the Linux command “file”. This is a handy utility that helps in identifying the file types regardless of their extensions based on a few checks it runs. One of those checks is the Magic Byte which is a way of quickly identifying common file formats.
$ file spoil.png
spoil.png: data
For a PNG image, the header must always start with “.PNG….” or the hex values “0x89 0x50 0x4E 0x47 0x0D 0x0A 0x1A 0x0A”.
We are spoiled for choice when it comes to using a Hex editor to inspect a binary file or image and verify the Magic. Some choices include:
Let’s verify the PNG header starts with “.PNG” or “89 50 4E 47”. Seems like our file has an incorrect header:

The file starts with “#3D_” which we should replace with “.PNG”.
Let’s replace that with the correct header values using the GUI Hex editor “bless”.

Using file command again we can verify if this has worked:
$ file spoil.png
spoil.png: PNG image data, 800 x 800, 8-bit/color RGBA, non-interlacedExcellent! Seems like we have fixed it and di not need to continue our analysis of the file further. Opening the file now will reveal the flag:

Task 12: Read it
Challenge
Some hidden flag inside the Tryhackme social account.
Did you find the hidden flag?
Solution
This task requires some social media OSINT.
We begin with a query such as the Google search below:
- “Task 12” + “flag”
This yields some pages with a CTF write-up or a walkthrough which is not what we want. That is just too easy and it’s kind of cheating!
A few results down the list we see a Reddit discussion which looked interesting. We also confirm this by checking the hint for the task.
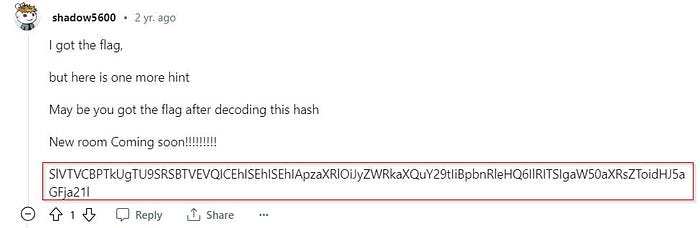
This does seem like a buried encoded string in the middle of a thread.
We would try a ROT or simple substitution cipher brute-force however, if you pay close attention to the string you would notice the mixing of upper and lowercase letters which could indicate a Base encoding (16, 32, 58, 64 etc..).
Remember our earlier bash script in Task 8? This is where re-use and automation come in handy!
$ ./scripts/base-decoder.sh
Enter the encoded string: SlVTVCBPTkUgTU9SRSBTVEVQICEhISEhISEhIApzaXRlOiJyZWRkaXQuY29tIiBpbnRleHQ6IlRITSIgaW50aXRsZToidHJ5aGFja21l
Original String: SlVTVCBPTkUgTU9SRSBTVEVQICEhISEhISEhIApzaXRlOiJyZWRkaXQuY29tIiBpbnRleHQ6IlRITSIgaW50aXRsZToidHJ5aGFja21l
base32: invalid input
subsection not found
Decoded (Base64): JUST ONE MORE STEP !!!!!!!!
site:"reddit.com" intext:"THM" intitle:"tryhackmeIt was a Base64 encoding and we have a very encouraging result.
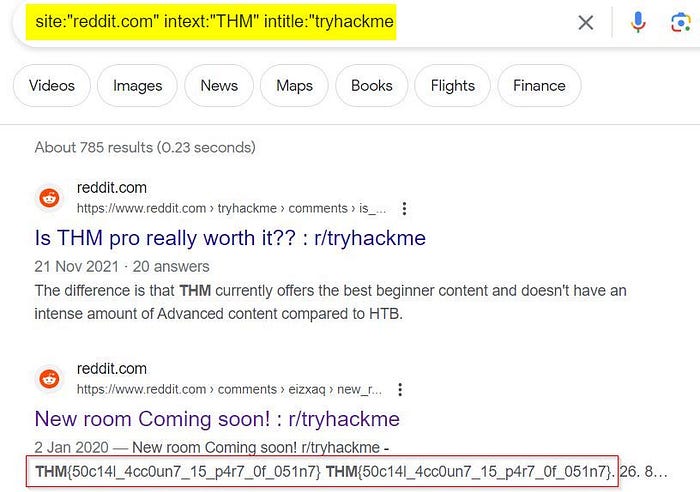
Let’s take to Google and try out that search:
site:”reddit.com” intext:”THM” intitle:”tryhackme
We had again a few results and the second result seems to have our flag.
