Member-only story
Vanilla PowerShell Reverse Shell Using ICMP
After recently creating a PowerShell reverse shell using WebSockets, I figured I could push this subject a bit further. Messing around with packets, hiding data and firing up WireShark, it has been a while!
In this article I want to walk you through how I created a reverse shell in vanilla PowerShell which communicates using ICMP Echo Request messages (Internet Control Message Protocol, a.k.a. ping) over IPv4. It communicates directly between devices at the network layer, utilizing IP for transmission. I’m still working on setting up a decent repository, but wanted to give a sneak preview at how data can be embedded in ICMP traffic. My goal? Creating a tool which can test the detection and response of defensive measures like NDR and XDR solutions!
Not a member? Read this article for free on my site.

Before reviewing how this works, lets first take a look at the ICMP proof of concept shell in action:
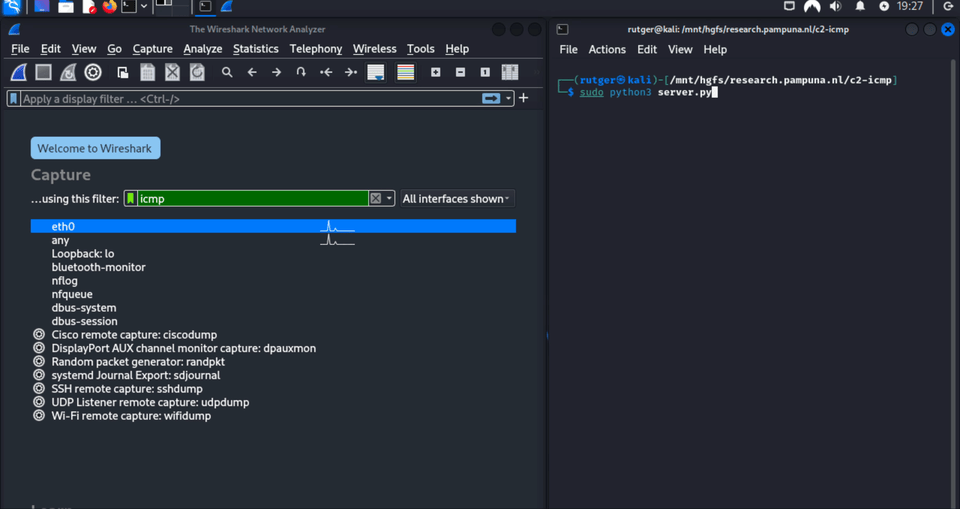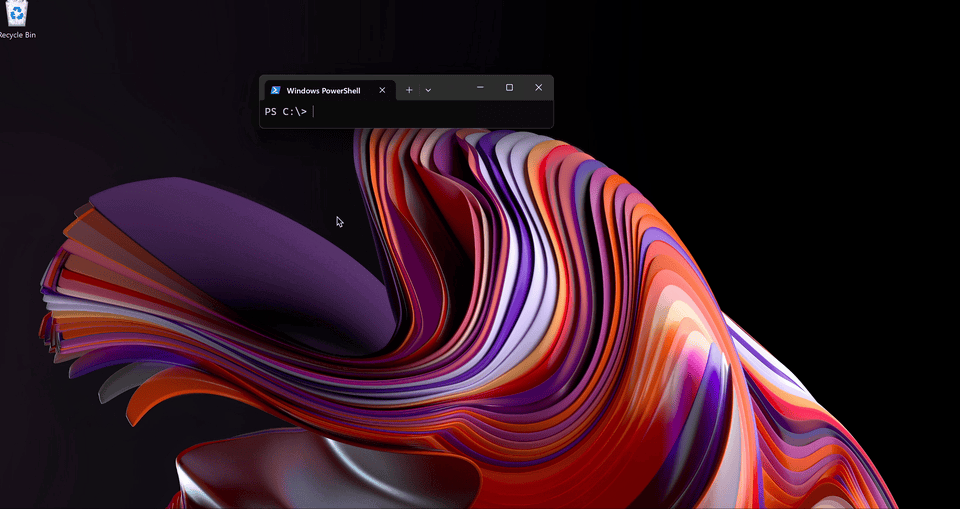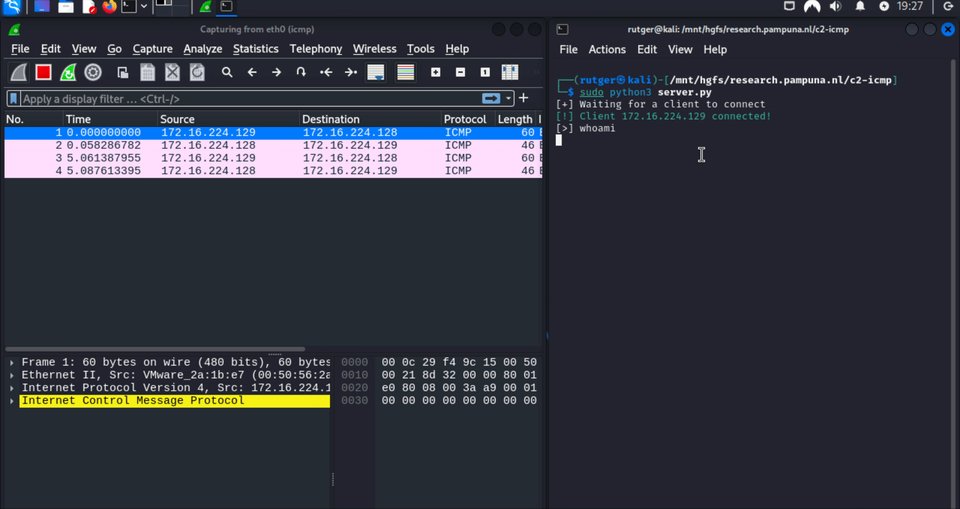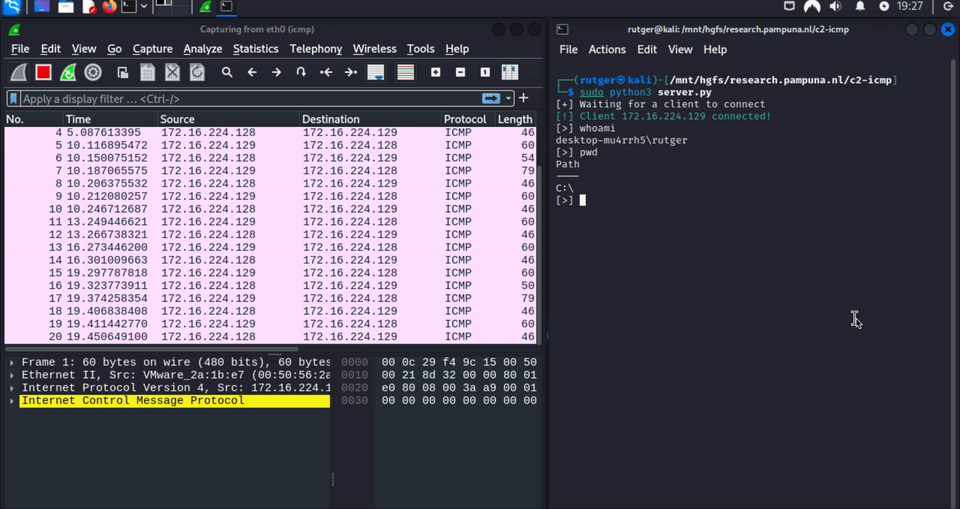
Note that this article is written for educational purposes and is intended only for legal penetration testing and red teaming activities, where explicit permission has been granted. For more information, refer to the disclaimer at the end of this article.
Visualizing The Concept
First, I would like to visualize a simplified overview of the way the client communicates with the server before I start explaining how the script works. Being a reverse shell, the client should initiate the connection.
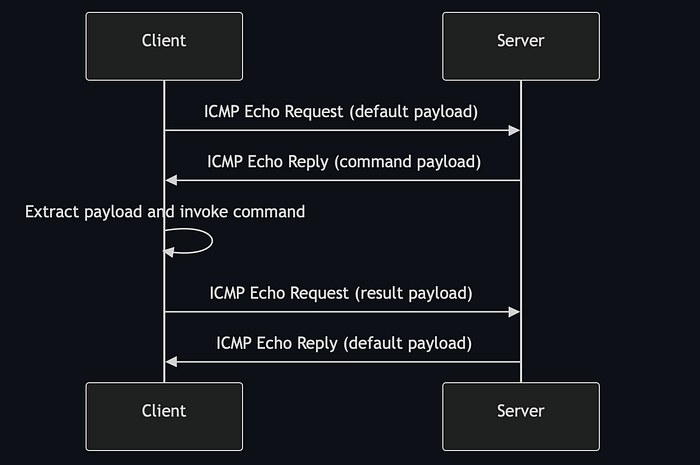
The above flow illustrate why it’s important to watch for patterns in traffic. Even when ping packets look legitimate, monitoring behavior over longer periods of time can help detecting tactics like these!
Preparing The Host
First things first. Before I could start testing, I had to disable ICMP echo replies on my host. If this isn’t done, the operating system will respond earlier than the server. This…