Task 13: Spin my head
Challenge
What is this?
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>++++++++++++++. — — — — — — .+++++.>+++++++++++++++++++++++.<<++++++++++++++++++.>> — — — — — — — — — -. — — — — -.++++++++++++++.++++++++++++.<++++++++++++++++++.+++++++++.<+++.+.> — — .>++++.
Can you decode it?
Solution
Now this looks like some interesting encoding. Certainly not the usual Base encoding scheme.
I have not come across this one before. I suspected a binary encoding but we seem to have 8 characters or more, not just two for a binary 1 and 0.
For full disclosure I had to use the hint for this challenge, which is fine and it’s all part of the learning process.
The hint indicated that this is an encoding known as “binaryfuck” or BrainFuck.
At this point, we head toward our favorite online decoder dCode.
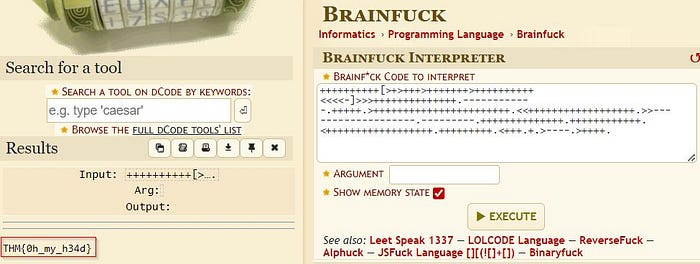
Task 14: An exclusive
Challenge
Exclusive strings for everyone!
S1: 44585d6b2368737c65252166234f20626d
S2: 1010101010101010101010101010101010
Did you crack it? Feed me now!
Solution
We have two strings, one being Hex and the other in Binary. The challenge text suggests that they want us to go down the Exclusive OR (XOR) route.
Before investing a lot of energy you can always confirm this with the provided hint whenever available.
One way of solving this is by using an Online XOR Calculator.
String 1: 44585d6b2368737c65252166234f20626d
String 2: 1010101010101010101010101010101010
Result in:
Binary: 101010001001000010011010111101100110011011110000110001101101100011101010011010100110001011101100011001101011111001100000111001001111101
Hex:
54484D7B3378636C75353176335F30727D
ASCII: }r0_3v15ulcx3{MHT
Our ASCII output from the online calculator looks like a flag but seems reversed. Easy to take care of it in Linux by using a command to reverse the string. You guessed it, it’s called “rev”!
$ echo "}r0_3v15ulcx3{MHT" | rev
THM{3xclu51v3_0r}We are Cyber Mavericks so let’s explore another way to solve it ourselves without using an online calculator:
$ python -c "s1 = bytes.fromhex('44585d6b2368737c65252166234f20626d'); s2 = bytes.fromhex('1010101010101010101010101010101010'); print(''.join(chr(a ^ b) for a, b in zip(s1, s2)))"
THM{3xclu51v3_0r} print(‘’.join(chr(a ^ b) for a, b in zip(s1, s2)))
Performs the XOR operation on the corresponding bytes of s1 and s2. It iterates over each pair of bytes using zip(s1, s2) and applies the XOR operation using the bitwise XOR operator ^.
‘’.join(chr(a ^ b) for a, b in zip(s1, s2))
Converts each XORed value back to its corresponding ASCII character using the chr()function. It then joins all the characters together to form a single string.
Again, let’s convert it into a re-usable script for any future CTFs, and let’s be more efficient by asking the script to prompt us for any changing strings instead of hard-coding those values:
# Prompt the user to enter the first string
s1_input = input("Enter the first string: ")
# Prompt the user to enter the second string
s2_input = input("Enter the second string: ")
# Convert the input strings to bytes
s1 = bytes.fromhex(s1_input)
s2 = bytes.fromhex(s2_input)
# Perform the XOR operation on the corresponding bytes
xor_result = bytes(a ^ b for a, b in zip(s1, s2))
# Convert the XOR result to ASCII and print
ascii_result = xor_result.decode('ascii')
print("XOR result (ASCII):", ascii_result)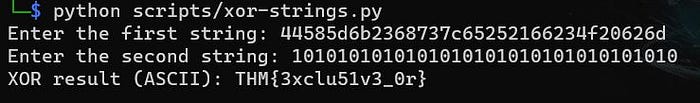
Task 15: Binary walk
Challenge
Please exfiltrate my file :)
Flag! Flag! Flag!
Download Task File: hell.jpg
Solution
As the name of the challenge suggests, we need to inspect the binary file or image hellp.jpg with a tool named “binwalk”. Binwalk is a popular tool used for analyzing, reverse engineering, and extracting not only firmware images but also hidden elements in binary files. It is frequently used during CTF forensics or steganography challenges to extract hidden text or files inside files such as images.
Let’s check if our image hell.jpg contains any sort of hidden data by running binwalk without additional options.
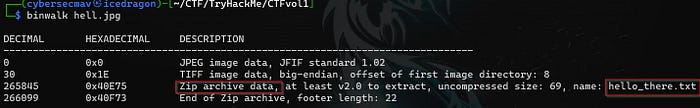
We found evidence of information hiding (stego). The indication is that there is an archive containing the hello_there.txt file. Time for extraction.
$ binwalk -e hell.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.02
30 0x1E TIFF image data, big-endian, offset of first image directory: 8
265845 0x40E75 Zip archive data, at least v2.0 to extract, uncompressed size: 69, name: hello_there.txt
266099 0x40F73 End of Zip archive, footer length: 22
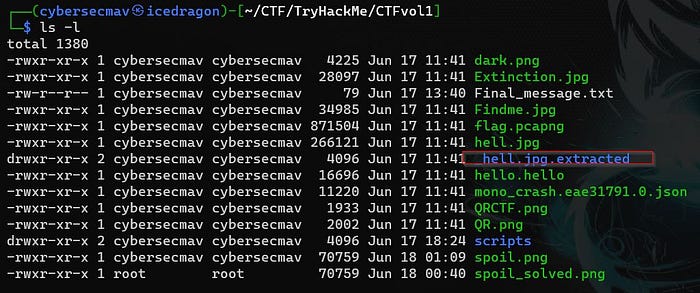
We see above that by using binwalk’s extract option (-e) we have a new folder named _hell.jpg.extracted which we should inspect next.
$ cd _hell.jpg.extracted/
$ ls -la
total 16
drwxr-xr-x 2 cybersecmav cybersecmav 4096 Jun 17 11:41 .
drwxr-xr-x 4 cybersecmav cybersecmav 4096 Jun 19 22:35 ..
-rwxr-xr-x 1 cybersecmav cybersecmav 276 Jun 17 11:41 40E75.zip
$ unzip 40E75.zip
Archive: 40E75.zip
replace hello_there.txt? [y]es, [n]o, [A]ll, [N]one, [r]ename: y
inflating: hello_there.txt
$ ls
40E75.zip hello_there.txt
$ rm hello_there.txt
$ unzip 40E75.zip
Archive: 40E75.zip
inflating: hello_there.txt
$ cat hello_there.txt
Thank you for extracting me, you are the best!
THM{y0u_w4lk_m3_0u7}That is how we uncovered the simple stego within a binwalk’s extract option.
Practice using binwalk a lot. It comes in handy very often in CTF challenges.
See the tutorial in the Resources section at the bottom of this article.
Task 16: Darkness
Challenge
There is something lurking in the dark.
What does the flag said?
Download Task File: dark.png
Solution
Once you have downloaded and inspected it with an image viewer you see nothing but….darkness!
We run through the usual checklist for analyzing the image file for hidden data and signs of steganography:
$ exiftool dark.png
$ steghide extract -sf dark.png
$ binwalk dark.png
$ strings dark.png | lessNone of them yield any useful results.
If you recall the name of the challenge, there is a suspicion that we are dealing with an image that has been “darkened” and that the hidden text may be visible if we manipulate the colors, greyscale, opacity, etc.
I have opened the image in Greenshot which is a great screenshotting tool on Windows. I have tried the “Inversion” effect which didn’t do the trick.
At this point, we decided to take a different approach and explore the image using a powerful steganography tool called StegSolve.
StegSolve allows us to manipulate various color channels and bit planes of the image, potentially revealing hidden information.
After opening the image in StegSolve, we started experimenting with different color and bit plane combinations. Lo and behold, when we adjusted the color planes, specifically the blue channel, a faint pattern started to emerge. It seemed that the hidden text was cleverly embedded within the image, visible only through this manipulation.
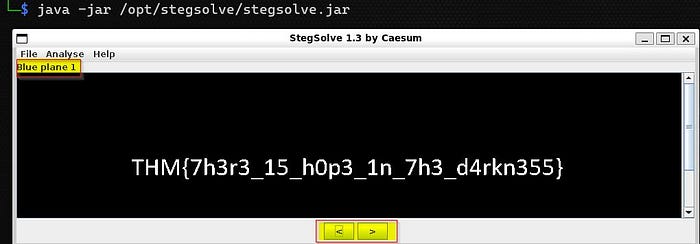
This experience served as a powerful reminder of the importance of understanding image composition and employing specialized tools like StegSolve to uncover hidden secrets within visual content.
Task 17: A sounding QR
Challenge
How good is your listening skill?
P/S: The flag formatted as THM{Listened Flag}, the flag should be in All CAPS
Download Task File: QRCTF.png
Solution
I have downloaded the QRCTF.png image.

This takes you to the following to the following URL:
The flag value is spoken at the start of the track. Easy peasy right?
Flag: THM{SOUNDINGQR}
Task 18: Dig up the past
Challenge
Sometimes we need a ‘machine’ to dig the past.
Targetted website: https://www.embeddedhacker.com/
Targetted time: 2 January 2020
Solution
The Internet Archive website WayBackMachine is a great resource for digging up previous versions of most websites.
We begin our search by browsing to it and inputting the URL we want to find a historic version for. URL: https://www.embeddedhacker.com/
We then select the date we are interested in, which is Jan 2nd, 2020.
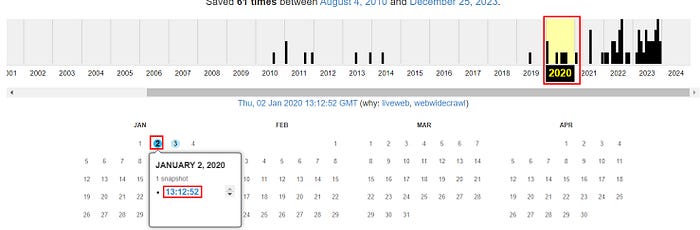
We open up that version and see the contents of the page as it was snapshotted and archived.

Flag: THM{ch3ck_th3_h4ckb4ck}
Task 19: Uncrackable!
Challenge
Can you solve the following? By the way, I lost the key. Sorry >.<
MYKAHODTQ{RVG_YVGGK_FAL_WXF}
Flag format: TRYHACKME{FLAG IN ALL CAP}
Solution
This encoded flag looks like it may have been encoded using a simple substitution cipher such as Caesar Cipher, which is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet.
The most common cipher is ROT13 (shift by 13 places). So it is a good first step to try the obvious first. For that, we can use several tools or websites to convert text to ROT13. Let’s head to CyberChef and test this out.
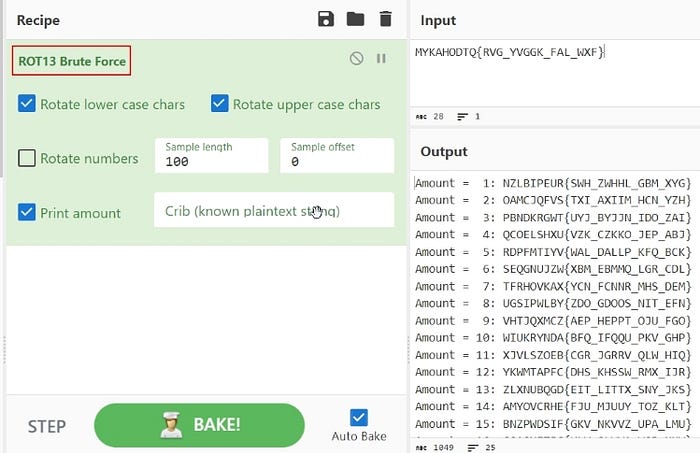
We had no luck with ROT after using the brute-forcer on CyberChef. 😞Let’s explore another great website called dcode.fr and identify the cipher
The code website was able to identify this as a Vigenere Cipher which is a common variation on Caesar’s substitution cipher.
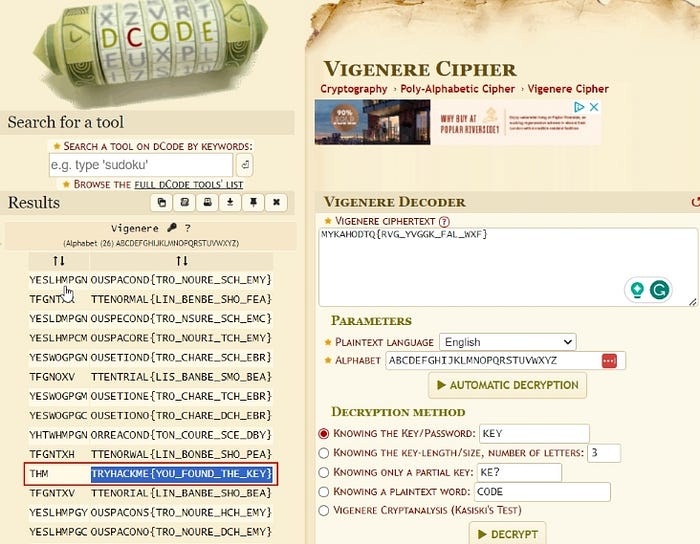
The Vigenere Cipher Decoder on dcode.fr was able to successfully decode the string as seen in the figure above. 😎
Flag: TRYHACKME{YOU_FOUND_THE_KEY}
Task 20: Small bases
Challenge
Decode the following text.
581695969015253365094191591547859387620042736036246486373595515576333693
Solution
The challenge name suggests that this is a Base-encoded message.
Base encoding is a scheme that translates ASCII text into a format that is transmission-friendly for binary data. This is particularly useful in processing by text-based systems like web and mail systems.
There exist many Base encoding systems such as Base16, Base32, and Base64. Base64 is the most popular scheme in use for web-based systems.
There is a common misconception among many technology enthusiasts and developers that Base encoding somehow encrypts, protects, or obfuscates data when sent in the clear.
This is a dangerous misunderstanding, as Base encoding, along with all forms of encoding, is reversible. Therefore, it does not protect any sensitive data or credentials that are converted and transmitted using Base-xx.
Back to the challenge at hand, I have first attempted a Base64 decoding due to its popularity and wide use. I have also tried a few different Base conversions and none of them seemed to work. Time to use the Hint provided by TryHackMe (no shame in that!).
Hint: dec -> hex -> ascii
Alright, I was going down a rabbit hole and this tip saved my effort of brute forcing a few more obscure BaseXX encoding schemes.
Let’s use a web-based converter first.
A) From Decimal to Hex
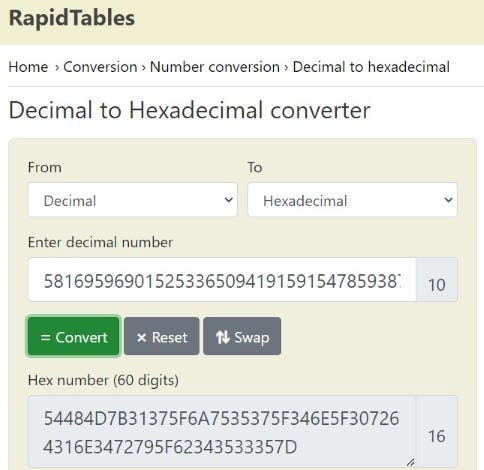
B) From Hex to Text
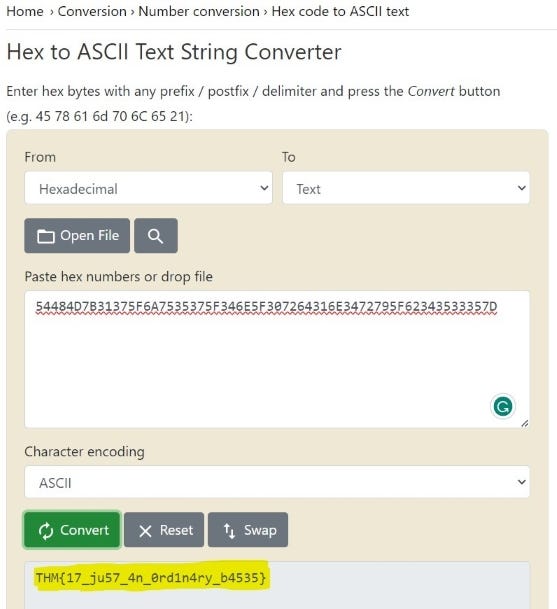
And there you have the flag!
But wait, We are Mavericks aren’t we? We aspire to be as fast, efficient and as leet as possible while we learn and solve challenges.
We have to attempt a command-line conversion and rely less on external tools or websites. It is quicker and much more efficient.
There are a dozen ways of doing this on Linux including using Python.
I will leave you with one method and let you discover the alternative ways to do this on your own 😄
Please ensure you have installed the xxd and bc tools beforehand with:
sudo apt install xxd
echo "ibase=10;obase=16;581695969015253365094191591547859387620042736036246486373595515576333693" | bc | xxd -r -pIn this example above we take a decimal number, convert it to hexadecimal using bc, and then convert the hexadecimal to ASCII using xxd.
bc: a calculator utility that interprets the mathematical expression in Hex.
- ibase=10: sets the input base to decimal.
- obase=16: sets the output base to hexadecimal.
xxd: is a utility that converts data in hexadecimal representation to binary and vice versa.
- -r: Reverse operation. Converts Hex to Binary
- -p: Plain hexdump style without line number display.
Note: originally I opted to use printf function. However, the Bash printf was unable to directly handle large decimal numbers that exceed a certain range
Flag: THM{17_ju57_4n_0rd1n4ry_b4535}
Task 21: Read the packet
Challenge
I just hacked my neighbor’s WiFi and tried to capture some packets.
He must be up to no good. Help me find it.
Download Task Files: flag.pcapng
Solution
Packet Analysis is one of my favorite tasks during CTFs. I like the rawness of the data and being closer to the wire during investigations and analysis.
For the sake of brevity, I will not get into my usual process of handling a packet capture file and the initial analysis I do to gain an understanding of the protocol statistics, conversations, and protocol hierarchy in a packet capture. I will keep the solution simple.
In this scenario, we look for the common protocols that contain data.
An assumption is made that our neighbor will be doing some web browsing so we start our analysis by zooming in on HTTP protocol communications.
We have found a total of 12 HTTP packets (6 requests and 6 responses).
Ignoring the OCSP packets (Online Certificate Status Protocol), we are left with a single HTTP request for /flag.txt and a response that contains our flag. Easy day at the office 😉
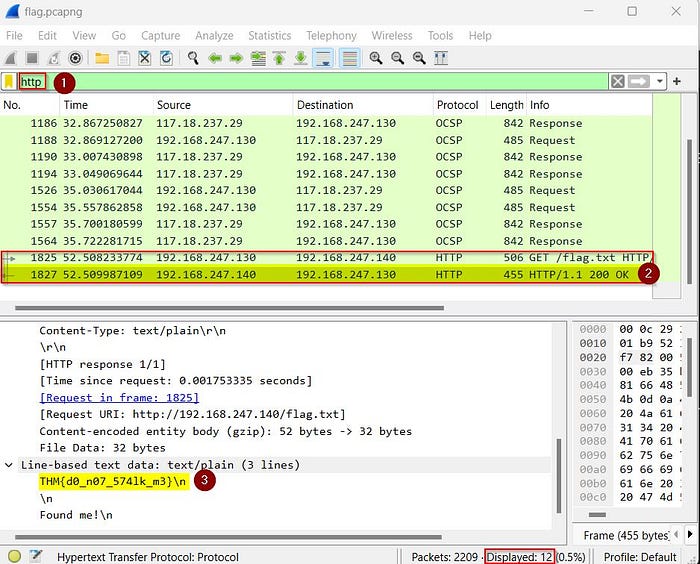
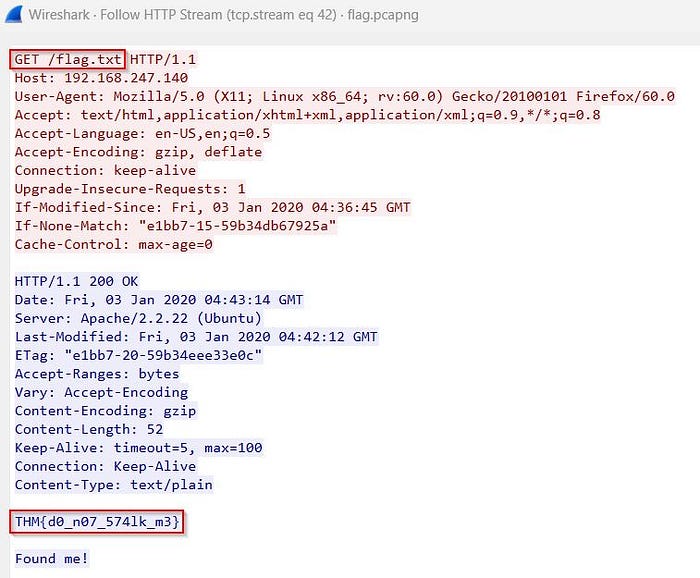
Alternatively, you can click the first HTTP request and use the following option to follow the packet in an easier format:
Analyze → Follow → HTTP Stream
Conclusion
This was a quick and fun introduction to solving mini-challenges, meant to boost your skills for tackling some common CTF tasks.
I have added a bit more details in places without assuming you’re already a pro at CTF or Linux.
I hope you were able to follow along. More importantly, I hope you have found them fun and educational.
I hope you followed along and, more importantly, had fun and learned something. Now, take that new interest in CTF challenges and keep going with your journey. There’s a lot more to learn!
I’ve listed some resources below that might be useful as you start your journey into CTFs.
What’s next?
- TryHackMe: CTF Collection Vol. 2 (Official Website)
- TryHackMe CTF Collection Vol. 2 (My Write-up)
- Tips & CTFs for beginners by HTB
- Introduction to CTFs by HTB


